Proofpoint discovered a campaign in which hackers used a Firefox extension to hack Gmail. The attacks were linked to the Chinese group TA413.
According to the researchers, the campaign was active from January to February 2021. Hackers attacked Tibetan organizations around the world using a malicious Firefox extension that steals Gmail and Firefox data and then downloads malware onto infected systems.
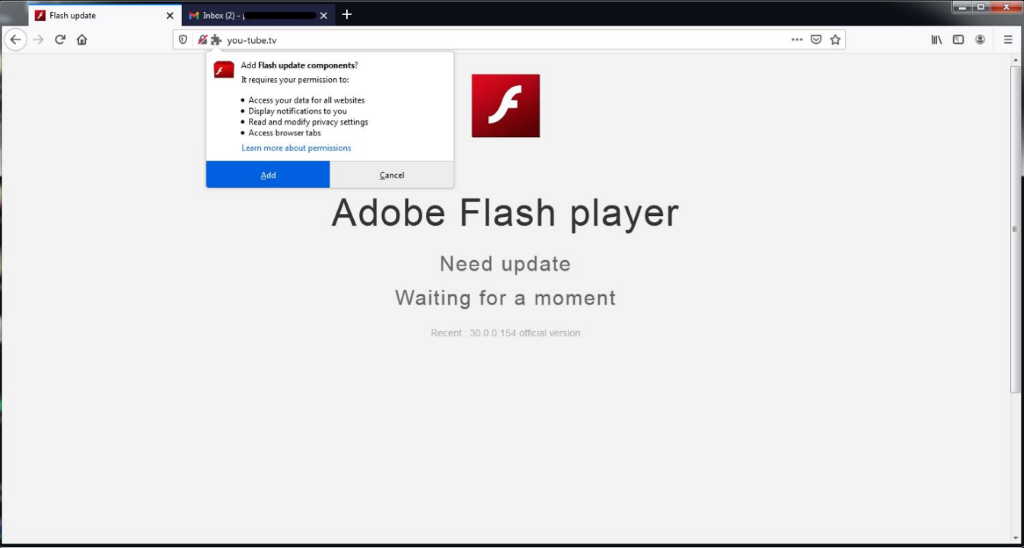
The researchers say that cybercriminals attacked Tibetan organizations with targeted phishing emails that lured victims to sites prompting them to install a fake Flash update, allegedly required to view the content.
In fact, these resources contained code that divided users into groups. So, only Firefox users with an active Gmail session were offered to install a malicious extension, while other hackers were not interested in other users.
The malicious extension was called Flash update components, but in fact it was a variation of the legitimate Gmail notifier (restartless) extension, and was capable of abusing the following features.
Gmail:
- Search for emails
- Archive emails
- Receive Gmail notifications
- Read emails
- Changing the audio and visual alert functionality in Firefox
- Flag emails
- Mark emails as spam
- Delete messages
- Refresh Inbox
- Forwarding letters
- Searching in email
- Delete messages from the Gmail Trash
- Send mail from a compromised account
Firefox (depends on the rights granted):
- Access to user data from all sites
- Show notifications
- Read and change privacy settings
- Access browser tabs
However, the attack did not end there. The extension also downloaded and installed ScanBox malware on the infected machine. It is an old malware tool based on PHP and JavaScript that has been used more than once in attacks by Chinese hack groups.
The last recorded use of ScanBox dates back to 2019, when analysts at Recorded Future noticed attacks on visitors of Pakistani and Tibetan sites.
Interestingly, this time the fake Flash attacks worked better than ever. While majority of users know for a long time that they should stay away from sites offering Flash updates, support for Flash was discontinued early this year. On January 12, 2021, all Flash content stopped playing in browsers, and this seems to be what made the TA413 attacks much more successful than usual.
Let me also remind you that a special version of Flash for China turned into adware.