LitterDrifter USB worm, intricately linked to the notorious Gamaredon group and originating from Russia. It has set its sights on Ukrainian entities, adding a concerning layer to the already complex world of state-sponsored cyber espionage. This USB worm, believed to be orchestrated by Russian actors, not only showcases the adaptability and innovation of Gamaredon but… Continue reading LitterDrifter – Russia’s USB Worm Targeting Ukrainian Entities
Tag: Hackers
Plume Hacked, Data Leaked in the Darknet
An anonymous hacker posted about a Plume data breach on the Darknet. The hacker says they have stolen the personal information of millions of users and threaten to release the data unless the company pays them a ransom. What is Plume? Plume Design, Inc. develops and sells smart home Wi-Fi mesh networking systems. Its flagship… Continue reading Plume Hacked, Data Leaked in the Darknet
North Korean Hackers Force US, Japan & South Korea Consultations
Increased activity by North Korean state hackers forced South Korea, the United States and Japan to create a special advisory group to coordinate cybersecurity efforts. The idea of consolidating efforts, apparently, was discussed back in August, at the international summit at Camp David. The decision was made last week following negotiations in Washington between Anne… Continue reading North Korean Hackers Force US, Japan & South Korea Consultations
American Airlines Hacked by Cl0P Gang, MOVEit Involved
American Airlines, the major airline company in the US, appears to be yet another victim of MOVEit vulnerability. Specifically, Cl0p ransomware gang hackers claim the successful attack upon the co. The post on their Darknet leak site does not disclose much, but the company is most likely already in the negotiations with hackers. What is… Continue reading American Airlines Hacked by Cl0P Gang, MOVEit Involved
California Water Treatment Plant Is in the Hands of a Hacker
Rambler Gallo, a resident of Tracy, Calif., has been charged with maliciously damaging a computer after it allegedly infiltrated a network of a water treatment plant in Discovery Bay. The treatment plant serves water and sewer systems for 15,000 residents of the city of Discovery Bay. Gallo was an employee of a private Massachusetts company… Continue reading California Water Treatment Plant Is in the Hands of a Hacker
Russian Hacker Project DDoSIA Grew by Multiple Times
Analysts of the Sekoia company reported that the Russian DDoSia hacker project grew by 2400% in less than a year. That project pays volunteers to participate in attacks on Western organizations. More than 10,000 people are currently involved in the attacks. DDoS-for-hire services became particularly popular over the last years. We recently did the review… Continue reading Russian Hacker Project DDoSIA Grew by Multiple Times
RepoJacking Attacks Could Threaten Millions of GitHub Repositories
Aqua researchers believe that millions of repositories on GitHub are vulnerable to an attack that allows taking over other people’s repositories and is called RepoJacking. The issue is reportedly affecting the repositories of Google, Lyft, and other major companies. Let me remind you that we also wrote that Malware in GitHub Repositories Is Spread From… Continue reading RepoJacking Attacks Could Threaten Millions of GitHub Repositories
APT28 Attacked Ukrainian and Polish Organizations
Recorded Future, in collaboration with CERT-UA researchers, has unveiled a recent cyber offensive orchestrated by Russian-speaking hackers affiliated with the APT28 Group (also known as Fancy Bear, BlueDelta, Sednit, and Sofacy). Their target: Roundcube mail servers of various Ukrainian organizations, including government entities. As a reminder, we previously reported on the divergence of hacker groups,… Continue reading APT28 Attacked Ukrainian and Polish Organizations
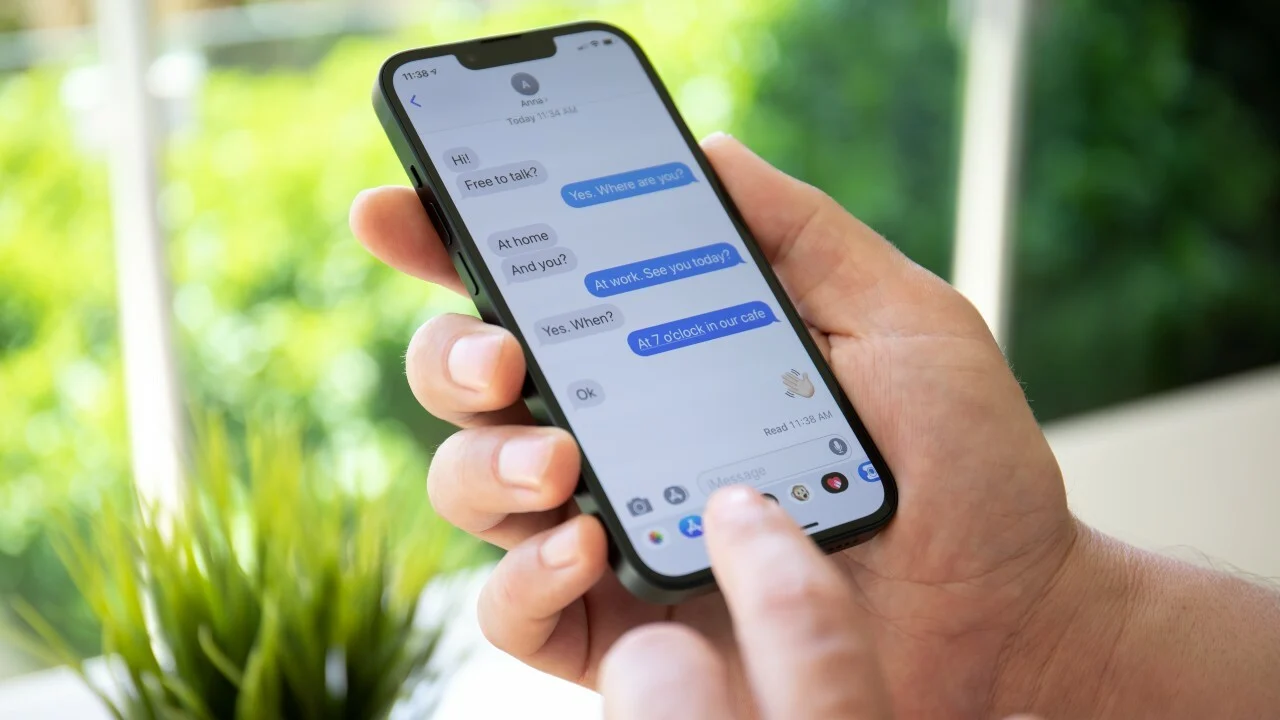
Freaky Leaky SMS: Message Delivery Report Can Be Used to Determine the Location of the Recipient
Researchers have created a side-channel attack called “Freaky Leaky SMS”, which allows finding out the location of the recipient of messages, based on the delivery time of reports on the receipt of SMS messages. Let me remind you that we also wrote about true Apocalypse Now: experts presented a new type of cyber-biological attack, and… Continue reading Freaky Leaky SMS: Message Delivery Report Can Be Used to Determine the Location of the Recipient
Malware Propagation On Darknet Forums
The forums on the dark web are well-known for being a hub of cybercriminal activity, including an auction system. Here, bad actors can trade tips on hacking, share samples of malware, and demonstrate how to exploit vulnerabilities. For those who develop malware, Darknet communication platforms, specifically forums, became a perfect marketing platform. The developers of… Continue reading Malware Propagation On Darknet Forums