Netscout warns that using of the DTLS vector allows hackers to amplify DDoS attacks by 37 times. The researchers found that criminals are using a relatively new vector for amplifying DDoS attacks: the Datagram Transport Layer Security (DTLS) protocol, which provides connection security for protocols using datagrams. DTLS, like other UDP-based protocols, is susceptible to… Continue reading DTLS can amplify DDoS by 37 times
Tag: DDoS
REvil spokesman boasts that hackers have access to ballistic missile launch systems
A Revil representative under the pseudonym Unknown, claims that the hackers, partners in the use of malware, have access to ballistic missile launch systems. Cybercriminal group REvil operates on the RaaS ransomware-as-a-service business model, in which attackers offer malware to partners who use it to block devices and encrypt organizations’ data. A REvil spokesperson under… Continue reading REvil spokesman boasts that hackers have access to ballistic missile launch systems
Google revealed the most powerful DDoS attack in history
This week, the Google Cloud team talked about a previously unknown DDoS attack that targeted a Google service back in September 2017 and peaked at 2.54 TB/sec, making it the most powerful recorded attack in history. Soon, analysts from the Google Threat Analysis Group (TAG) published their report on the incident, in which they said… Continue reading Google revealed the most powerful DDoS attack in history
Lucifer malware uses many exploits, is engaged in mining and DDoS attacks
Palo Alto Networks experts have prepared a report on Lucifer malware, which uses many exploits and, according to experts, “wreaks havoc” on Windows hosts. It is noted that the authors of the malware themselves named their brainchild Satan DDoS, but information security experts call it Lucifer to distinguish it from the Satan cryptographer. The Lucifer… Continue reading Lucifer malware uses many exploits, is engaged in mining and DDoS attacks
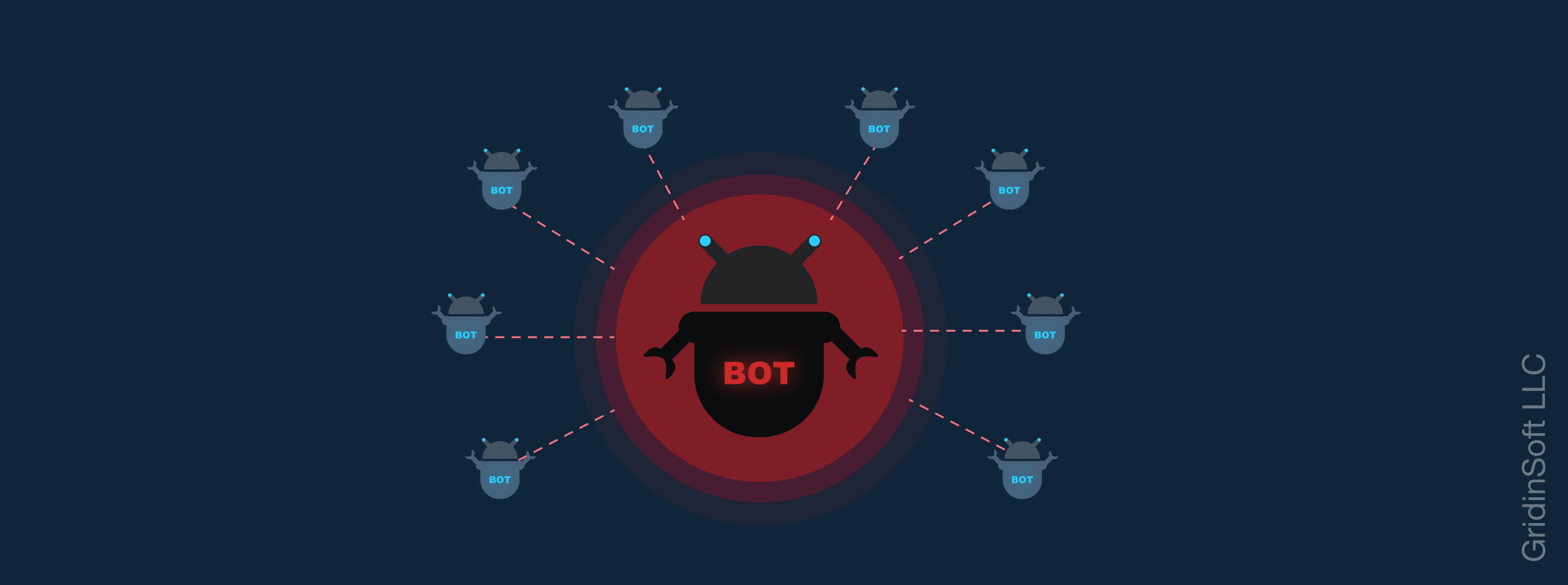
The Danger of Botnet Network: How to Detect Botnet on You PC
The word “botnet” is now ubiquitous, and almost all users know what it means. This is not surprising because this network can be virtually any device with Internet access. Such a network can infect many devices, such as desktop computers, smartphones, and home Wi-Fi routers. All of them may one day have weapons in the… Continue reading The Danger of Botnet Network: How to Detect Botnet on You PC