Experts from the Gemini Advisory company published a report, according to which on underground hacker forums were found two precedents, when hackers collected EMV card data and put this information up for sale. Thus, attacks on EMV cards, which were only a theory 12 years, have been noticed in reality.
The ZDNet publication says that just recently analysts at Cyber R&D Lab conducted an interesting experiment related to EMV cards.
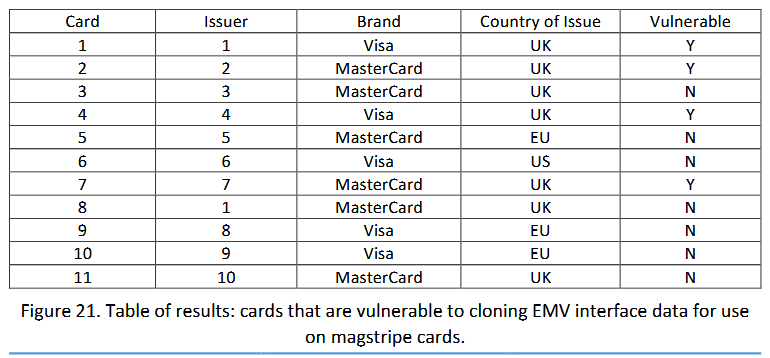
The researchers issued EMV cards with a chip in 11 banks in the US, UK and EU, and then used hacking tools against them, which are usually used to copy information stored on EMV cards and their magnetic stripes.
As a result, the researchers were able to extract data from EMV cards and created clones with the same magnetic stripe, but without the actual chip.
“This became possible due to the fact that all EMV-cards have a magnetic stripe just in case, for example, for a situation when a user has gone abroad and cannot use EMV, or there is an old PoS-terminal”, – told ZDNet journalists.
The fact that it is possible to copy the magnetic stripe of EMV cards has been known since 2008, but it was believed that this feature could hardly be abused, since banks planned to transfer all users to EMV and often refused to use magnetic stripes. As practice has now shown, this did not happen, and Cyber R&D Labs specialists reported that they managed to clone four cards in the above described way and carry out transactions.
However, until this week, the problem was still considered rather theoretical, since it was not known about the massive use of this technique by hackers, and now experts at Gemini Advisory have discovered such precedents.
The researchers write that the EMV cards data were stolen from the American supermarket chain Key Food Stores Co-Operative Inc., as well as from the American liquor store Mega Package Store.
The fact that criminals have begun cloning EMV cards seems to be confirmed by the warning, issued by Visa. Visa representatives write that malware such as Alina POS, Dexter POS and TinyLoader have been updated and can now collect information from EMV cards, which has never been seen before, since the data collected in this way usually could not be monetized.
Gemini Advisory believes that the method that criminals began to use was described as early as in 2008, and that this technique, EMV-Bypass Cloning, was the subject of recent research by Cyber R&D Labs.
“I demonstrated cloning from chip data to magstripe, but the banks said that cards issued after 2008 would not be vulnerable and chip data would be “useless to the fraudster ”. This new research shows that the problem still has not been fixed, 12 years on”, – said engineer Steven Murdoch, who described the cloning technique in 2008.
In theory, it is not too difficult to defend against such attacks: it is enough for banks to conduct more thorough checks when processing transactions from magnetic stripes of EMV cards. However, unfortunately, as a study by Cyber R&D Labs has shown, not all banks pay attention to this.
By the way, here the hacker Tamagotchi instantly collected on Kickstarter an amount 7 times more than necessary – hacking is in fashion, and your personal data, including bank accounts and cards, is always in danger. Let me also remind you that BlackRock Trojan steals passwords and card data from 337 applications on Android OS.