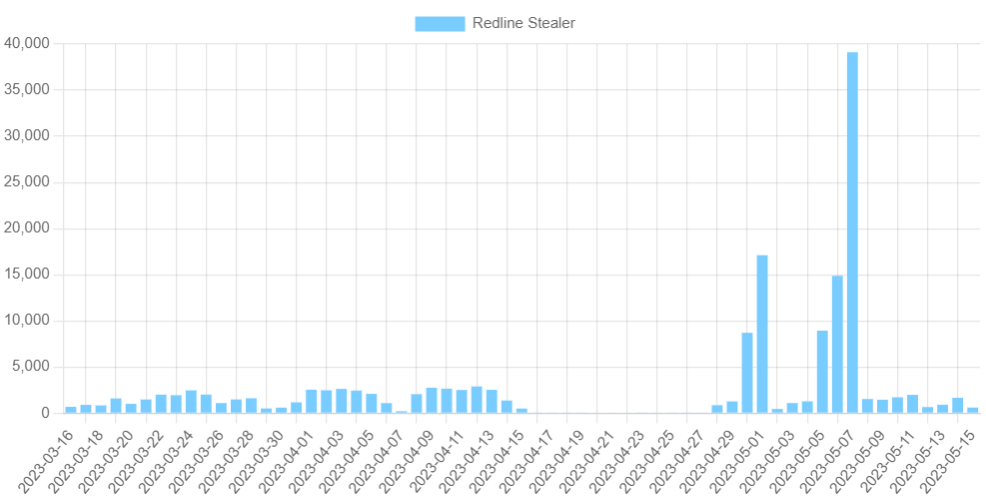
Throughout the entire early May 2023, GridinSoft analysts team observed an anomalous activity of RedLine stealer. It is, actually, an activity different from what we used to know. Over 100,000 samples of this malware appeared through the first 12 days of the month – that is too much even for more massive threats. Needless to say for stealer malware such a massive outbreak is confusing, to say the least.
What is RedLine malware?
First, let me remind you what RedLine is. It is a classic infostealer that targets cryptocurrency wallet credentials, browser AutoFill forms, cookies, and credentials from other applications. The most common way of spreading this malware is spear phishing, which contains infected files and phishing links. Another option used by malware masters recently is malvertising through Google Search ads. The latter supposes the creation of a website that replicates the downloading page of a legit free software – like 7zip, OBS Studio or LibreOffice.
Emerged in early 2020, RedLine had moderate activity throughout its lifespan. The first noticeable activity happened only half a year after the first sample detection – meaning its developers were raising their malware from scratch. But now it made an enormous spike, that peaked on May 7 – over 39,000 samples emerged that day.
What does that mean?
Actually, almost a hundred thousand samples do not correspond to 100,000 victims. RedLine malware toolkit offers sample recompilation and its developers recommend compiling a fresh sample for each attack. That makes every malware unit unique, which makes it way harder to detect by classic anti-virus programs. Encrypting utility, which is also recommended by the malware developers to use, makes it even tougher.
Sure, some of these samples are definitely used in ongoing attacks. RedLine bears on continuous operations and botnet expansions, which requires retaining high infection rates. “Background” activity of this malware is about 1,500 samples a day – meaning most of them are used in actual attacks. Meanwhile, no huge infection spikes were detected recently, at least not of the scale of the sample generation.
The most concerning hypothesis is that RedLine is getting ready for a massive attack. How will this attack be conducted – this is about to be guessed or seen, yet cybercriminals rarely betray their “classic” spreading ways. Email spam, especially precision-made ones, remains very effective and exceptionally cheap – so why would they reinvent the bicycle?
Another possible occasion is way less dramatic, yet does not mean that the threat is over. Such a massive sample generation may be an outcome of some tests – for example, ones done to test the compiler, crypto, or other mechanism. Neither me nor any other analyst can know for sure what exactly they test, but these changes may have qualitative differences. The best way to understand what that means is to spectate, fortunately, these maneuvers do not disrupt threat intelligence in any way.
IoC RedLine Stealer
- Spy.Win32.Redline.lu!heur: 78df5dd27086d25674a6b62028226b22b87a9a35c719324f6ed25618babb8409
- Spy.Win32.Redline.lu!heur: 0855a642a88abca0d504328addc0c43c70316540f768b669e4dfaf8de8d87f4e
- Trojan.Win32.RedLine.mz!n: acbb3d54b4392443037ed3ecb35d079cb2a9b11f914b3ee74f9ad2de1aee6ee3
- Malware.U.RedLine.tr: f4d1b970bc9e5d319c5432be9e3863b5a20bf26e557c8cea6f3949df0012cf01
- Malware.Win32.RedLine.tr: 80f306d656669534f8996c5b83c6b0c1aa87e0097bac53b79d8ec30550ea5e44
- Spy.Win32.Redline.lu!heur: d62fc9601bbf082cd097af67c9a6b74179a636c8dbf8ac04f614df2a6c0c9fe6
- Malware.U.RedLine.tr: 77436bfe8498d733a09f07608054731d5f7ddb28e56ea7166c89fbae134fe334
- Trojan.Win32.RedLine.mz!n: acbb409f6fbe45fe6be7346c2d5ef43b86e095b2f63fe83d3edb4d3ca9eb4d7b
- Malware.U.RedLine.tr: 156a6f7f50aab5d04e30ddbaee8557857f48b5386d09150b178693731eac7b35
- Spy.Win32.Redline.lu!heur: bb69aa08bdbcaa8860d26feaa036760b683f0e164fb18b5a772f0c4321e63b1d
How to stay protected?
I’ve already mentioned preferred spreading ways that RedLine has used since its emergence in 2020. Protective measures should be built around counteracting these methods. And, of course, as the last line of defense, there should be anti-malware software.
Perform a diligent check for each email you receive. It may look like a too paranoid measure for messages, but be aware – it is not about “just emails”. The number of cyberattacks on companies of all sizes done through email spam is terrifying, thus such a threat should not be ignored. Any questionable attachment, link, or strange email address of a sender is a red flag.
Use network monitoring tools. Both active and passive will fit, as RedLine does not apply complicated anti-detection methods. Still, it tries to spoof the traffic path during the C2 communication – and here is where protective solutions shine. Firewalls are much cheaper and easier to set up, but lack reactive response capabilities. Meanwhile, NDR solutions trade their complexity and expense for the ability to intercept even the most novice threats.
Anti-malware software – the last argument of kings. The ideal network security situation is preventing malware from making its way to the live workstation. Though idealism is sometimes synonymous with naivety. For that reason, a thing to back up your security is essential, both if you’re a home user or are connected to the corporate LAN. GridinSoft Anti-Malware is a great choice for home protection, though it will be better to seek a specialized option to protect an entire network.