Cybercriminals used stealthy malware to create a botnet of 400,000 proxy servers. Although the company providing the proxy services claims that users voluntarily provided their devices, experts believe otherwise.
A botnet of 400,000 proxy servers
Cybersecurity researchers recently discovered a botnet with more than 400,000 existing proxy nodes. At first glance, the attackers appear as a legitimate company that offers proxy services. However, such concepts as crooks and honesty are incompatible, as the researchers have proven once again. There is a fact that attackers covertly install malware that introduces proxy capabilities on the infected device.
During the installation of the proxy client, the malware sends specific parameters that are also sent to the management and control server. It continuously collects some information about the infected system, such as process monitoring, CPU usage, RAM usage, and battery status. This is done to optimize performance and responsiveness. However, this is not the only case related to the detected payload. Researchers also tie this service to the malware family called AdLoad, that targets macOS. It is a rare occurrence to see cross-platform malware, but thanks to the choice of Golang as a programming language, it is possible for this tricky proxy.
Well Legal, But Actually Illegal
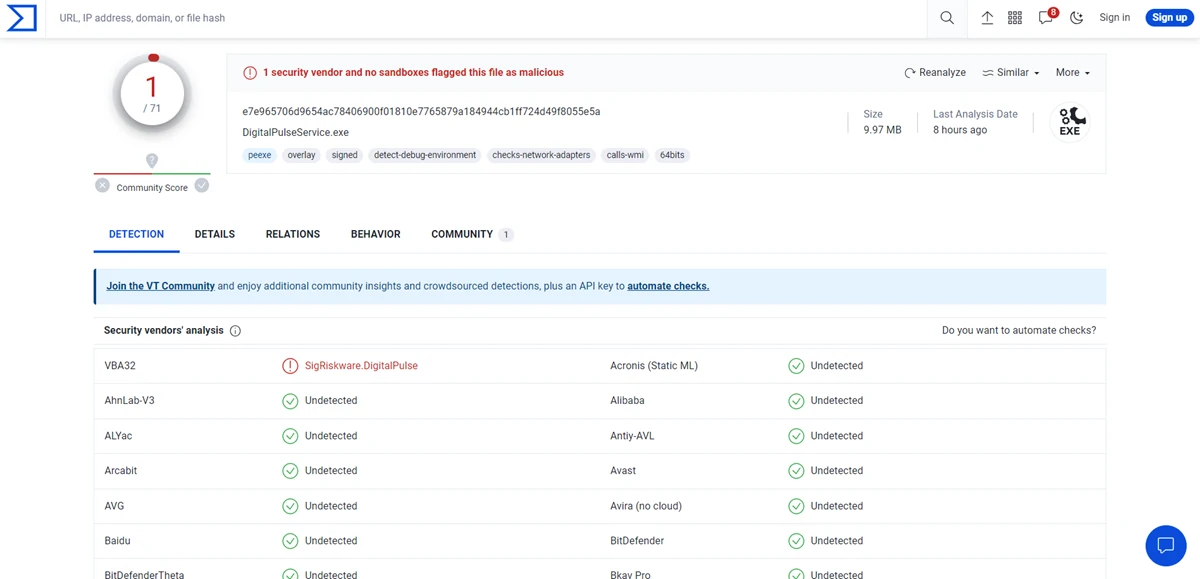
As I wrote above, scammers illegally distribute software that turns the victim’s device into a proxy server. However, things are not so clear-cut here. Although the site states that users provide their devices voluntarily, no notifications or windows are displayed to the user to accept or decline. Nevertheless, the organization that offers resident proxy services is legitimate, and the application has a valid digital signature. Consequently, Windows antivirus tools do not react to it in any way.
On the other hand, most of the time, macOS detects samples of this software. In addition, the site that provides proxy services rewards users who have provided their device as a proxy server. But since the attackers organize the entire process, they get all the profits. It is not surprising they have not passed such a scheme.
Spreading methods and impact
Spreading methods is yet another slippery place there. As I mentioned above, the software part that makes the infected system act as a proxy node is inside of the client installation file. You give it a go – and your system becomes yet another element of this 400,000 botnet. However, things are not over with these trojanized installers.
The attackers know many people disable their antivirus software when downloading and installing pirated software. So, by this action, people essentially give the attackers a green light to install malware on their computers. Cracked software can be downloaded from various sources, including torrent websites, file-sharing sites, and even legitimate software download sites. The malware is often hidden in the software installer or in the cracks or keygens that are used to activate pirated software. Apart from pirate sites, the primary source of this malware is advertising. Sometimes unscrupulous authors of freeware programs accidentally or intentionally allow their product to be used as a delivery method.
How to Avoid Sketchy Proxies & Malware?
Stay away from using p2p software sharing sites. Torrent trackers are a breeding ground for malware. If you think that repack authors are selfless, you’re mistaken. If you want to avoid consciously paying the application developer for his labor, you will have to pay the repacker unknowingly. However, the price is too high and can range from leaking your data to irretrievably wiping all your information. So, avoid downloading pirated software and running executables from untrustworthy sources.
Protecting your privacy is essential to using only reputable proxy servers with trustworthy offers. Here are some tips for choosing a reputable proxy server:
- Read reviews from other users. This is a great way to get an idea of the quality of service you can expect from a particular proxy server provider.
- Please ensure the proxy server provider has a good reputation. You can read online reviews or by looking for accreditations from reputable organizations to check it.
- Ask about the proxy server provider’s security features. Make sure they offer features like encryption and authentication to protect your data.
- Only use proxy servers that are paid for. Free proxy servers are often unreliable and can be used to steal your data.
Use anti-malware software as a preventive measure. Crooks can use malware to steal your personal information, track your online activity, or take control of your computer and join it to the botnet. Reliable anti-malware software can detect and remove malware before it can harm your computer.
Mitigation
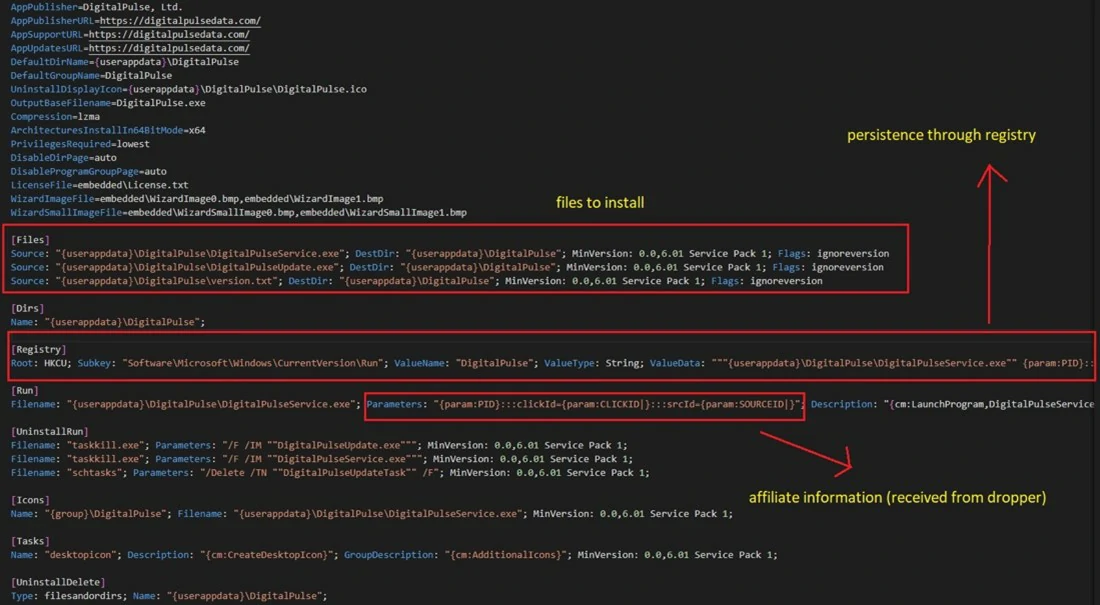
The main signs of proxyware infection are Internet speed degradation and frequent communication with unknown IPs or domains. You should remove the “Digital Pulse” executable found at “%AppData%\” and the Registry key on “HKCU\Software\Microsoft\Windows\CurrentVersion\Run\,” as well as the scheduled task called “DigitalPulseUpdateTask“. That’s it when it comes to removing this threat, but I’d recommend protecting yourself against further cases as well.