Octo Tempest, a financially-motivated hacking group, has been labeled “one of the most dangerous financial criminal groups” by Microsoft. Known as UNC3944 and 0ktapus, the group has gained attention for bold cyber attacks.
What is Octo Tempest Cybercrime Gang?
Octo Tempest’s journey into the world of cybercrime is an intriguing one. Only a few months ago, it became the first English-speaking affiliate of the BlackCat ransomware gang. This collaboration marks a rare occurrence in the cybercriminal ecosystem, as historically, Eastern European ransomware groups have been reluctant to do business with native English-speaking criminals.
Octo Tempest’s modus operandi is characterized by well-organized and prolific attacks, reflecting a depth of technical expertise and the involvement of multiple operators with hands-on-keyboard skills. The group first appeared on the radar in early 2022, initially targeting mobile telecommunications and business process outsourcing organizations for SIM swaps. Notably, their activities were traced to ransomware attacks against Las Vegas casinos in September of the same year.
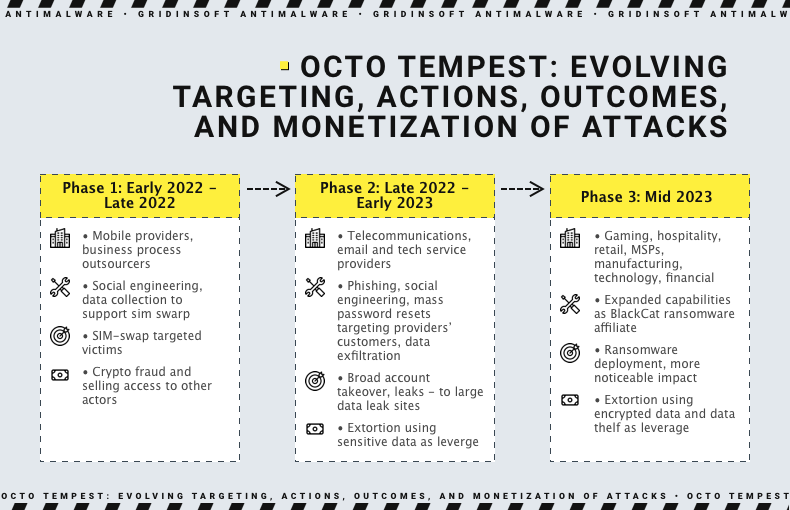
However, their ambitions did not stop there. In 2022, Octo Tempest orchestrated a large-scale campaign that compromised over 130 organizations, including prominent names like Twilio and Mailchimp, highlighting the group’s capacity to wreak havoc on a grand scale.
Collaboration with BlackCat and Ransomware Deployment
A significant turning point in Octo Tempest’s cybercriminal career was its collaboration with BlackCat, also known as ALPHV. The group began deploying ransomware payloads developed by BlackCat, extending their focus to both Windows and Linux systems. More recently, Octo Tempest has directed its efforts towards VMWare ESXi servers.
Octo Tempest remains financially motivated, with diverse monetization techniques. Their activities span from cryptocurrency theft to data exfiltration for extortion and ransomware deployment.
Octo Tempest Methods of Initial Access
Octo Tempest employs a range of methods for gaining initial access, including:
- Installing remote monitoring and management utilities.
- Navigating to fake login portals using an adversary-in-the-middle toolkit.
- Purchasing stolen employee credentials or session tokens on the dark web.
- Conducting SMS phishing campaigns targeting employee phone numbers with links to fake login portals.
- Leveraging SIM swaps or call forwarding on an employee’s phone number.
- Initiating a self-service password reset once control of the employee’s phone number is established.
- Fear-Mongering Tactics and Reconnaissance.
In rare instances, Octo Tempest resorts to fear-mongering tactics, targeting specific individuals through phone calls, texts, and even physical threats to coerce victims into sharing their credentials for corporate access.
Upon gaining initial access, the group proceeds with a meticulous reconnaissance process. It includes enumerating hosts and services, collecting information, and identifying documents related to network architecture, employee onboarding, remote access methods, password policies, and credential vaults. Their access to internal networks allows them to carry out broad searches across knowledge repositories to gather intelligence about the target’s infrastructure.
Defending Against Octo Tempest
Detecting and defending against Octo Tempest is no easy task due to their use of social engineering, living-off-the-land techniques, and a diverse toolkit. However, cybersecurity experts offer guidelines to help organizations detect and combat this rising cyber threat.
- Monitoring and reviewing identity-related processes, Azure environments, and endpoints are crucial steps in bolstering defenses against Octo Tempest.
- Educate yourself and your employees about social engineering and phishing tactics commonly used by Octo Tempest. Regular training on recognizing suspicious emails and links can help prevent successful attacks.
- Keep your operating systems, software, and applications up to date with the latest security patches. Cybercriminals often exploit known vulnerabilities in outdated software.
- Use a firewall to monitor and filter incoming and outgoing network traffic. Intrusion detection and prevention systems (IDPS) can also help detect suspicious activities.
- Regularly back up your data, both on-site and off-site. In the event of a ransomware attack, having clean, uninfected backups can save your data.
- Stay informed about emerging threats and vulnerabilities by monitoring cybersecurity news and threat intelligence feeds. This can help you adapt your defenses to evolving threats.