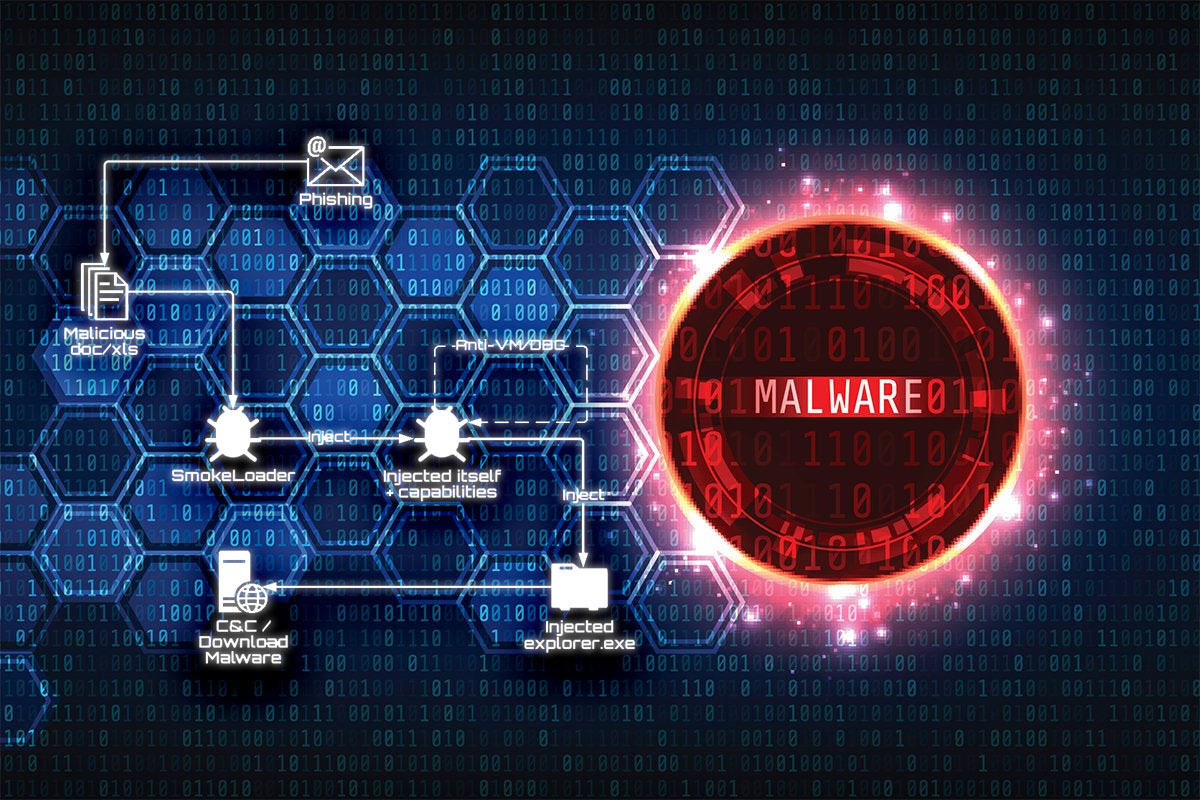
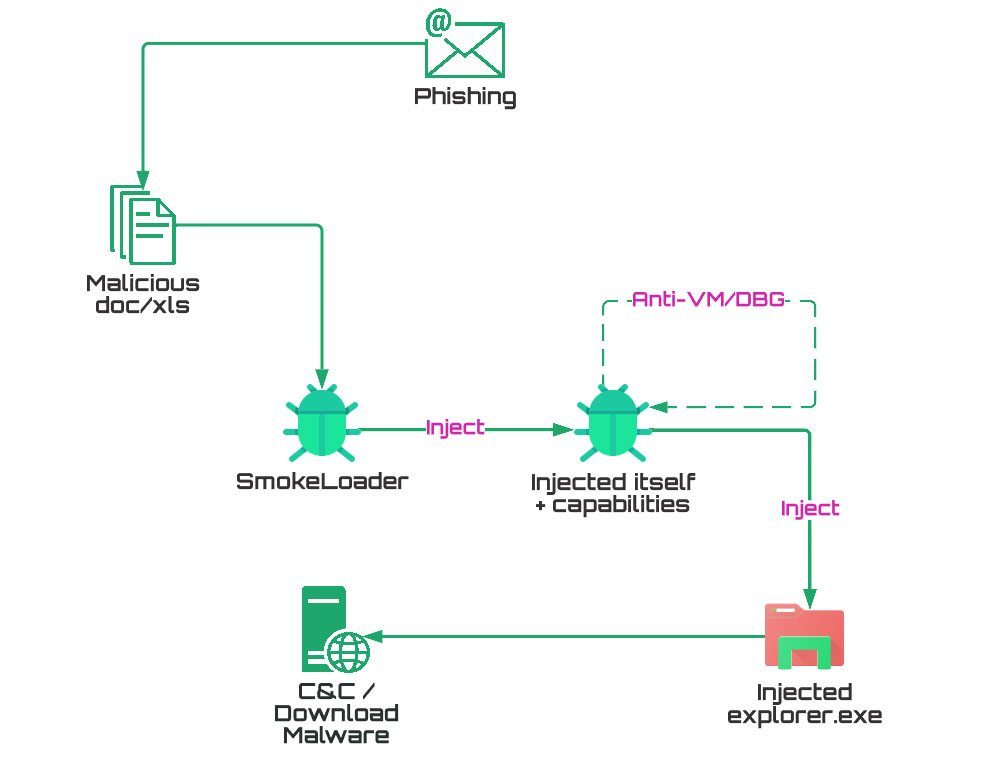
A new variant of the Smoke Loader malware has been discovered that uses a new method to infect computers. Smoke Loader is a sophisticated malware that has been around since 2011, but it continues to evolve and adapt to new security measures.
The new infection method involves the use of spam emails that contain a link to a malicious website. When a user clicks on the link, it downloads a file that appears to be a PDF document but is actually an executable file that installs the Smoke Loader malware on the computer.
Once installed, the malware can steal sensitive information from the infected computer, such as login credentials, banking information, and personal data. It can also download additional malware, making the infection even more dangerous.
Smoke Loader is designed to evade detection by traditional antivirus software. It uses a variety of obfuscation and encryption techniques to hide its presence on the infected computer.
To protect yourself from this type of malware, it is important to be cautious when clicking on links or downloading files from unknown sources. You should also ensure that your antivirus software is up-to-date and that you are using a firewall to block incoming traffic.
IoC Smoke Loader
- Trojan.Win32.SmokeLoader.tr: 7bfa7bde491d5bca80f14118e187dfab173fee1dc9a25138c36af44ea6df246e
- Trojan.Win32.SmokeLoader.bot: a7f605d4110bba430e02c7c5240e656fb3f1dd7f02dce985e9e5677169c9de55
- Trojan.Win32.SmokeLoader.bot: cc58ad1f7a097f077f06b78e21c1f5a01007cd98613b602bb22b95751920ba80
- Trojan.Win32.SmokeLoader.bot: 143310670009099214b1b1a812e98a485db3e2879ab35dca8ba63005a62a610c
- Trojan.Win32.SmokeLoader.bot: 980a736f3c959e814619ab185cf89fd17a930774f11aa06ca79e263be6d077c9
- Trojan.Win32.SmokeLoader.bot: 109d9077e847550b471e717986dec00400d4a49cccf438a462ec9630eda654c5
- Trojan.Win32.SmokeLoader.bot: 0c1f4caa4168d458ffedcd65213253b42d972964ea78d042d4c560d8a71973bc
- Trojan.Win32.SmokeLoader.bot: 47c6cee60f89a6562df66731d25bb8992e1b4cf125d871895808946fa69a501e
If you believe that your computer may be infected with Smoke Loader or any other malware, you should immediately disconnect it from the internet and run a full system scan with your antivirus software. You should also change any passwords that may have been compromised and monitor your bank accounts and credit card statements for any suspicious activity.
In conclusion, the discovery of this new infection method for Smoke Loader is a reminder of the ongoing threat posed by malware and the importance of taking proactive measures to protect your computer and personal information. By following best practices for online security and staying vigilant, you can help minimize the risk of falling victim to these types of attacks.