Spyware is probably one of the oldest but most dangerous types of malware. As the name suggests, spyware is software that spies on you when using your computer or mobile device. To recognize when you’ve been infected and to take steps to remove spyware, it’s essential to be aware of its possible signs. Unfortunately, just… Continue reading Spyware Attack: Red Flags You’re Dealing With Spyware
Tag: Spyware
Spyware vs. Stalkerware: What’s the difference?
Fraudsters develop various methods to penetrate the property of others, so there are different types of attacks and threats. In this article, we will look at what spyware and stalkerware are, their differences, and how to avoid these programs penetrating your device. What is Spyware? Spyware is well known to the public, whereas stalkerware is… Continue reading Spyware vs. Stalkerware: What’s the difference?
Signs of Identity Theft: How to Prevent It?
Identity theft is a rather unpleasant crime. Cybercriminals can not only empty your wallet but also stalk your digital space and may even use it to commit crimes on your behalf. Since criminals invent new tricks daily, keeping yourself safe is pretty hard. So we’ve set together some essential tips to help prevent identity theft… Continue reading Signs of Identity Theft: How to Prevent It?
Pegasus Spyware — The Most Dangerous Malware
Pegasus Spyware is a malicious program that is covered with multiple layers of secrets, rumours and false claims. That military-grade malware is something like a legend, that sometimes makes people think it is rather mythical than real. Still, the real Pegasus appears from time to time, just to notify everyone that it is still the… Continue reading Pegasus Spyware — The Most Dangerous Malware
Top Working Antispyware Tips 2022
The user risks being compromised by using the Internet. The intruders are still trying to hijack your confidential data and credit card numbers, distribute spyware, and the like. With each passing day, their penetration methods into your OS are becoming more sophisticated, which is something to watch out for. Spyware is one of those ways… Continue reading Top Working Antispyware Tips 2022
Google Report Companies Creating Mobile Spyware for Governments
Google Reveals An Italian Company to Sell Android and iOS Spyware to Governments In its blog, Google has published a report revealing that multiple companies have been crafting and selling spyware exploiting mobile devices’ zero-day vulnerabilities discovered by Google specialists last year. The post includes code fragments from the disputed malware. Over 30 companies turned… Continue reading Google Report Companies Creating Mobile Spyware for Governments
10 Signs That Your Computer Is Infected With Spyware
What Is Spyware? It is a malicious program that secretly gets installed onto your device. Sometimes you can get it by downloading it together with other usually freeware programs and the other cases include someone who installed it on your device by themselves. In the case of freeware you get to download spyware without your… Continue reading 10 Signs That Your Computer Is Infected With Spyware
The 5 Most Famous Spyware Attacks
Spyware can be called the most sophisticated malware these days. It never acts openly, uses tricky techniques, and appears more often with other viruses. Together with its brother-in-law – stealer malware – spyware helps the cyber criminals to find and exfiltrate the data from attacked corporations. Moreover, ransomware that aims at individuals (exactly, STOP/Djvu family)… Continue reading The 5 Most Famous Spyware Attacks
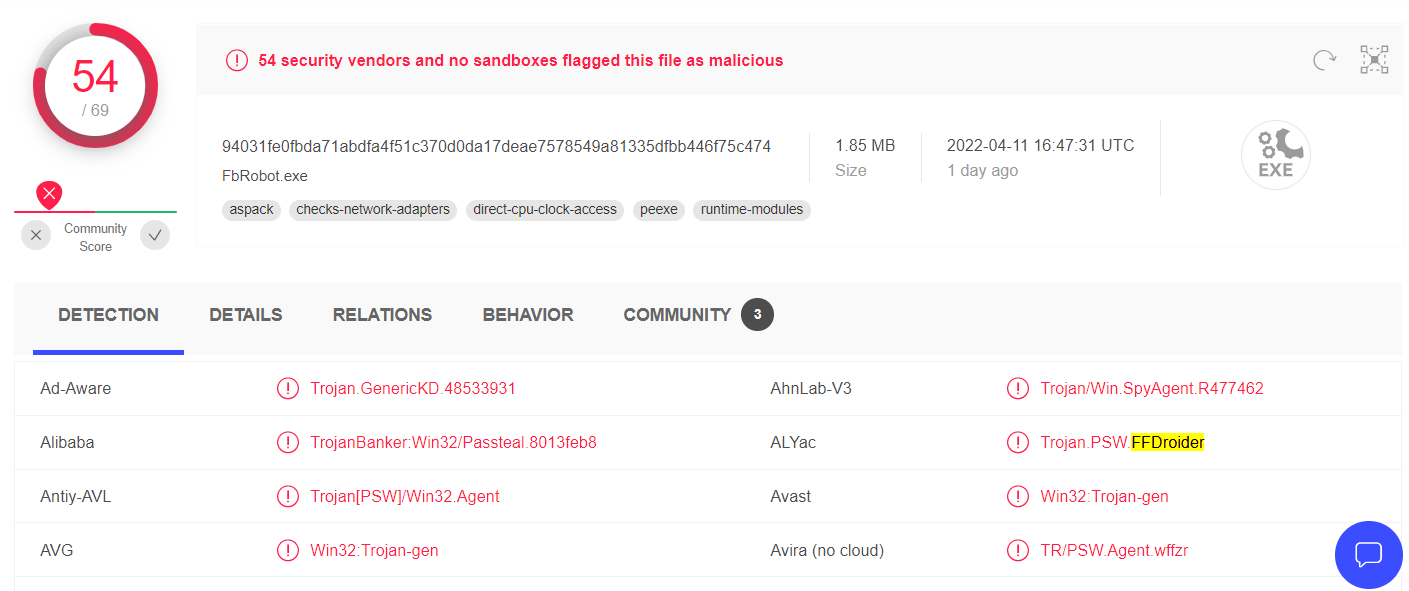
FFDroider Stealer – the new hazard to your social networks
FFDroider is an example of a modern stealer malware that aims at sensitive data in web browsers. The overall amount of new stealers that appeared in the first quarter of 2022 says a lot about the new malware trends. FFDroider Stealer is the second malware of this type that popped out last month. The BlackGuard… Continue reading FFDroider Stealer – the new hazard to your social networks
Meta Infostealer Malware Spread via Spam
Meta, a newly crafted information-stealing malware, is distributed via a vast spam spree. The mechanism of the stealer injection within this campaign is already well-known. However, Meta is now a mainstream tool among hackers. Therefore, further attacks featuring this software but with different scenarios are inevitable. This article explains how the current malspam scheme works.… Continue reading Meta Infostealer Malware Spread via Spam



![Signs of Identity Theft: How to Prevent Identity Theft [Short Guide 2022 ]](https://gridinsoft.com/blogs/wp-content/uploads/2022/09/istockphoto-1279316333-612x612-1.jpg)