Experts from ReasonLabs have discovered an unusual malicious scheme that has been operating since 2019 – carders used fake dating sites to steal and launder funds.
Also read our article: Signs You’re Dealing with an Online Scam.
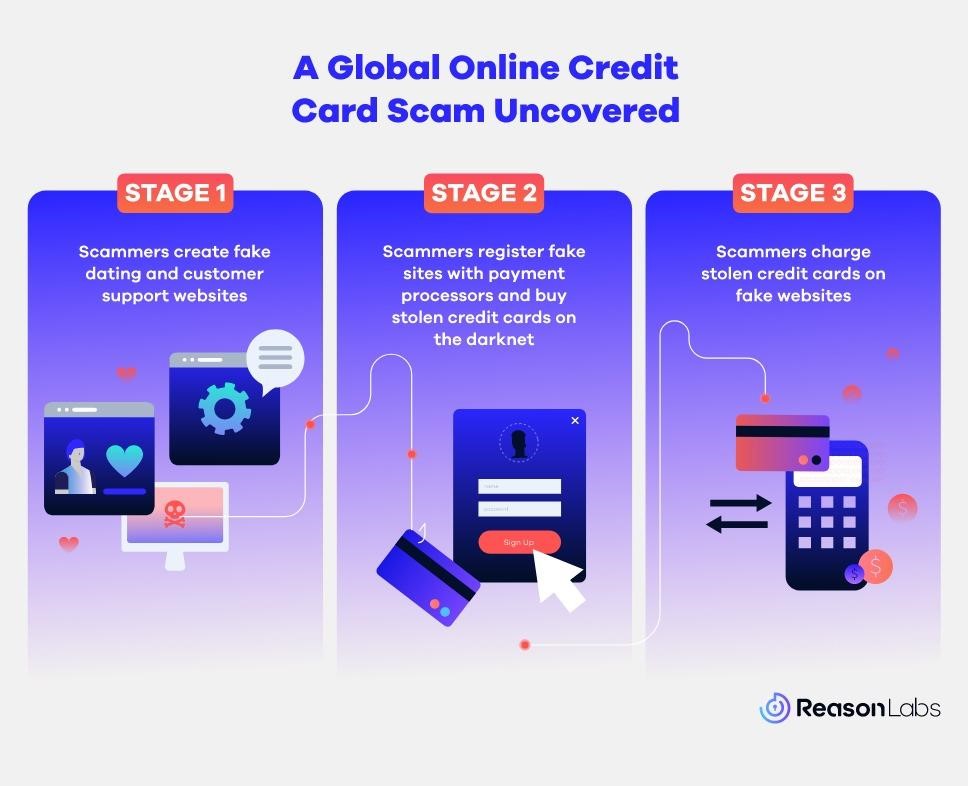
According to researchers, with its help, hackers stole millions of dollars from tens of thousands of victims. It turned out that the attackers operate a in large network of more than 200 fake dating and customer support sites, and use these resources to debit other people’s bank cards bought on the dark web.
This campaign uses two types of domains: dating sites and customer support portals (list of addresses can be found in the company report). If you try to visit the websites of the companies that allegedly own these fake resources, you will find that they do not exist at all, or they use non-existent email addresses, such as [email protected].
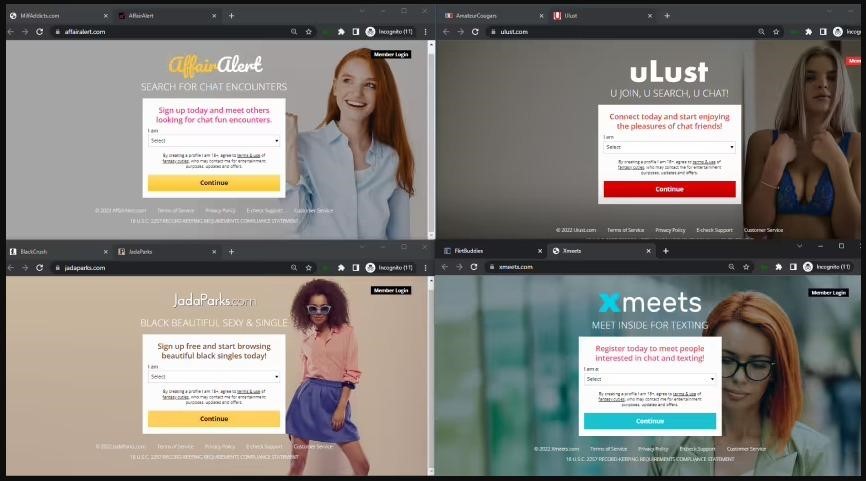
Fake dating sites
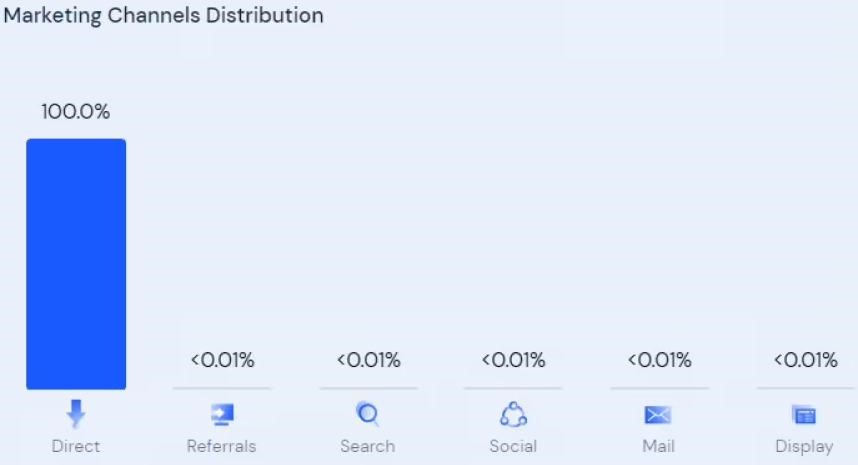
At the same time, dating and customer support sites look viable, but receive almost no traffic, occupying low positions in Google search results. The fact is that they exist not to attract users, but to serve as channels for money laundering.
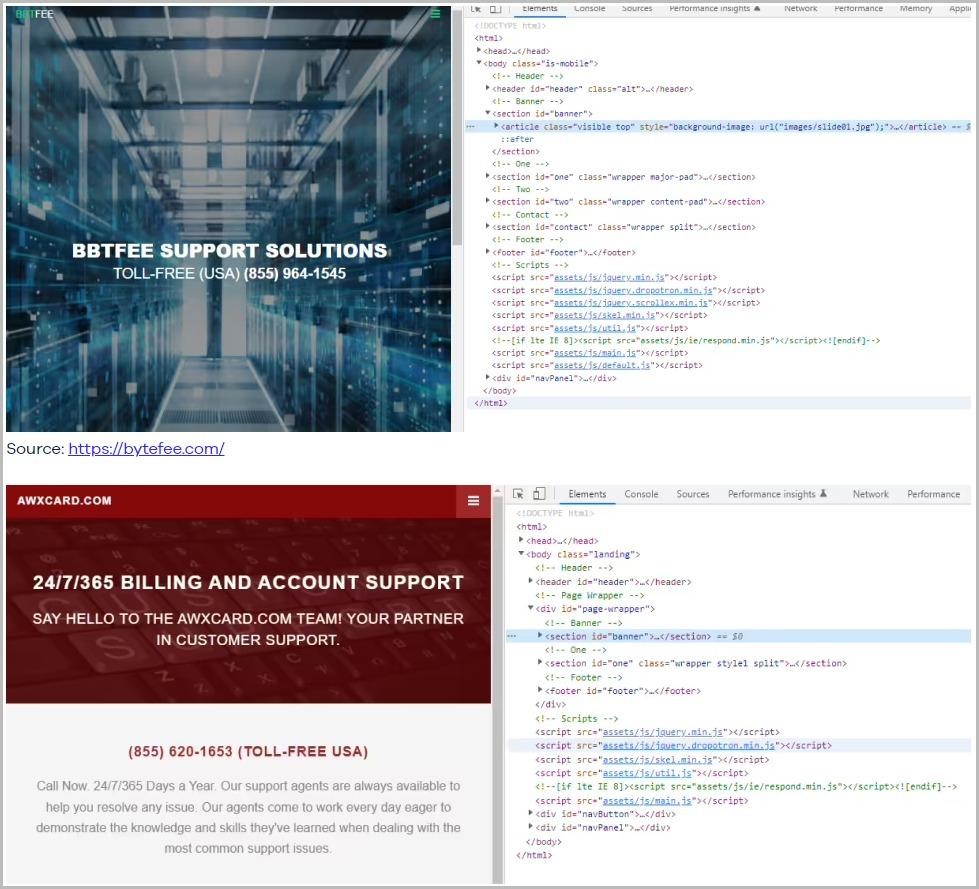
ReasonLabs analysts write that all sites have the same HTML structure and almost the same content, so it looks like they were created using automatic tools. At the same time, fake customer support portals often use the names of non-existent organizations, or try to resemble real brands such as McAfee, ReasonLabs and other firms.
It is also noted that the operators of this campaign seem to have gone to great lengths to hide all 75 fake support portals from being indexed by search engines using the anti-crawler instructions in Robots.txt.
But the biggest challenge for attackers is registering these sites with payment processors, who usually classify them as “high-risk” (even if it’s a legitimate resource) due to their high chargeback rates. In order not to be blacklisted, each site applies individually, as campaign operators are afraid of losing all resources at once if fraud is detected.
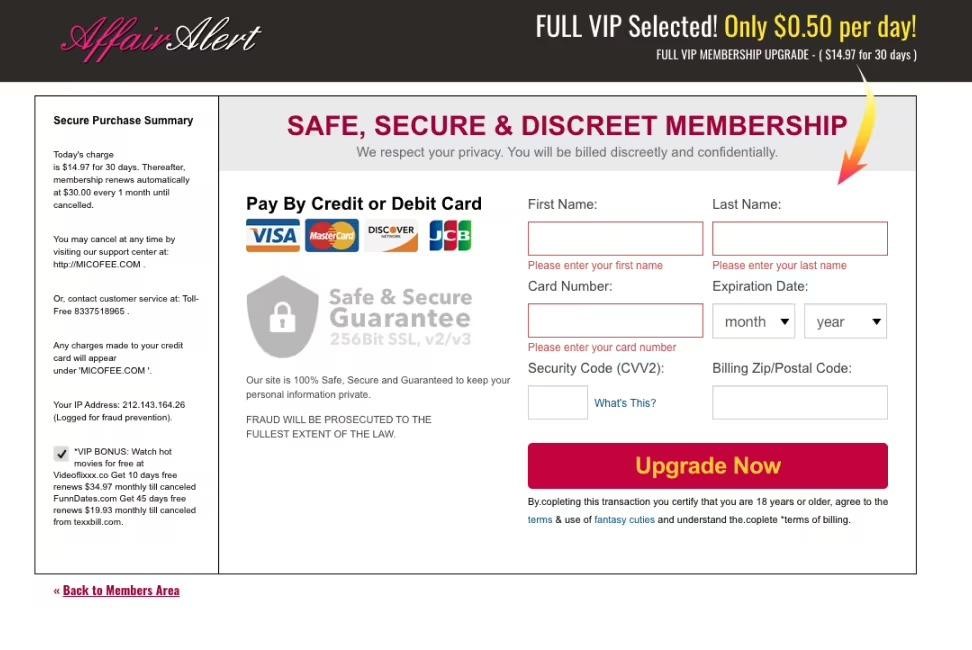
If resources need to prove their legitimacy, then all sites have a round-the-clock chat with support and a working phone, outsourced to a real call-center. In addition, all sites list a toll-free number in case users want to cancel a payment, which scammers usually do not offer.
Once the payment processor has approved the request, the hackers use millions of stolen payment cards purchased on the dark web and debit them through their fake websites. Most of the cards belong to residents of the United States, but it is also reported that hackers bought cards from French-speaking countries.
Site operators are very careful and try not to draw attention to themselves. They withdraw small amounts, use common names that can get lost among the victim’s other expenses, use recurring payments with the same amount, and avoid test transactions.
Payment page on one of the scam sites
What’s more, in some cases, the hackers even refund the victims, making their transactions more authentic and making the charge-back ratio seem low.
While many of the 275 bogus sites are still up and running, ReasonLabs experts have already notified payment processors and law enforcement of their findings.
You may also be interested in: 8 Best Practices How to Keep Your Windows 10 Computer Secure in 2022.