Throughout the timeline of the trojan virus evolution, it obtained a lot of different forms. They have become global malware that can exploit your computer as it wants. In this article, I will tell you about the particular type of trojan virus – Trojan Coin Miners, also known as “Coin Miner Virus”. Coin miners: essence,… Continue reading Coin Miner – What is it?
Author: Polina Lisovskaya
I have been working as a marketing manager for many years and I like to look for interesting topics for you
5G and it’s possible effect on our lives
5G networks are declared as an amazing technology that can allow us to use different options of ultra high speed connection. The biggest 5G network in the world is located in China, where people can feel the 5G effect in summer 2020. But a lot of problems were uncovered after such massive testing. One of… Continue reading 5G and it’s possible effect on our lives
How To Use Public Wi-Fi Safely: Risks To Watch Out For
In a world where almost everything comes with a price it’s sometimes nice to have at least free wifi. But starting with such a poetic intro here actually comes the real concern: how to use Wi-Fi for free and keep your data private. Many people don’t realize it but using public Wi-Fi puts you at… Continue reading How To Use Public Wi-Fi Safely: Risks To Watch Out For
Who stands behind cyberattacks? Top 5 types of attackers
When accessing the internet, we are often introduced to seemingly wonderful websites, which we think would assist us with our internet surfing, and we often fall into the trap of thinking that these websites are save to use. In addition to that, it is advisable to us to install a number of web applications to… Continue reading Who stands behind cyberattacks? Top 5 types of attackers
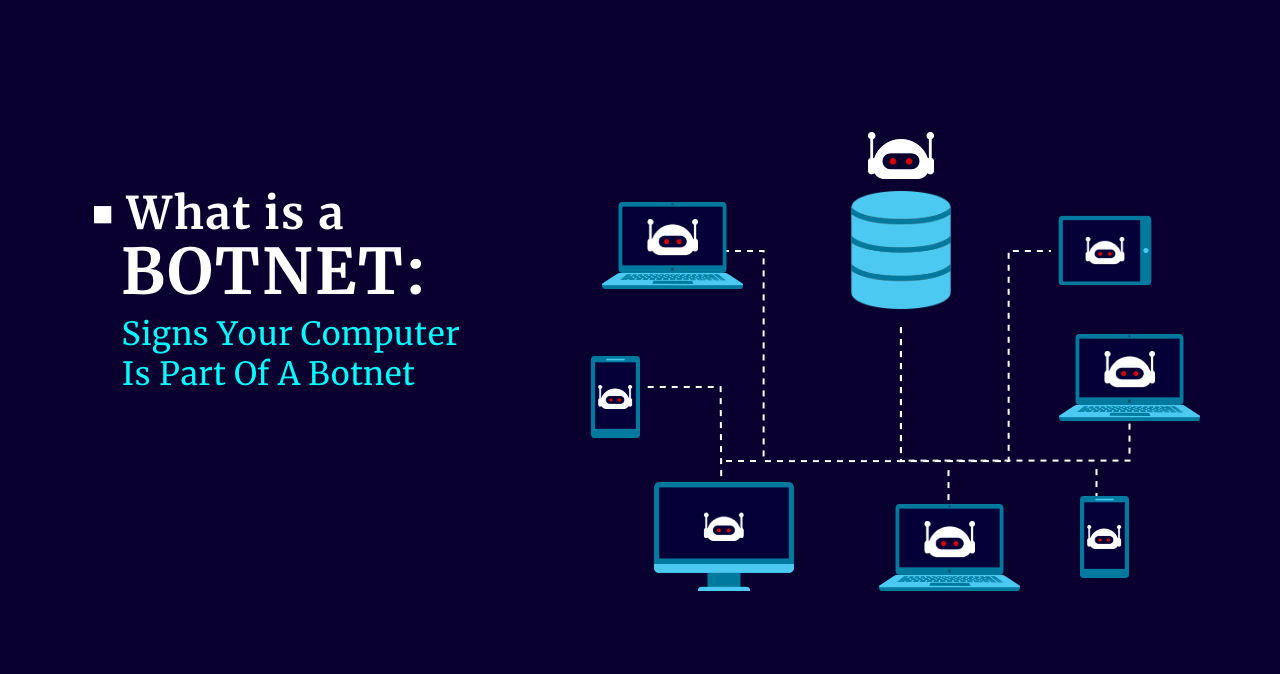
What is a Botnet: Signs Your Computer Is Part Of A Botnet
Botnets are a new reality that seems to have somehow imperceptibly swooped upon us. In fact, the first documented botnet – a network of bots – was created as early as 2001. Today some botnets include tens of millions of machines. And these computers perform the tasks they are given in complete ignorance of their… Continue reading What is a Botnet: Signs Your Computer Is Part Of A Botnet
How to clean space on your Windows computer?
Nothing is more annoying than receiving a notification about your device’s storage being full. You delete some software, your favorite music, and some memorable pictures but, still, the storage seems to remain full. It is a hair-pulling moment. But, you can solve this problem on your Windows by following the easy steps given below. You… Continue reading How to clean space on your Windows computer?
How can you enhance the security of your browser?
Which is the most secure Web browser? Google Chrome? Mozilla Firefox? Microsoft’s Edge? It’s a simple question but the answer is quite complicated. Five years back a poll was carried out and results shows security-conscious browser users overwhelmingly voted Firefox as the most secure. But during the annual Pwn2own hacking contest in March 2014, Firefox… Continue reading How can you enhance the security of your browser?
How To Fix a Computer That Randomly Restarts
Modern computers have working stability much higher than the stability of the computers in the late ‘90s – early ‘00s. Nonetheless, nasty bugs sometimes make us frenzy, because they make the working process problematic. Besides the BSODs and malicious software, there is a thing that is much harder to understand – constant PC rebooting. Be… Continue reading How To Fix a Computer That Randomly Restarts
Google Fined Record €4.3 Billion for Abusing Dominance in Smartphone Market
On July 18, 2018, the European Commission announced that it had fined Google €4.3 billion for violating EU competition rules. The fine was imposed after an investigation revealed that Google had abused its dominance in the smartphone market by requiring phone manufacturers to preinstall its apps on Android phones. The European Commission found that Google… Continue reading Google Fined Record €4.3 Billion for Abusing Dominance in Smartphone Market
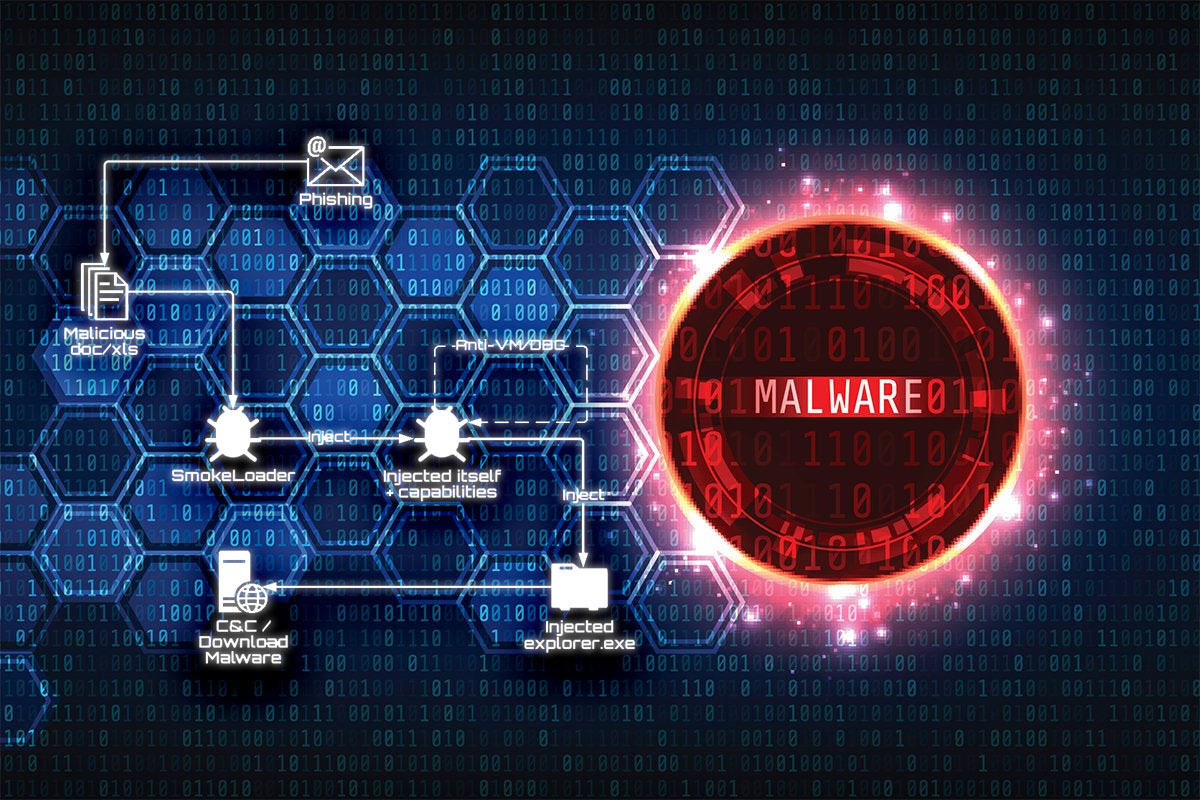
Smoke Loader Malware: New Password-Stealing Infection Method
A new variant of the Smoke Loader malware has been discovered that uses a new method to infect computers. Smoke Loader is a sophisticated malware that has been around since 2011, but it continues to evolve and adapt to new security measures. The new infection method involves the use of spam emails that contain a… Continue reading Smoke Loader Malware: New Password-Stealing Infection Method