As we wrote in one of the articles, SQL is a structured query programming language (SQL, Structured Query Language) that allows programmers to communicate with large databases in almost plain English. It also gives the ability to access and manipulate data stored in tables on the server. In the case of websites, the tables can store sensitive data such as logins, passwords, credit card numbers, etc. And if proper precautions are not taken, sites can be tricked by simply running malicious SQL queries. This is called SQL injection, and today we will examine in detail what types of this there are.
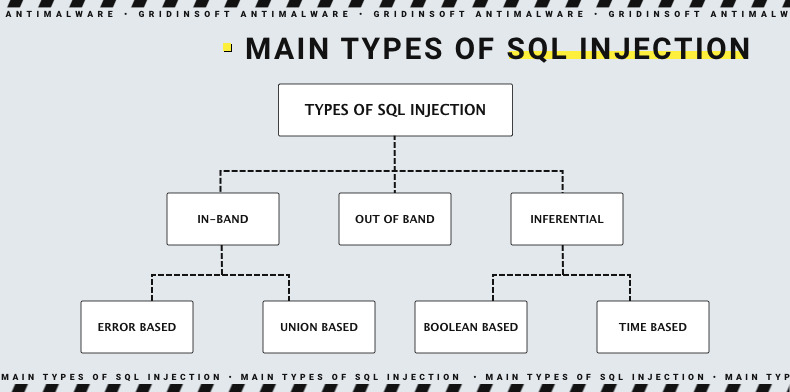
SQL injection has different use methods, and all of them can cause serious problems. For example, with SQL injection, an attacker can bypass authentication, access databases, and change or delete their contents. Sometimes SQL injection can be used to execute a command in the Operating system. This will allow the attacker to do even more colossal damage, even if the network is behind a firewall. Conventionally SQL injection can be divided into three main categories – In-band SQLi, Inferential SQLi, and Out-of-band SQLi.
In-band SQLi (Classic SQLi)
In-band SQL injection – most common and simplest SQL injection attack. It occurs when an attacker cannot use the same communication channel to launch the attack and to collect the results. The most popular types of in-band SQL injection are Error-based SQLi and Union-based SQLi.
Data exfiltration using in-band attacks is done either through error messages that appear in the web application triggered by the SQL injection attack or by using the UNION statement, which allows the attacker to insert his SQL queries.
Error-Based SQL Injection
Error-based SQLi is an attack, and it relies on error messages that the database server throws to obtain information about the database structure. Sometimes all it takes is one SQL injection based on errors, and an attacker can enumerate the entire database. Errors are often useful at the development stage of a web application, on a live site they should be disabled or written to a restricted file.
Union based SQL Injection
A merge-based SQLi is a technique that uses the UNION SQL statement to combine the results of more than two SELECT statements into one result, which is then returned as part of the HTTP response. The peculiarity of this method is that it will work only if the number of columns returned by the first query is equal to the number of columns returned in the second query.
Inferential SQLi (Blind SQLi)
Unlike in-band SQLi, inferential SQL injection may take the attacker more time, but it is no less dangerous than any other SQL injection. In an inferential SQLi attack, data is not passed through the web application, and the attacker cannot see the result of the in-band attack (that’s why these attacks are also called “blind SQL injection attacks“). Instead, the attacker can reconstruct the database structure by sending the payload, and observing the response of the web application and the behavior of the database server. Blind-boolean-based SQLi and Blind-time-based SQLi are two types of SQL injection. But not only websites display the data returned from the database, which is vulnerable.
Boolean-based (content-based) Blind SQLi
Boolean-based SQL injection is an inferential SQLi method that relies on sending an SQL query to a database, which causes the application to return a different result depending on whether the query returns a TRUE or FALSE result.
The content of the HTTP response changes or stays the same depending on the result, allowing an intruder to infer whether the payload used is true or false, even if no data is returned from the database. This attack is usually slow (especially for large databases) because the attacker would have to list the database character by character.
Time-based Blind SQLi
Temporary SQL injection is an inferential SQLi method, which is based on sending an SQL query to the database that causes the database to wait a certain amount of time (in seconds) before responding. It is the response time that tells the attacker whether the result of the query is TRUE or FALSE.
The HTTP response will be returned with a delay or immediately, depending on the result, and will allow the attacker to infer whether the payload used is true or false, even if no data is returned from the database. This attack is also usually slow (especially for large databases) because the hacker must enumerate the database character by character.
Out-of-band SQL Injection
Out-of-band SQL injection is relatively rare because it depends on the features enabled on the database server used by the web application. Out-of-band SQL injection occurs when an attacker cannot use the same channel to conduct an attack and collect the results. Out-of-band methods for the hacker are an alternative to time-based methods, especially if the server responses are not very stable (which reduces the effectiveness of a time-based attack).
Out-of-band SQLi methods rely on a database server’s ability to make DNS or HTTP queries to deliver data to an attacker. This refers to the xp_dirtree Microsoft SQL Server command, which can be used to make DNS queries to an attacker-controlled server, and the UTL_HTTP Oracle Database package, which can be used to send HTTP queries from SQL and PL/SQL to an attacker-controlled server.