The US cyber command warned that in PAN-OS was discovered a dangerous vulnerability and that soon government hack groups are likely to start using it.
PAN-OS is an operating system running on firewalls and corporate VPN devices, manufactured by Palo Alto Networks.
The cause for concern is really serious: the CVE-2020-2021 vulnerability is one of those rare errors that get 10 out of 10 points on the CVSSv3 vulnerability rating scale. Such score means that the vulnerability is easy to use, its operation does not require serious technical knowledge, and it can also be used remotely via the Internet, and attackers may not have any “fulcrum” on the target device.
“From a technical point of view, the vulnerability is an authentication bypass and allows an outsider to gain access to the device without providing credentials. After successfully exploiting the problem, the attacker can change the PAN-OS settings. In essence, this can be used to disable access control policies in the company’s firewalls and VPN solutions, after which the devices will become practically useless”, — said USCYBERCOM representatives.
I also note that Trump declared a state of emergency due to cyberattacks on US energy systems.
Palo Alto Networks specialists have already prepared their own security bulletin, which says that for the successful operation of the problem a number of conditions must be met.
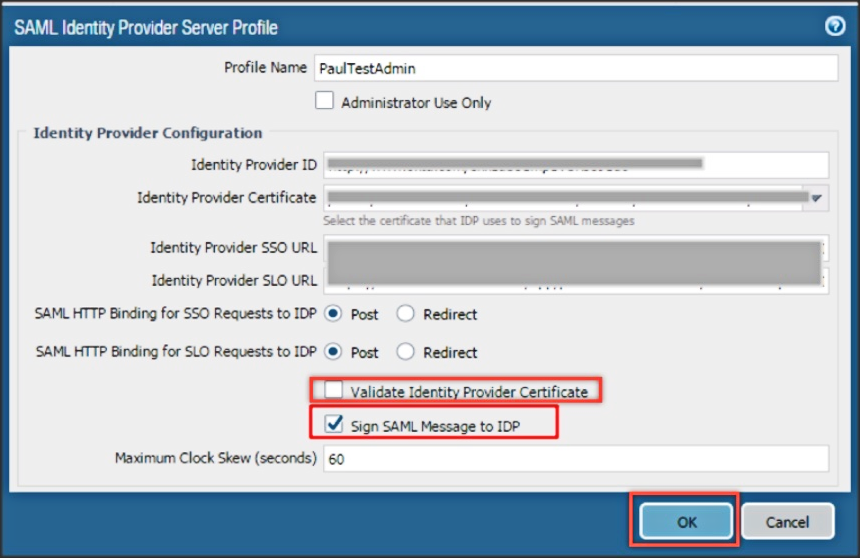
In particular, PAN-OS devices must have a specific configuration so that the error can be used. So, the option Validate Identity Provider Certificate should be disabled, and SAML (Security Assertion Markup Language) on the contrary enabled.
Devices that can be configured this way are vulnerable to attack. These include:
- GlobalProtect Gateway;
- GlobalProtect Portal;
- GlobalProtect Clientless VPN;
- Authentication and Captive Portal;
- PAN-OS firewalls (PA and VM series) and Panorama web interfaces;
- Prisma Access Systems.
Fortunately, by default, the above settings are set to other values. However, CERT/CC expert Will Dorman warns that when using third-party identity providers in many PAN-OS operator guides, it is recommended to stay attached to this configuration. For example, when using Duo authentication or third-party solutions from Centrify, Trusona and Okta.
“As a result, despite the fact that at first glance the vulnerability does not look too dangerous and requires certain conditions to be met, in fact, many devices are configured exactly as described above, especially due to the widespread use of Duo in the corporate and public sectors”, – told in Palo Alto Networks.
According to Troy Mursch, co-founder of Bad Packets, the current number of vulnerable systems is approximately 4,200.
“Of the 58,521 Palo Alto public servers (PAN-OS) scanned by Bad Packets, only 4,291 hosts use some kind of SAML authentication”, — write the expert.
He also clarifies that the scan conducted by his company helped determine whether authentication with SAML is enabled, but in this way you cannot find out the status of the Validate Identity Provider Certificate.
Currently, information security experts are urging all owners of PAN-OS devices to immediately check the configurations of their devices and install patches released by Palo Alto Networks as soon as possible.
Let me remind you that according to the report of Radware company specialists, government hackers attacked more often in 2019-2020.