UPDATE: BigNox contacted us and said that they “contacted cybersecurity firm ESET to determine the root cause of the issue,” and at this point “fixed all issues”
ESET has released an update to the article stating that hackers have infected the android NoxPlayer emulator with malware, and we are also adding following information: “BigNox stated that they sent the latest files to the update server for NoxPlayer and that when launching NoxPlayer now will start a scan of application files previously installed on users’ computers”.
The GridinSoft Blog is not responsible for the accuracy of the information provided by BigNox.
ESET experts discovered an attack on the supply chain, during which an unknown hack group compromised the developers of the popular Android emulator NoxPlayer and infected it with the malware code.
NoxPlayer is free and designed to emulate Android applications on Windows or macOS computers. The emulator is developed by the Hong Kong company BigNox and is used by more than 150,000,000 users in 150 countries.
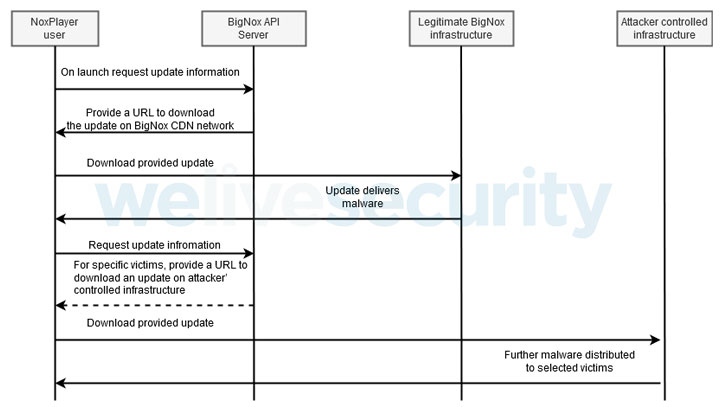
The researchers write that they discovered an attack targeting BigNox on January 25, 2021.
According to them, the attackers compromised one of the company’s official APIs (api.bignox.com), as well as file hosting servers (res06.bignox.com). Using the obtained access, the hackers “worked” with the URL address to download the updates and, as a result, distributed malware among NoxPlayer users.
The following threats were distributed through NoxPlayer. A previously unknown malware that allows tracking victims and that is also capable of executing commands received from the command and control server, deleting files, downloading and uploading files, and so on. The other two malware were already known to experts: they were variations of Gh0st RAT (with keylogger capabilities) and PoisonIvy RAT.
While analysts believe the attackers have had access to BigNox’s servers since at least September 2020, the hackers did not attack the company’s entire sizable user base, but instead focused their efforts on specific machines. Based on this, the experts conclude that they have discovered a narrowly targeted attack aimed at infecting a certain class of users. Therefore, so far, only five people from Taiwan, Hong Kong and Sri Lanka have been identified as affected by the infected version of NoxPlayer.
The relationship and similarities noted by ESET experts are explained by the fact that all three malwares that were deployed through the NoxPlayer update are very similar to another malware that was used during the hacking of the website of the Myanmar presidential administration (2018) and the University of Hong Kong (2020).
Let me remind you about the fact that new worm for Android spreads rapidly via WhatsApp.