Rapid7 analysts and independent information security expert Rafay Baloch discovered that seven popular mobile browsers are vulnerable to url spoofing. They allow malicious sites to change the URL and display a spoofed address in the address bar.
Basically, the problem of address bar spoofing existed since emergence of the Internet.
With the ever-increasing sophistication of targeted phishing attacks, exploiting browser vulnerabilities such as address bar spoofing can contribute to the success of targeted phishing attacks and, therefore, they may prove fatal.
And while modern desktop browsers have a lot of security mechanisms that make it easy to detect a fake URL, mobile browsers are less protected.
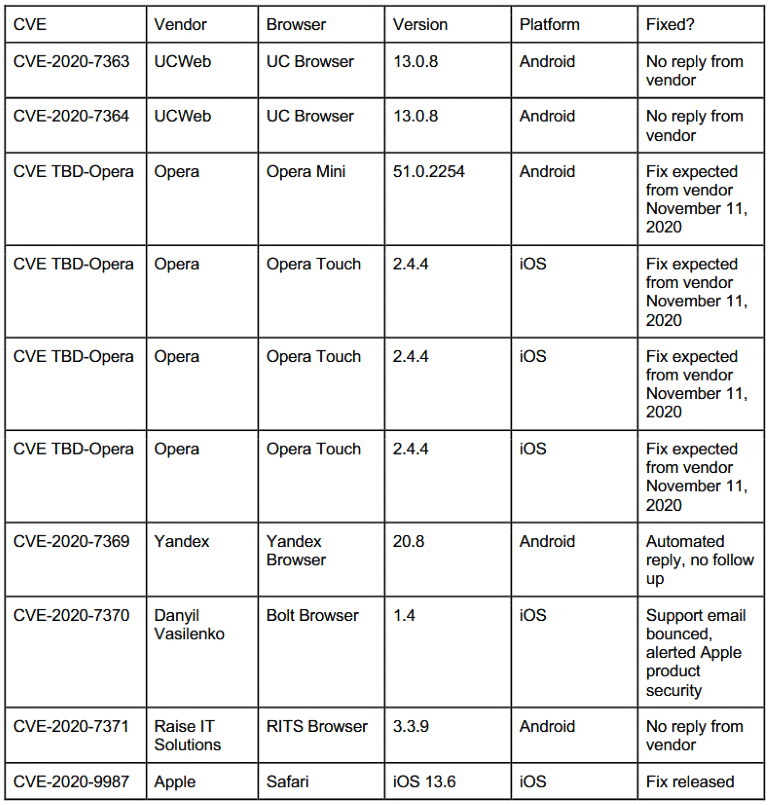
As mentioned above, the researchers found that seven mobile browsers are vulnerable to such spoofing. These are Apple Safari, Opera Touch and Opera Mini, Bolt, RITS, UC Browser, and Yandex.Browser.
The researchers explain that usually the exploitation of such bugs comes down to various manipulations with JavaScript. For example, by dealing with the time that elapses between loading a page and the moment the browser is able to update the URL in the address bar, a malicious site can force the browser to display the wrong address.
Most often, this will be the URL of a certain legitimate site, for which scammers are trying to pass off their resource. A detailed description of all found bugs can be found on Baloch’s blog.
The vulnerabilities were identified this summer, and the researchers notified the developers of the problems in August. As you can see in the table below, large vendors eliminated vulnerabilities very quickly, while small ones did not even bother to answer specialists, let alone release of patches.
Experts strongly recommend users to update their browsers, and if patches are still missing, use other, more secure applications.
What is good about url spoofing – at least it won’t burn you! But BadPower attack can set devices on fire!