Among hundreds of different types of scam emails, there is a specific scary one that bothers people around the world. Known as “Professional Hacker” scam email, it claims that an illusory hacker has accessed your PC and gathered whatever information, including capturing videos through the web camera. The message is accompanied by a ransom demand and threats to publish data if it is not paid.
Professional Hacker Email Scam Overview
Despite being a distinctive kind of email spam, “Professional Hacker” still has some variations to it. However, all of them have a text stating nearly the same thing: a hacker got into your computer and gathered a lot of sensitive information. If you do not pay the ransom – all this info will be published. Here are some common patterns the forms of this scam follow all as one.
Worrying Claims At The Very Beginning
The message starts with the subject like “Your personal data has leaked due to suspected harmful activities”. This serious yet threatening claim may already inflict fear and make the victim believe every word in the message body.
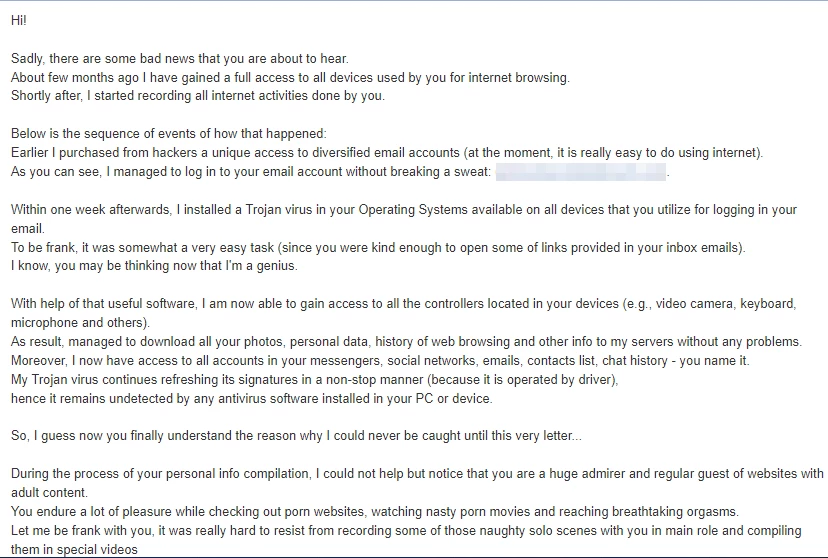
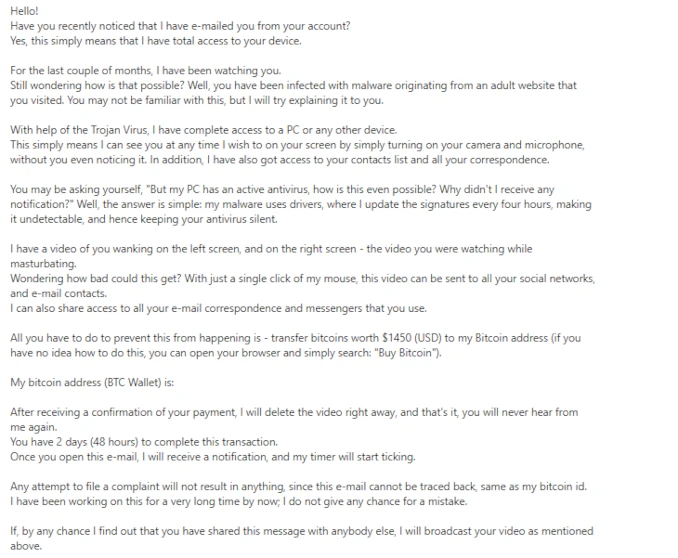
The body is not better either. Commonly, there are claims like “successfully managed to hack your operating system” and “gained full access to your account”. They are nonsense from the technical point of view, but look legitimate for people who are not aware of such details.
Fake Hacker Activities Description
Further in the message body, the hacker says that it was “monitoring all your activities and watching you for several months”. The crook claims it has installed infostealer malware (or trojan viruses) on your PC. Interestingly enough, the spreading way they say about a lot is “adult sites”. While in the past such pages were really a threat, it is barely a thing these days. It is also unclear why there is so much attention to a single victim. The actions the hacker boasts of may be done in a matter of days if not hours. Thence, it is either about unprofessionalism or stalking.
Claims On Compromised Video Being Recorded
Another typical claim is about the video taken from the webcam. Not a regular one – hacker says about a recording of you being in pretty compromising situations. This is, actually, the culmination point of the scam letter. These rows talk about the potential possession of highly compromising materials. In other words, this is what should force a victim to pay. It is particularly hard to prove or disprove this statement, though as the overall email has a lot of questionable takes, this one is not realistic either.
Explanation of Malware Invulnerability
To prove its proficiency, a hacker states that the malware it uses integrates at driver level, which makes it impossible to detect and remove. Well, this part is at least somewhat true – driver-level malware integration is a thing and it is done exactly to make both detection and removal much more complicated. But to perform such a trick, a hacker should either trick you into running the malware with high privileges or escalate them through an exploit – which is not a trivial task.
Some crooks also mention “hourly updates” (each several hours, daily, etc), which is, in turn, just fiction. There are much less effort-intensive ways to avoid detection, so using such an ineffective trick is either a mark of an unskilled hacker or a liar.
Ransom Demands & Publishing Threats
Obviously, the outro of the scam email – ransom demands. “Professional Hacker” commonly asks for a ransom in Bitcoins, and sets a deadline of 48-72 hours. If the demand is dismissed, the hacker promises to publish all the gathered info and videos on your social media – as it “has full access to your accounts”.
The ransom sum varies depending on unknown factors, but most commonly the ask ranges from $1000 to $2000 in Bitcoin. Some messages do not tell the ransom amount and instead offer to negotiate the sum on the email.
Typical Professional Hacker Scam Email Example
As I said, there could be dozens of different text variations of this scam. Though they differ just a bit, so I collected the most common ones.
Is “Professional Hacker” Email True?
No, it is just an attempt to make a scared user pay for deleting non-existent compromising materials. Sure, some of the things described in the email may happen. But the overall course of action is not how hackers normally work. Spending more than a month spying on a single victim is a thing in cyberattacks on large companies. However, doing so in attacks on home users is counter-productive.
There are a lot of things in the message that make me conclude it is a scam written by a low-profile scam actor. It may be aware of some typical tactics and practices that cybercriminals use. However, any of their attempts to describe them in detail uncover the complete incompetence of a subject. “Malware uses drivers” “Updating the signatures every four hours” – any tech-savvy guy will laugh his head off listening to such twaddle.
Social Engineering Tactics Used in “Professional Hacker” Email Scam
As you could have possibly supposed, Professional Hacker scam is based purely on social engineering. There are mistakes in the technical description of a “hack“ that show low technical competence. Nonetheless, the psychological tricks scam actors are trying to use are quite clear and professional. Let’s have a look at each one.
Pretending to be a professional
First paragraph of a scam message starts with a claim about being a professional hacker. Most probably, a victim will not trust it from the start. But it changes as a victim sees details adult sites, trojan viruses and the like. All these tales make the target person believe the hacker who attacked them is really a professional one, and it is not a joke.
The scammers’ hope here is that the target individual don’t know a thing about how hackers operate. And let’s be honest – there are quite a lot of people who don’t. They will surely believe a scary story about month-long spying with an undetectable malware.
Privacy compromise notifications
Once the authority is gained with the tricks I described above, the hacker switches to scaring the victim. The first sprouts of this appear at the very beginning of an email message – in the message subject. Then, the rascal says that it possesses a whole bunch of compromising information – from dialogues in messengers to video from a webcam with the victim watching content on adult sites.
This may look like a silly show, but don’t forget – the victim believes it is a genuine hacker who has sent an email. Thus, it can enforce a genuine fear or even panic, especially when a blind take about compromising messagings or visits to adult sites was dead-on.
Threats of public humiliation & ransom demands
By appealing to the compromising info possessed and the overall access to the victim’s system, a hacker threatens to publish all the info to social media, using the victim’s accounts. Sure enough, a scared user will now be ready to do whatever the hacker asks to avoid this. And the task is quite obvious – a ransom you should pay off in Bitcoins. The scammer specifies the wallet in the message. Even in the cases where the message body does not mention the ransom at all, it still ends up there.
Inflicting urgency
Despite all the places in this message that may scare the victim, the key element that makes it pay is time sensitivity. Hackers inflict urgency of a payment by saying that the deadline for making a payment is 48-72 hours from the moment when it have sent the message. No payment = all your friends on social media will know about your dirty deeds. Well, they would not, but hacker’s role is make you believe that this will happen.
Scan Your System For Spyware
Once you suspect that your system has some unwanted items in it, or see scam messages stating so, consider checking your system with a security tool. Despite what these wannabe-hackers say in the email, anti-malware programs are able to counteract spyware, trojan viruses and other malware. Sure enough, not each one can boast of top efficiency – a security program should feature most modern detection mechanisms. GridinSoft Anti-Malware can show you all the profits of such capabilities – consider trying it out.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.



The thing this article doesn’t mention about this scam is that sometimes it includes a password that the victim has actually used in the past, and also it may be sent from the victim’s e-mail address to itself, which can make the threat look more real and serious (which is the reason why I myself googled about it, honestly)
Same as Wonchi said, email comes from one’s email address and includes a password that has been used in the past. Tricky for sure but still scam.
Same scam e-mail over here: the scammer stated an old password and it was sent from a @hotmail.com e-mail address.
Indeed felt quite scary in the beginning, but after some google searches, things started to calm down.
Especially this article really made me calm down, thanks.
Nevertheless I changed practically all my passwords into more complicated ones.
But how can I report the scammer? Does hotmail.com have an option for this?