What does spam mean in texting? Receiving random text messages from unknown numbers is unsettling. But, unfortunately, spam is more than just irritating. It can also be a locomotive for malware. Read on to learn how to block random text messages from unknown numbers, stop spam, and protect against other scams. What are spam text… Continue reading Texting Spam: How to Stop Spam Text Messages
Tag: Online Security
Difference Between IPSec and SSL
In the last couple of years, remote work has become integral to the world business landscape. However, to make remote work more efficient, employees need access to the company network wherever they are. A virtual private network (VPN) solves this by allowing remote employees to connect directly to the network, performing tasks as if they… Continue reading Difference Between IPSec and SSL
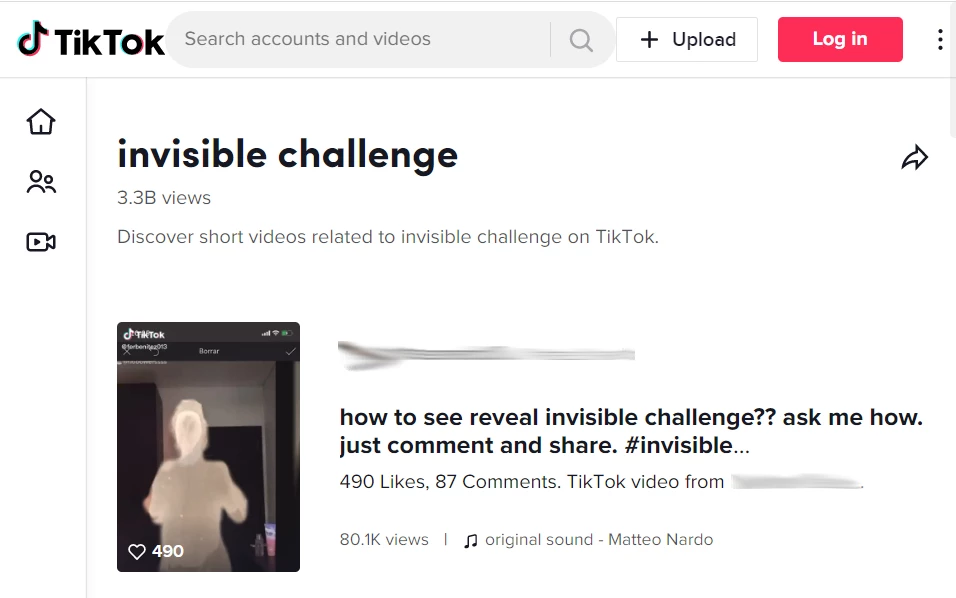
TikTok Invisible Challenge Is Used to Spread Malware
TikTok Invisible Challenge became yet another host for threat actors. Crooks found a way to spread the WASP information stealer as a specific utility to revert the in-app filter. Users who ate the bait are risking their account credentials and banking information. What is the TikTok Invisible Challenge? Same as Instagram back in the previous… Continue reading TikTok Invisible Challenge Is Used to Spread Malware
Online Dating Scams: How to Avoid Romance Scam
Online dating scammers get you to believe that their fake romances are real. They use deceptive tactics to make their scams hard to detect. The overall fraud got the name of a romance scam. Let’s see how a romantic meeting online may turn into a money loss. What is a romance scam? Romance scam artists… Continue reading Online Dating Scams: How to Avoid Romance Scam
What Is an Evil Twin Attack? How Does It Work?
How often do we connect to free Wi-Fi networks in public places? Whether to post Instagram stories with a cup of coffee we just bought or to make edits to a project while you’re waiting for your flight. In such cases, the widespread availability of public Wi-Fi is a boon. But this general use of… Continue reading What Is an Evil Twin Attack? How Does It Work?
What is eWallet? How to Protect Your eWallet
During a time of crisis, Americans turned to digital wallets called eWallets to purchase supplies without face-to-face interaction with payment terminals or cards. These wallets make purchasing supplies faster and easier than traditional methods. A common alternative to eWallets is the physical wallet, which is less convenient for many people. In addition, clever crooks and… Continue reading What is eWallet? How to Protect Your eWallet
Beware Snapchat Hacker Attacks: How to Stop Them
There’s a demand for users to secure their privacy and security when using Snapchat. This is due to the fact that it’s one of the most popular social media platforms. Here are the ways hackers usually hack your Snapchat accounts. How Attackers Hack Someone’s Snapchat Account Snapchat does not seem to be the place where… Continue reading Beware Snapchat Hacker Attacks: How to Stop Them
Transport Layer Security (TLS): Difference Between TLS and HTTPS?
Transport Layer Security is a widely used security protocol designed to ensure confidentiality and data security when exchanging data over the Internet. In particular, we use TLS daily to encrypt communication between servers and clients – a common communication for everyone. Meanwhile, people used to hear HTTPS abbreviation regarding the same thing – secure client-server… Continue reading Transport Layer Security (TLS): Difference Between TLS and HTTPS?
How to Browse the Web Securely: Stay Safe Online
Web browsers are invaluable tools for users and make up a huge portion of the daily time we spend in the digital world. Unfortunately, they hold many personal files and information, making them a desirable target for cybercriminals. Threat actors could attempt to access a person’s computer or other computers in the network using attacks… Continue reading How to Browse the Web Securely: Stay Safe Online
8 Top Internet Safety Rules: Cybersecurity Tips
There is a lot of entertainment available online, along with education and social media. However, not everyone understands how the Internet works,and knows something about methods of safe usage. This article introduces some great tips to keep your Internet safety well in your daily things. What is Internet Safety? Internet safety and data protection is… Continue reading 8 Top Internet Safety Rules: Cybersecurity Tips