BlackBerry and Intezer specialists spoke about the new Symbiote Linux malware that infects all running processes on compromised systems, steals credentials and provides backdoor access to its operators.
Let me remind you that we also said that Google Offers up to $91,000 for Linux Kernel Vulnerabilities, and also that Experts list 15 most attacked Linux vulnerabilities.
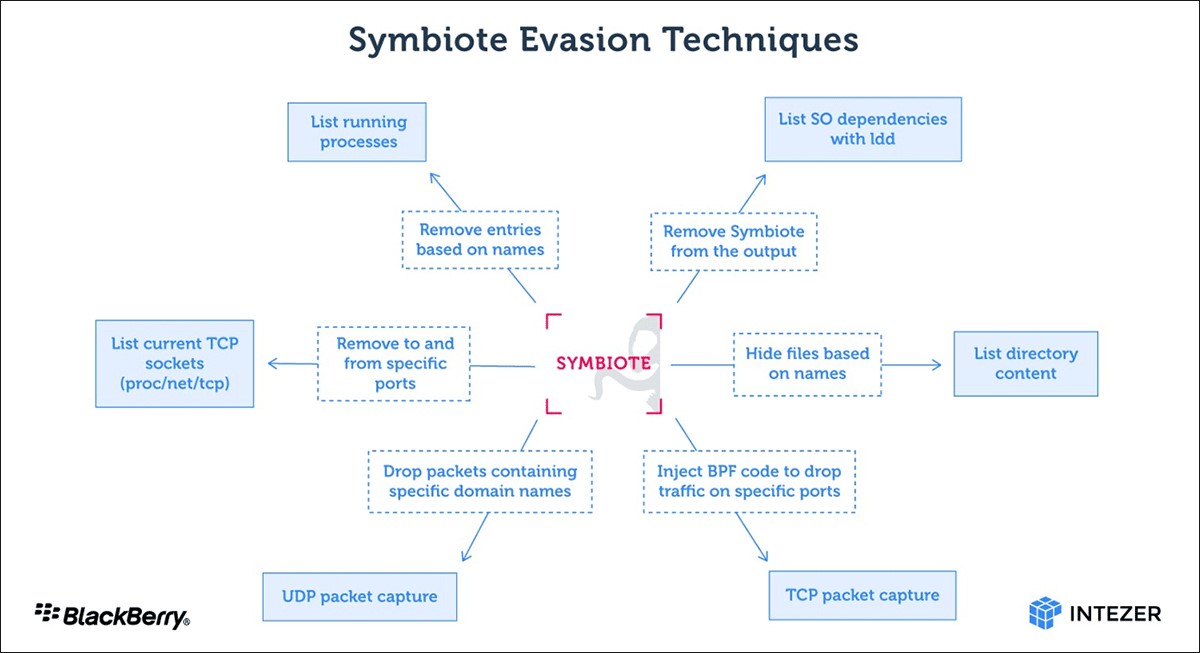
Infiltrating all running processes, the malware acts as a system-wide parasite, leaving no noticeable signs of infection, so it is difficult to detect Symbiote even with careful and in-depth study.
The development of Symbiote is believed to have started in November 2021, after which the attackers mainly used the malware to attack the financial sector in Latin America, including banks such as Banco do Brasil and Caixa.
Instead of a regular executable file, Symbiote is a shared object (SO) library that is loaded into running processes using the LD_PRELOAD function so that the dynamic linker will load malware into all running processes and infect the host. This approach was previously used by other malware, including Pro-Ocean and Facefish. Also, these actions help the malware get priority over other SOs.
Thus, with the help of the libc and libpcap functions, Symbiote can perform various actions to hide its presence in the system. For example, hide parasitic processes, hide files deployed with malware, and so on.
In addition to hiding its presence in the file system, Symbiote is also able to hide its network traffic using the Berkeley Packet Filter (BPF). This is done by injecting malware into the process and using BPF to filter the results that reveal its activity.
According to the researchers, Symbiote is now mainly used to automatically collect credentials from hacked devices (via libc read). The fact is that the theft of administrator credentials opens the way for attackers to unhindered lateral movement and gives unrestricted access to the entire system.
In addition, Symbiote provides its operators with remote SHH access to the infected machine via PAM, which allows attackers to gain root privileges.