Fortinet disclosed a critical vulnerability affecting FortiClient EMS products in March 2024. This vulnerability, categorized as an SQL injection, poses a significant cybersecurity threat. Above all, it has the potential to allow remote attackers to execute arbitrary commands on administrative workstations.
Fortinet SQLi Vulnerability Causes Remote Code Execution
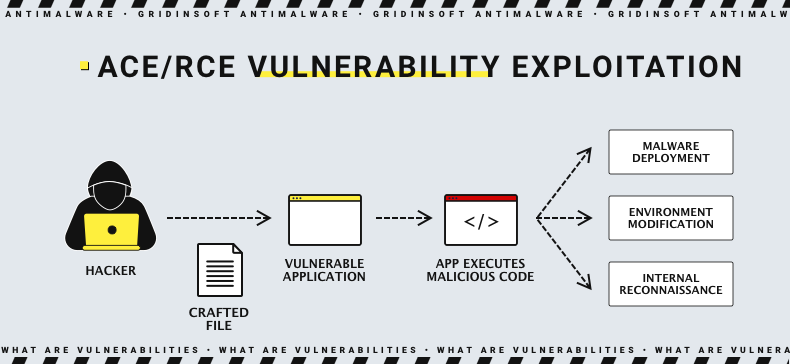
As I mentioned, the vulnerability is classified as SQL injection, which stems from improper neutralization of special elements used in SQL commands. However, successful exploitation can lead to the execution of the code, embedded into a specially crafted packet. Such a combination of two grants this flaw a CVSS rating of 9.8.
The discovery was made jointly by Fortinet and the UK’s National Cyber Security Center (NCSC). Fortunately, there is currently no information on whether the vulnerability exploited in the wild. But given the researcher’s promise to release indicators of compromise (IoCs), a proof of concept (POC), and a detailed blog next week, the possibility is rather high.
CVE-2023-48788 Vulnerability Overview
The vulnerability, identified as CVE-2023-48788, is considered severe, with urgent patches been released. Versions affected by the vulnerability include FortiClientEMS 7.2 (versions 7.2.0 through 7.2.2) and FortiClientEMS 7.0 (versions 7.0.1 through 7.0.10).
An attacker can exploit a SQL injection vulnerability (CWE-89) in FortiClientEMS to execute commands via maliciously crafted HTTP requests on a server with SYSTEM privileges. This jeopardizes the integrity of the system and could result in complete control of the vulnerable server. Also of particular concern is the fact that no authentication is required to exploit the vulnerability. It definitely adds to its severity rating.
Recall that in February, Fortinet disclosed a critical remote code execution (RCE) bug (CVE-2024-21762) in the FortiOS operating system and FortiProxy secure web proxy. The company also noted it as “potentially being exploited in the wild”.
Fortinet Releases Immediate Patch
Fortinet recommends that all users immediately upgrade their systems to the latest versions to address the vulnerability. Furthermore, you should regularly check the DAS logs for suspicious requests that may indicate an attempt to exploit the vulnerability.
| Version | Affected | Solution |
| FortiOS 7.2 | 7.2.0 through 7.2.2 | Upgrade to 7.2.3 or above |
| FortiOS 7.4 | 7.0.1 through 7.0.10 | Upgrade to 7.0.11 or above |
The developers also patched several other vulnerabilities this week. These including a critical write outside array (CVE-2023-42789) and buffer-based stack overflow (CVE-2023-42790) vulnerability in the FortiOS Capture Portal and FortiProxy. Also it could “allow an insider attacker with access to the Capture Portal to execute random code or commands via specially crafted HTTP requests”.