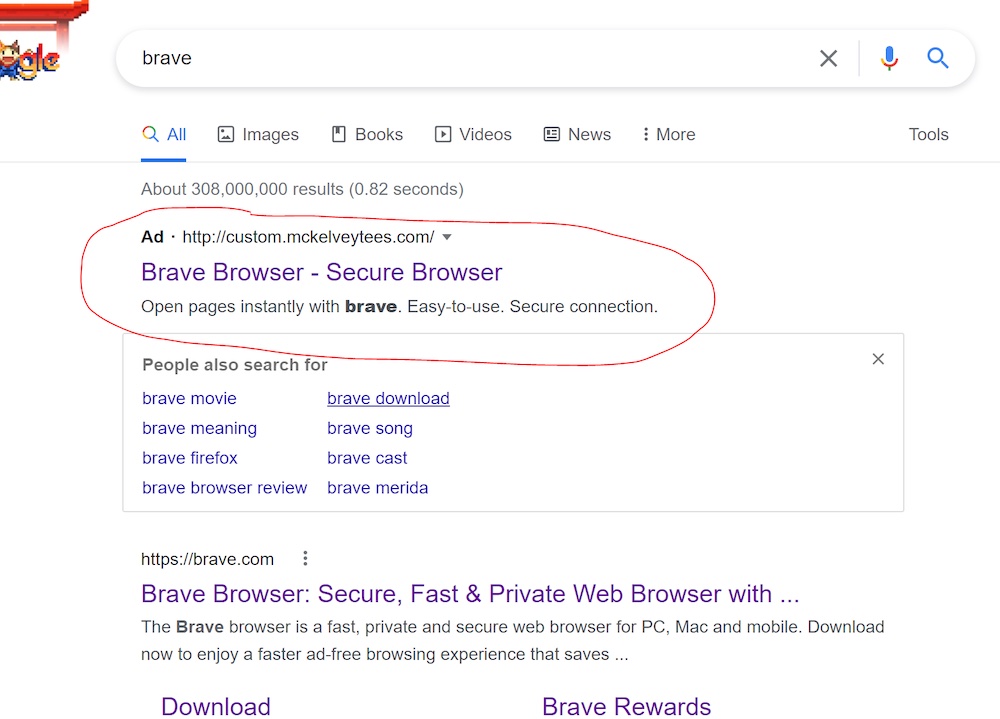
Google specialists stopped a malicious advertising campaign in which scammers lured users to a fake Brave browser site, where ArechClient (SectopRAT) malware was hiding under the mask of a browser.
To drive traffic to a fake site, scammers bought ads on Google, which were displayed when people searched for something related to browsers.
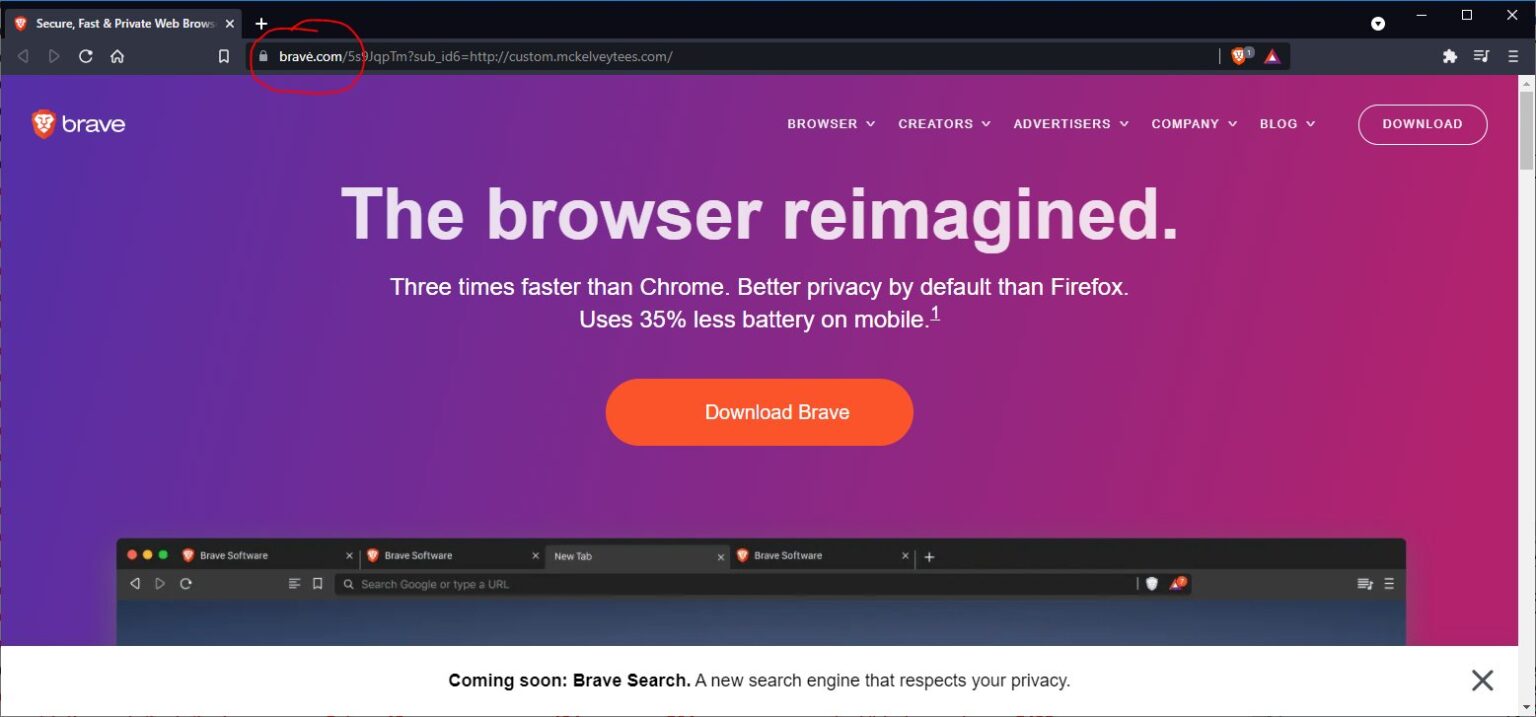
The researchers say they spotted this cleverly masked ad that redirected visitors to a malicious site. The resource was located at bravė.com, where the word “Brave” was written with the Lithuanian letter “ė” instead of the usual Latin “e”.
Scammers use Punycode to bypass security filters and lull users’ vigilance, and this is not a secret anymore.
Punycode is a standardized method for converting sequences of Unicode characters to ACE sequences, which consist only of alphanumeric characters, as is allowed in domain names.
Punycode was designed to unambiguously convert domain names to a sequence of ASCII characters.
In a modern browser, the malicious domain bravė.com will turn into xn--brav-epa.com, but users can ignore the address bar without noticing the substitution.
Users were prompted to download a 303MB ISO file, allegedly containing the Brave installer. Oddly enough, the browser was also present in this file, but along with it, ArechClient (SectopRAT) malware was distributed, the main task of which is to steal data from browsers and cryptocurrency wallets.
It is also worth mentioning that after detecting and blocking the attack, the Namecheap registrar, which was used by the attackers, disabled all their domains, including other fraudulent sites, which, for example, masked as official Tor, Signal and Telegram resources (lędgėr.com, sīgnal.com, teleģram.com).
You may also be interested to know that Malware developers increase use of the unusual programming languages.