A set of process injection techniques, named PoolParty, was presented at the Black Hat Europe 2023 conference. A set of 8 tricks allows to force running any malicious code, and circumvents protection of top-notched EDR solutions.
PoolParty Process Injection Exploits Windows Mechanisms
The initial presentation of the techniques, along with further analysis, reveals a chain or simple yet genius tricks. As it comes from the name, PoolParty plays with Windows thread pool. It is an internal mechanism that orchestrates system functions execution during the application runtime. Let’s dig into the details a little bit.
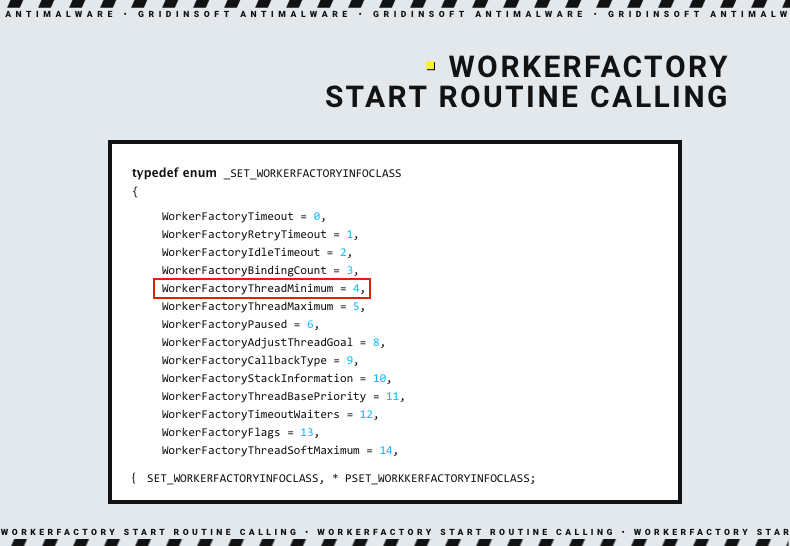
There is an object in Windows called “worker factory” – a thing responsible for managing the number of worker threads. The latter, as I’ve said above, are used to execute system functions needed for the programs to operate. Each process running in the system eventually gets its own worker factory, with a set of worker threads needed to run it.
The system itself offers the ability to dump the info of a chosen worker factory, including the start routine value. It is possible to simply substitute this value with the one needed to run the malware, for example – a malicious shellcode. Through the same worker factory calls, it is possible to speed up the process by initiating the start routine execution when needed rather than waiting when the system runs it.
Thread Pool Attacks
Another edge of the attack targets not the workers and worker factories, but thread pools. Those are, essentially, strings of tasks the system should perform; a to-do list for the workers, one may say. Through playing with specific properties of work item types, it is possible to feed a malicious task to the task list for workers.
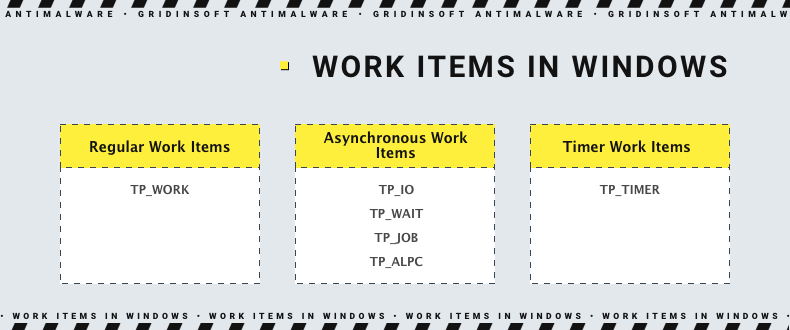
As there are separate types of queue for regular, timer and asynchronous jobs, devs can fine-tune the execution flow of the program. Or, in the case of malicious exploitation, the fine-tuning is applied to malware execution. Depending on the type of job, the way of injection differs, becoming the most complicated on timer jobs. But nonetheless, all three types of jobs remain the attack surface – and there is not much EDR solutions can do about it.
Are PoolParty Injects Dangerous?
Indeed, they are. Process injection is a bread and butter of pretty much every malware launching procedure. A malicious program in the form of an executable file is nowadays a rare sight: they mostly come as DLLs or portable executable files. But to the moment all the techniques used to launch such malware were researched to the last tiny bit. Hollowing, duplicating, thread hijacking – we know not only its mechanism, but also the ways to counteract it.
The latter, however, is not the story about PoolParty injection methods. This vile eight is researched, but is successfully ignored even by top-rated EDR solutions. And those are security solutions called to protect enterprises and have the biggest protective capabilities – leave alone the effectiveness of user-oriented antivirus programs.
Therehence, it is extremely important to follow the preventive techniques against malware injection. Giving it zero chances to even appear in your system means it cannot do such tricks as PoolParty are. Among such are effective network protection, content disarming utilities, firewalls, and email protection solutions. However, security essentials like privileges limitation or access control will work out as well. Even having the way to detect such threats, it will be great to avoid their appearance in the first place.


it is very good idea