A new ransomware called “Kasseika” uses Bring Your Own Vulnerable Driver tactics to disable antivirus software before encrypting files. Kasseika was likely built by former members of the BlackMatter group or experienced ransomware actors who purchased its code.
Kasseika Ransomware Deploys BYOVD Attacks
A new ransomware operation known as “Kasseika” has recently been discovered. This threat actor uses Bring Your Own Vulnerable Driver tactics to disable antivirus software before encrypting files. Kasseika exploits the Martini driver (Martini.sys/viragt64.sys), part of TG Soft’s VirtIT Agent System, to disable antivirus products protecting the targeted system.
According to analysts who first discovered and studied Kasseika in December 2023, the ransomware shares many attack chains and source code similarities with BlackMatter. Although BlackMatter’s source code has never been publicly leaked since its shutdown in late 2021, investigators believe that Kasseika was likely built by former members of the group or experienced ransomware actors who purchased its code.
What is BYOVD?
BYOVD, which stands for Bring Your Own Vulnerable Driver, is a technique attackers use to compromise a targeted system. In this method, attackers rely on exploiting a vulnerable driver that arrives at the system together with the payload. Since the drivers are trusted by security software, they are not detected or blocked.
These drivers are typically kernel-mode drivers, which allow attackers to escalate privileges to the highest level of access and control over system resources. Such a trick enables attackers to disable endpoint security software and evade detection. Once the security defenses are compromised, attackers can engage in malicious activities without hindrance.
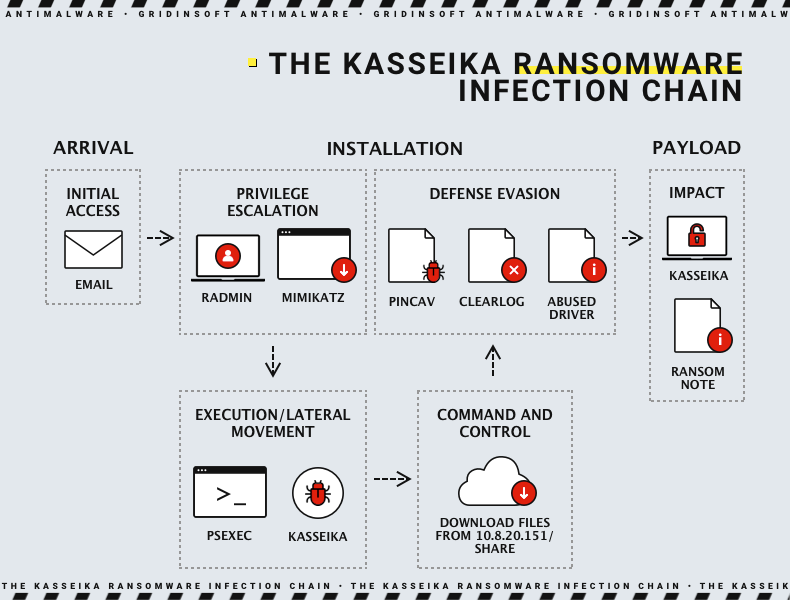
Kasseika Ransomware Attack Chain
Cyber attackers often use a phishing email to gain initial access to a network. Next, they use remote administration tools (RATs) to move around the network and gain privileged access. These attackers typically use Microsoft’s Sysinternals PsExec command-line utility to carry out their attacks. To find a process called “Martini.exe” and stop it, adversaries execute a malicious batch script. This ensures that only one process instance is running on the machine.
Defense evasion
After the initial preparations, the attackers download and run a driver called “Martini.sys” from a remote server. This driver can disable up to 991 security-related elements. It’s important to note that “Martini.sys” is a legitimate, signed driver named “viragt64.sys”. Now, it has been added to Microsoft’s vulnerable driver blocklist. If the malware cannot find “Martini.sys,” it will terminate itself and not proceed with the attack. So the entire attack relies on the presence of this specific driver – a rather indiscreet approach, if you ask me.
Executing payload
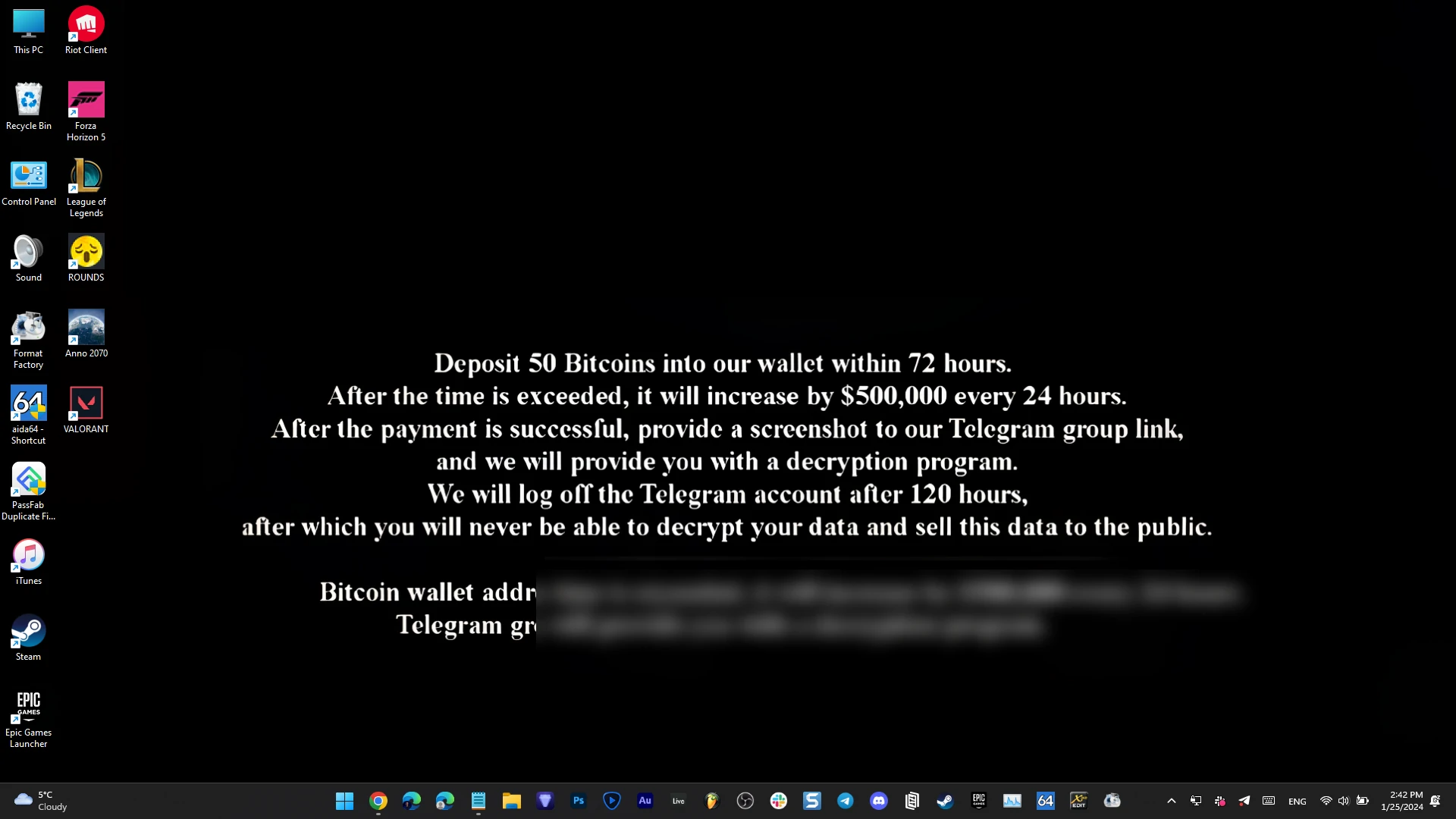
After executing “Martini.exe”, the ransomware payload “smartscreen_protected.exe” encrypts all the files using ChaCha20 and RSA algorithms. It also terminates all the processes and services accessing Windows Restart Manager. Once the encryption is completed, a ransom note is left in every directory that has been encrypted. In addition, the system’s wallpaper is modified to display a note demanding payment of 50 bitcoins to a wallet address within 72 hours. Failure to comply with this demand will result in an additional fee of $500,000 every 24 hours after the deadline has passed.
Clearing traces
The victims must post a screenshot of the successful payment to a Telegram group controlled by the attacker to receive a decryptor. The Kasseika ransomware also clears the system’s event logs using the wevtutil.exe binary to remove any traces of its activity. This technique operates discreetly, making it more challenging for security tools to identify and respond to malicious activities.
Safety Recommendations
Organizations should implement a multi-layered approach to protect against Kasseika and other malware. Here are key recommendations:
- Enhance email security. To improve the security of your emails, it is essential to implement strong email filters that can detect and block phishing attempts. Additionally, educating your employees on identifying phishing and other cyber threats is essential. Regular training sessions can help them recognize phishing emails and malicious websites, significantly reducing the risk of infection.
- Implement EDR zero-trust. Implementing EDR within a zero-trust security framework involves continuous monitoring and verification of endpoints and enforcing strict access controls to minimize the risk of lateral movement within the network. This integration enhances security posture and protects against cyber threats as well as ransomware.
- Update and patch regularly. As software vulnerabilities are a primary concern in enterprise cybersecurity, installing patches is the best option for covering that weak spot. Cost spent on installing the update is nothing compared to the ransom amounts and reputation damage. Keep track of the latest news and patches released by the vendors of the software you use to be sure you don’t have loose things to tighten up.


