An old-good form of malware disguisment sparked recently in several Spanish-speaking countries across the globe. Users note numerous cases of email attachments with spoofed file extensions, that appear to be coin miner trojans.
Massive outbreak of extension spoofing in email spam
Email spam is a form of malware spreading that became very popular at the edge of the current decade. It was used earlier as well, but with a much smaller scale. This spreading way may fit different needs – from massive spamming without target selection to spear phishing against the corporation employees. In modern practices, email spam usually contains something that makes the victim believe in the legitimacy of this letter. Background similar to the one used by FedEx, some routine patterned words about the incoming delivery – and voila – user believes you. After gaining your trust, they will try to trick you into following the link, or opening the attached file – the latter usually contains malware. The former, however, may lead the victim to the phishing page, or to the exploit site, where crooks will try to install malware.
Hence, if attaching the malware was not something new – what is the reason to wonder about the new wave? Hundreds of them happen each day, so they do not look like something worth attention. The peculiar item about those attacks is that they apply the use of extension spoofing techniques in order to disguise the attached file. That approach was not seen for a long time – but it popped up, again.
What is extension spoofing?
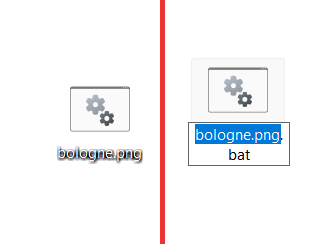
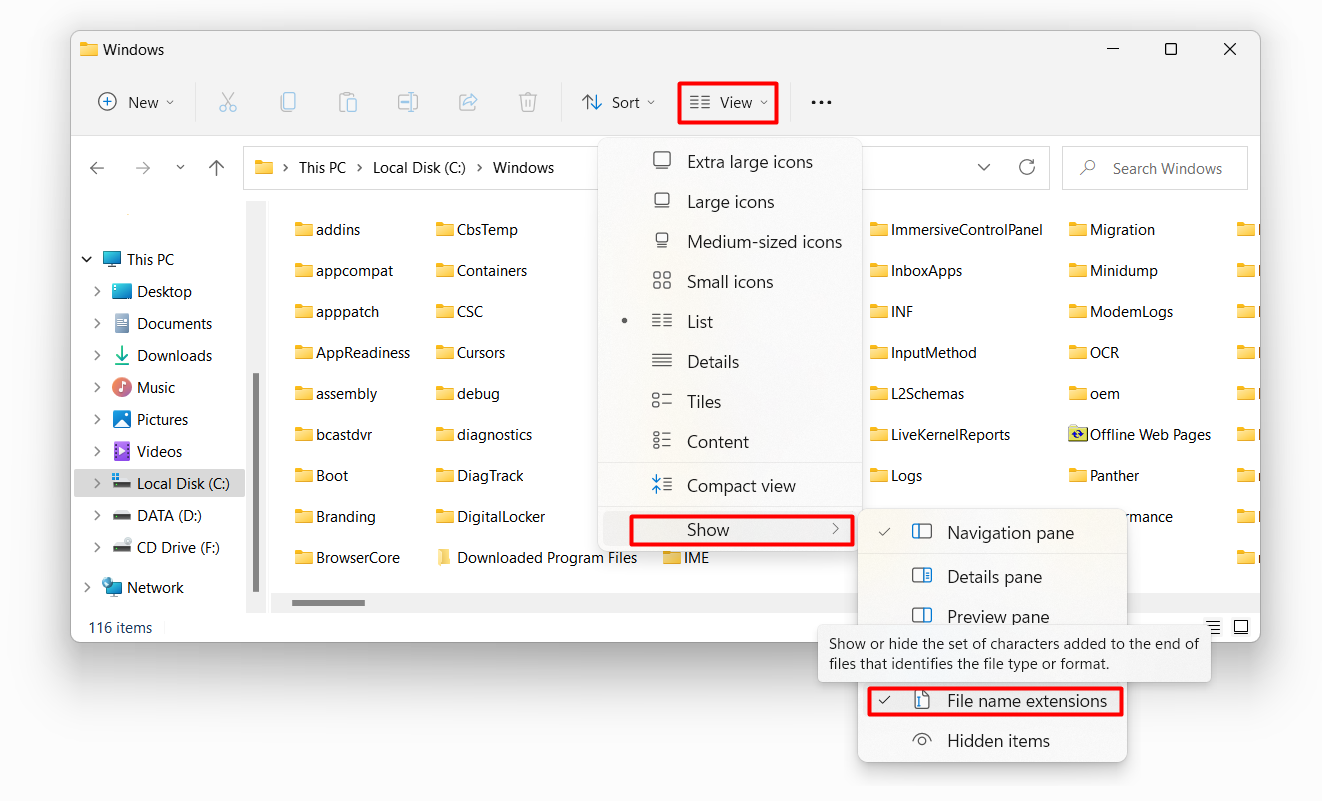
Extension spoofing is a trick with file names that visually changes the file format. It is based on Windows default settings of file extension display. By default, you see only the filenames – without extensions. When you spectate the opened folder in a list view mode, you’d likely fail to see the file icons. Therefore, you can add the extension you want to the end of your file, but in fact leaving it unchanged.
For example, you can make the batch script file and name it as “tuxedo-cat.png.bat”. Users will see it as “tuxedo-cat.png”, but in fact it will be the batch file that will run as soon as you’d try to open it. Moreover, low-skill users may easily miss the second extension, thinking that the first one is original. That trick is very old, but still effective – especially with the latest visual updates in Windows.
Who is under attack?
Most of the spectated cases appear in Spanish-speaking countries. Users from Mexico, Chile, Ecuador and, exactly, Spain reported the appearance of routinely looking emails with attached files. The latter had the naming like “confiromidad entrega material ].xlsx.exe or “resumenes info socioeco.xlsx.exe”. As you can see, the extension spoofing there has its easiest form – the one you can uncover by just seeing the detailed information about the file. However, the victims were tricked by the file names – they were too similar to the documents you work with everyday.
In those files, the coin miner virus is hiding. When you are trying to open this file, thinking it is legit, you will see no effects. But in the background, malware starts its nasty job. Coin miners, as you can suppose by the name, exploit your hardware to mine cryptocurrencies. Contrary to legit miners that you can install these do not let you to set how much hardware power they can use. You will see your CPU and GPU overloaded, so the PC will be barely operable.
How to prevent extension spoofing and email spam?
There is not a lot you can do about the exact email spam. Mailing will be possible until you have an active email account. However, you can do a lot to make the spam much less relevant and thus less believable.
Extension spoofing is much easier to prevent. There are techniques which allow the crooks to mask the file in a more reliable way, but they are rarely used these days. Most cases can easily be mirrored with simple diligence.