The Pig Butchering scam, a scam operation that specializes in fake investments in allegedly promising cryptocurrency projects, stocks, bonds, futures and options, was found in the Apple and Google app stores. Such attacks are called “pig slaughter”, and scammers use social engineering against their victims (“pigs”), finding contact with them on social networks and dating… Continue reading Cryptocurrency Scam “Pig Butchering” Penetrated the Apple App Store and Google Play Store
Tag: Google
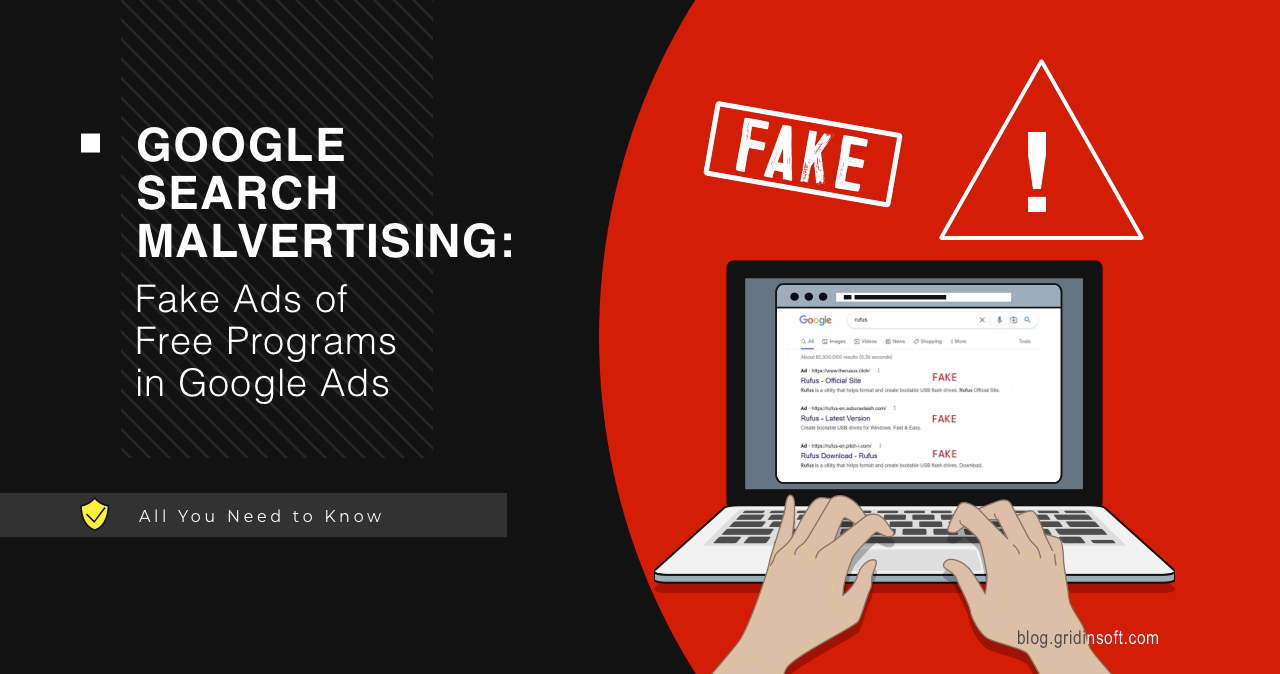
Google Search Malvertising: Fake Ads of Free Programs in Google Ads
Google Search malvertising is an unpleasant phenomenon of malicious advertisements in search engine results. Ads up there are called to make it easier to find users interested in specific queries, but it ended up being yet another object of hackers’ exploitation. Let’s see why these links appear, how dangerous they are, and how you can… Continue reading Google Search Malvertising: Fake Ads of Free Programs in Google Ads
Hackers Are Misusing Google Ads to Spread Malware
Malware operators and other hackers are increasingly abusing Google Ads to distribute malware to users who are looking for popular software. So, you can encounter malicious ads when searching for Grammarly, MSI Afterburner, Slack, Dashlane, Malwarebytes, Audacity, μTorrent, OBS, Ring, AnyDesk, Libre Office, Teamviewer, Thunderbird, and Brave. Let me remind you that we also wrote… Continue reading Hackers Are Misusing Google Ads to Spread Malware
42,000 Sites Generate Ad Traffic Pretending to Be Famous Brands
The Chinese group Fangxiao has built a huge network of 42,000 websites that pose as well-known brands (including Coca-Cola, McDonald’s, Knorr, Unilever, Shopee and Emirates) and generate ad traffic. These resources redirect their visitors to sites that advertise adware applications, dating sites, giveaways, or infect their systems with the Triada Trojan. You might also be… Continue reading 42,000 Sites Generate Ad Traffic Pretending to Be Famous Brands
Attackers Hacked 15,000 Websites to Poison SEO
Sucuri analysts have discovered a massive hacking campaign in which the attackers hacked about 15,000 sites, mostly running WordPress. Let me remind you that we also wrote that 0-day Vulnerability in WordPress BackupBuddy Plugin Attacked Over 5 million Times, and also that Ukraine Was Hit by DDoS Attacks from Hacked WordPress Sites. Attackers use compromised… Continue reading Attackers Hacked 15,000 Websites to Poison SEO
Meta Finds over 400 Chinese Apps That Stole Data from 1 million Users
Meta has sued several Chinese companies (including HeyMods, Highlight Mobi and HeyWhatsApp) for developing and using “unofficial” WhatsApp apps for Android. The fact is that since May 2022, these applications have been used to steal more than a million WhatsApp accounts. By the way, also read our article: Top Facebook Scams 2024: How to Avoid… Continue reading Meta Finds over 400 Chinese Apps That Stole Data from 1 million Users
SharkBot Malware Infiltrates Google Play Store Again
Information security specialists from Fox IT discovered two applications in the Google Play Store that distribute the SharkBot Trojan: Mister Phone Cleaner and Kylhavy Mobile Security were installed more than 60,000 times in total. Let me remind you that we wrote that Researchers Found 35 Malware on Google Play, Overall Installed 2,000,000 Times, and also… Continue reading SharkBot Malware Infiltrates Google Play Store Again
Researchers Found 35 Malware on Google Play, Overall Installed 2,000,000 Times
Bitdefender experts found 35 malware in the Google Play Store that distributed unwanted ads, and which users in total downloaded more than 2,000,000 times. Let me remind you that we wrote that About 8% of apps in the Google Play Store are vulnerable to a bug in the Play Core library, and also that Mandrake… Continue reading Researchers Found 35 Malware on Google Play, Overall Installed 2,000,000 Times
Most Often, Malware to Bypass Protection Impersonates Skype, Adobe Acrobat and VLC
VirusTotal analysts presented a report on the methods that malware operators use to bypass protection and increase the effectiveness of social engineering. The study showed that attackers are increasingly imitating legitimate applications such as Skype, Adobe Reader and VLC Player to gain the trust of victims. Let me remind you that we also wrote that… Continue reading Most Often, Malware to Bypass Protection Impersonates Skype, Adobe Acrobat and VLC
Fraudsters Are Running a Malicious Advertising Campaign through Google Search
Malwarebytes, an information security company, has discovered a large malicious campaign that skillfully uses ads and Google search. A phishing campaign using Windows tech support is spreading through Google Ads. Let me remind you that we wrote that Companies in the EU will have to remove Google Analytics from their websites, and also that Google… Continue reading Fraudsters Are Running a Malicious Advertising Campaign through Google Search