Bleeping Computer discovered that an exploit that uses the memory buffer of AMD and Nvidia GPUs to store malware and execute it, appeared for sale on a hacker forum.
In general, this method is not new and similar PoC exploits have already been published earlier, but all these projects were either implemented as part of academic research, or remained incomplete and unprocessed.
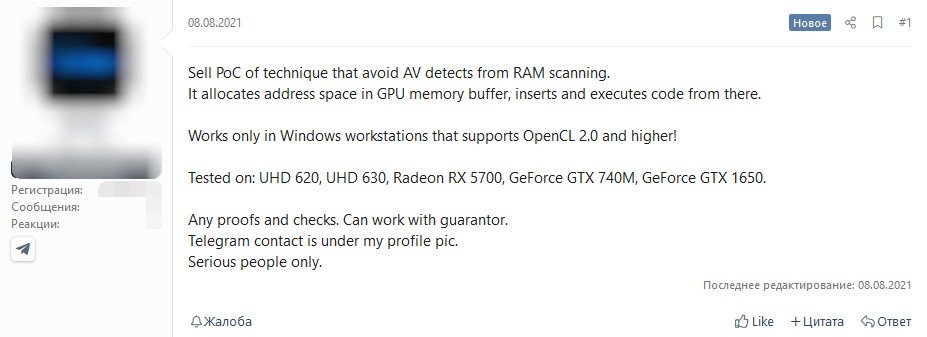
The exploit seller writes that his tool successfully protects malicious code from security solutions that scan system RAM. So far, it only works on Windows systems that support OpenCL 2.0 and above. The exploit author assures that his solution has been tested and works accurately on Intel (UHD 620/630), Radeon (RX 5700) and GeForce (GTX 740M, GTX 1650) video cards.
The announcement appeared on the hack forum on August 8 this year, and about two weeks later, on August 25, the seller announced that he had sold his PoC, but did not disclose any details about the deal.
VX-Underground researchers tweet that the malicious code sold does indeed work and allows the GPU to execute binaries.
They promised to demonstrate this attack technique soon.
Bleeping Computer journalists remind that GPU malware has already been created, referring to the JellyFish rootkit and the Demon keylogger. These projects were published in May 2015 and are still in the public domain. The foundation for such attacks was laid in 2013 by researchers from the Institute of Computer Science, FORTH and Columbia University in New York. They demonstrated that the work of a keylogger can be entrusted to GPUs and that they will save the intercepted keystrokes in their memory.
The seller of the new tool claims that its development has nothing to do with JellyFish and says that his method is different from the one presented in 2015, as it does not rely on mapping the code back to user space.
Let me remind you that I said that the GitHub Developers Review Exploit Posting Policy Due to Scandal.