Researchers have discovered a new form of malware called RedEnergy Stealer. It is categorized as Stealer-as-a-Ransomware but is not affiliated with the Australian company Red Energy. A malware called RedEnergy stealer uses a sneaky tactic to steal sensitive data from different web browsers. Its fundamental spreading way circulates fake updates – pop-ups and banners that… Continue reading RedEnergy Stealer-as-a-Ransomware On The Rise
Tag: Stealer
Super Mario Malware: Hackers Spread Stealers in the Fake Game
The Super Mario video game franchise has gained immense acclaim due to its platforming gameplay, lively visuals, memorable characters. Recently, the franchise has experienced a renewed surge in popularity with the release of new games and animated movies. The franchise has consistently evolved by introducing innovative game mechanics, power-ups, and levels across titles and gaming… Continue reading Super Mario Malware: Hackers Spread Stealers in the Fake Game
GoDaddy Refund Phishing Emails Spread Infostealer
Hackers started using GoDaddy Refund Emails as a disguise to trick the users into installing malware. In order to deploy the payload, they opted for a particularly new tactic or, well, combination of ones. As a payload, a unique free open-source Invicta Stealer is used. GoDaddy Refund Email Phishing Being a widely popular web hosting… Continue reading GoDaddy Refund Phishing Emails Spread Infostealer
Ducktail Infostealer Malware Targeting Facebook Business Accounts
Researchers discovered Ducktail Malware, which targets individuals and organizations on the Facebook Business/Ads platform. The malware steals browser cookies and uses authenticated Facebook sessions to access the victim’s account. As a result, the scammers gain access to Facebook Business through the victim’s account, which has sufficient access to do so. It is a particularly interesting… Continue reading Ducktail Infostealer Malware Targeting Facebook Business Accounts
RedLine Stealer Issues 100,000 Samples – What is Happening?
Throughout the entire early May 2023, GridinSoft analysts team observed an anomalous activity of RedLine stealer. It is, actually, an activity different from what we used to know. Over 100,000 samples of this malware appeared through the first 12 days of the month – that is too much even for more massive threats. Needless to… Continue reading RedLine Stealer Issues 100,000 Samples – What is Happening?
3CX Phone System is Struck With Chain Supply Attack
3CX Phone System, a desktop app for business phone communication, fell victim to a supply chain attack. Recent updates deliver a forged version of the application that makes it possible to install stealer malware. The actual payload is getting delivered in a 3-stage manner, which makes it harder to track. What is the 3CX Phone… Continue reading 3CX Phone System is Struck With Chain Supply Attack
Spyware Attack: Red Flags You’re Dealing With Spyware
Spyware is probably one of the oldest but most dangerous types of malware. As the name suggests, spyware is software that spies on you when using your computer or mobile device. To recognize when you’ve been infected and to take steps to remove spyware, it’s essential to be aware of its possible signs. Unfortunately, just… Continue reading Spyware Attack: Red Flags You’re Dealing With Spyware
Top Working Antispyware Tips 2022
The user risks being compromised by using the Internet. The intruders are still trying to hijack your confidential data and credit card numbers, distribute spyware, and the like. With each passing day, their penetration methods into your OS are becoming more sophisticated, which is something to watch out for. Spyware is one of those ways… Continue reading Top Working Antispyware Tips 2022
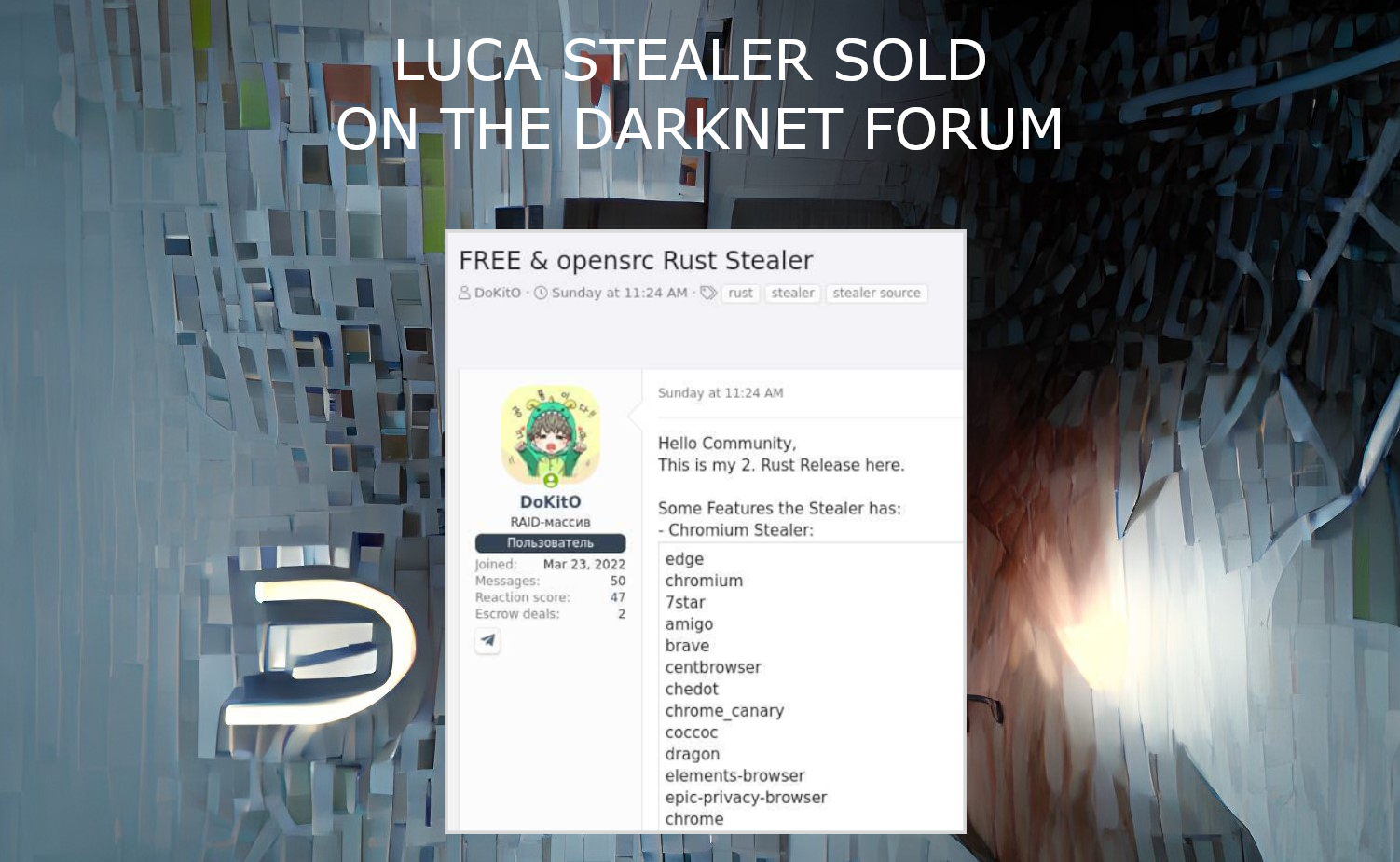
Luca Stealer Source Code Published In The Darknet
Luca Stealer, an omni-purpose stealing malware programmed on Rust, was published on the Darknet forum in recent days. The source code of a well-done stealing tool is now available for everyone. This stealer generally aims at web browsers, particularly the plugins and data that belongs to cryptocurrency wallets and online banking. Luca Stealer functionality As… Continue reading Luca Stealer Source Code Published In The Darknet
Attackers Exploit MSDT Follina Bug to Drop RAT
Security specialists caution users about the exploitation of the recently disclosed Follina Bug found in all supported versions of Windows. Threat actors have actively utilized this vulnerability to install payloads such as the AsyncRAT trojan and infostealer. Understanding the Follina Vulnerability On May 27, 2022, the public became aware of a remote code execution (RCE)… Continue reading Attackers Exploit MSDT Follina Bug to Drop RAT