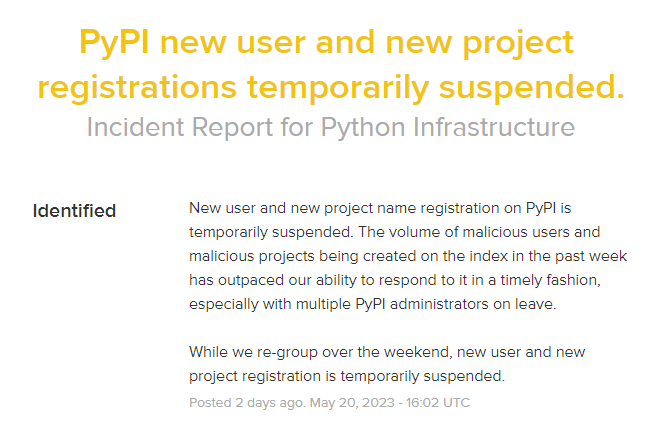
Python Package Index, a software repository for Python developers, recently faced a massive attack. An enormous flow of malicious uploads forced the administration of the project to suspend both new uploads and new users registration. This crisis peaked on May 20, 2023, when project masters released the note regarding the current state of things.
What is the Python Package Index?
Python Package Index, mostly known under the abbreviation of PyPI, is a third-party project that serves as code solution repository for Python. It emerged in 2002, in the form of a centralised Internet catalogue of Python packages. The developers who use Python highly appreciate this source, and for most of its users, it has become as trusted as an official one. As of the beginning of May 2023, over 450,000 packages were available on this resource. As you may suppose, administering such a massive flow of packages for various purposes is not an easy task, even though there are a bunch of rules of uploading.
PyPI Faces Malicious Packages Outbreak
Since May 20, PyPI admins restrict the new users registrations and submissions of new packages for existing ones. They lifted the restrictions on May 22, after clearing the issue. However, wiping them out is not a solution to a problem, it’s just healing the symptoms. Situation will appear over and over again, just because hackers will not stop that easy. Preventing further malware spreading via PyPI may require introducing a more complicated system of package control.
The situation around malicious items circulating in PyPI is not new. Same thing was happening for years, yet with way less volume of uploaded malware. It is quite obvious that the place where that big number of packages are stored may be a point of interest for hackers. Upload a malicious package, promote it in one or another way, and harvest the victims. Malicious code may be used to compromise not only the machine of a user who downloaded it, but also to launch a supply chain attack. The latter, apparently, turns into a new malware spreading trend.
Putting malware into supplementary packages used by coders appears to be another new-old trend. Recent discovery of malicious Visual Studio Code plugins in VSCode Marketplace is a perfect example. More rigorous moderation and way less popularity of the Marketplace allowed its masters to operatively dispatch the threats – but who knows what may happen next.
How to protect yourself?
By now, the administration of the PyPI project did not release any instructions about the protection for their users. And it is expected, as such attack vectors are quite novice. I have a couple of thoughts about possible countermeasures – let me share them.
Check all the packages you download for malware. Fortunately, there are a lot of online sandboxes that allow you to scan the files. VirusTotal, Any.Run – you name it. However, they have file size restrictions, which make it impossible to scan large (or intendedly bloated) projects. Apparently, the only bypass here is to review the code in the debug environment – though it requires certain skills.
Review the source. There are numerous trusted and clean packages that hackers are trying to mimic. Namesquatting and typosquatting are most typical methods – search carefully to avoid it. User feedback in the comments is another source of information. Upload date and the publisher can give you even more clues – new packages from a no-name developer that mimic well-proven ones should not be trusted at all.
Use an anti-malware program with an advanced heuristic detection engine. Static detection, i.e. one that bears on signatures, may be useless against the newest threats. Meanwhile, an anti-malware program that can check the threat from another side is essential. GridinSoft Anti-Malware features a proactive protection that can dispatch the samples that were released 5 minutes ago – simply by their behaviour.