U2K ransomware, probably the rising star on the ransomware arena, appeared on July 10, 2022. It instantly infected a huge number of users and keeps spreading, despite the massive alarms in cyberspace.
U2K ransomware (U2K files encrypted) – what happened?
Numerous analysts report the analysts about the new ransomware variant stomping the users’ devices. It likely uses the same distribution methods as most of other ransomware families – via software cracks and dubious tools, spread through the torrent downloadings. Still, there are no details about the spreading way, since the threat is only 4 days old. However, it already struck over 10 thousand users – an enormous number for a no-name ransomware. There are several similarities with the other ransomware variant that does not belong to any family – MME ransomware – but it was far from being so widespread.
The other ransomware variant that was dominating the ransomware market in recent years – STOP/Djvu – was pushed down at the moment, as its latest HHEW variant barely scored 5k infections. Such news is overwhelming, since Djvu ransomware was a complete monopolist among ransomware groups that attack individual users. It accounted for over 70% of all attacks on single users, and such a high share was constant for over 2 years.
U2K files – how to decrypt them?
Currently, cybersecurity analysts consider that there is no free way to decrypt the files after the U2K ransomware attack. It likely uses the AES ciphering algorithm, typical for other ransomware. Even if it has certain flaws that make it possible to decrypt it, it will take a certain amount of time to uncover these breaches and make them exploitable. As of now, neither brute force nor decryption tools can do anything with the encrypted files. If there are no breaches in the AES mode crooks applied in the ransomware, it will take millions of years to find a key with brute force.
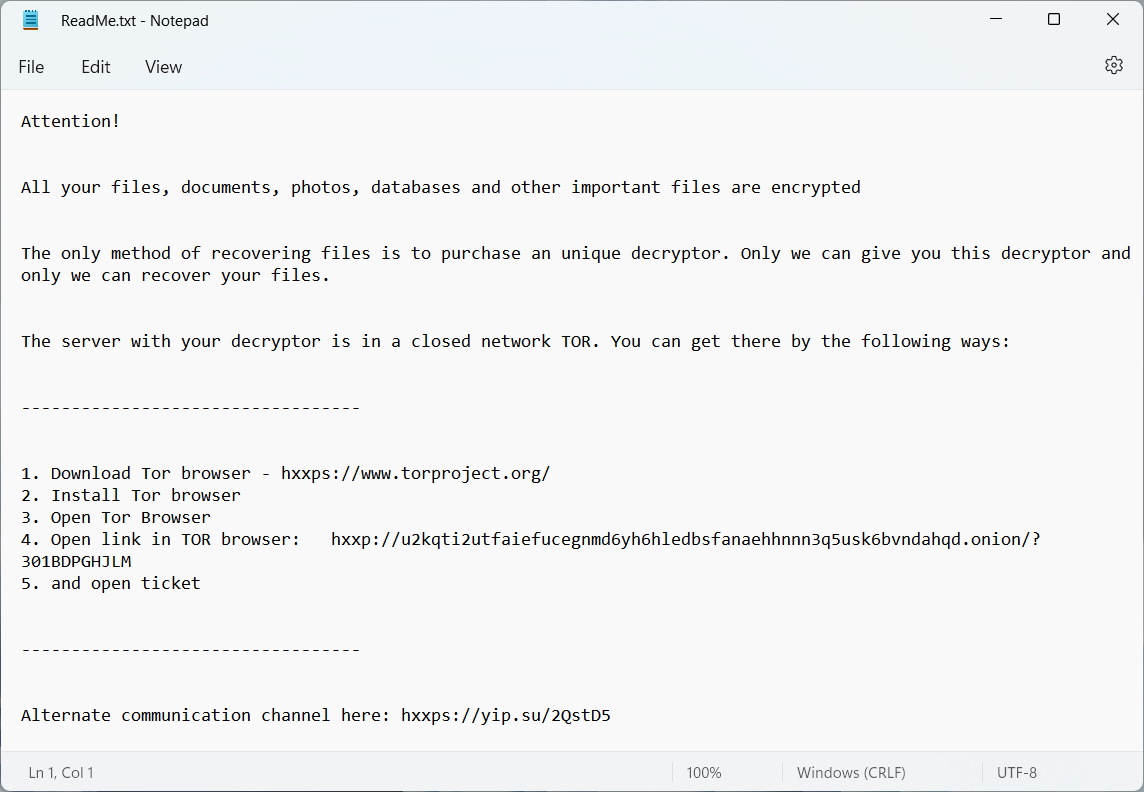
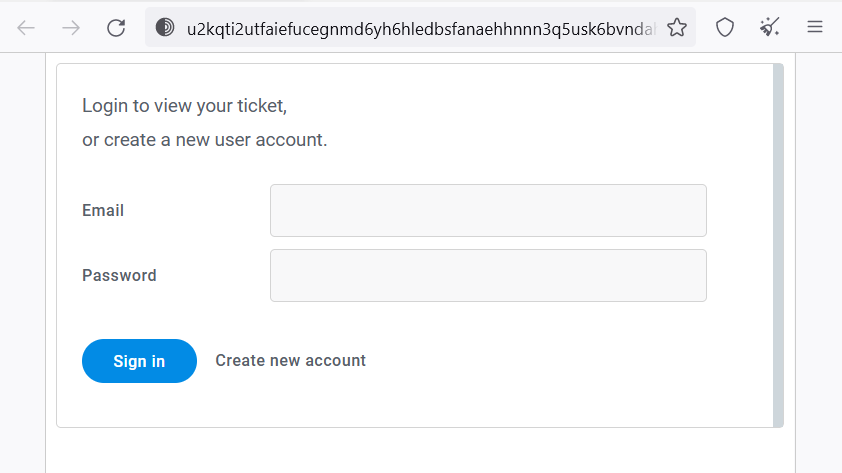
After finishing the encryption process, this malware adds to each file its specific extension (.U2K) and leaves a ransom note on the desktop. In the ReadMe.txt file, the victim will see the link that leads to the Darknet page. Other rows ensure that there is no way to get the files back, and all the victim has to do is to contact the crooks to agree to the payment. The full contents of the ransom note are the following:
Red Stealer comes together with U2K ransomware
Analysts who had a look at U2K ransomware file notice that there is a stealer malware that goes together with the main payload. This tactic is not new, as most of the modern ransomware examples do the same. In particular, STOP/Djvu ransomware brings Azorult spyware to steal the victim’s credentials. Having the spyware or stealer in the bundle does not always mean the double extortion – the credentials hackers receive will then be used directly to hijack your accounts in social networks. Hackers don’t notify you about that, and don’t give you a chance to buy-off your login info.
The ransom size is likely individual for each victim. Crooks name the sum after the conversation on the Darknet site, where you should create the ticket (like in the tech support) and wait for the response. That is not typical for the rascals who aim at individuals as well, since communication through the Darknet is a prerogative of the groups that aim at corporations. For the latter it is essential since the ransom sum is obviously unique for every hacked company, and haggling is allowed. Among gangs that attack individuals, only Magniber ransowmare practices this trick.
How to protect yourself?
Ransomware is considered one of the most dangerous viruses nowadays. It is better to avoid it at all rather than getting ready to solve the post-attack issues. Fortunately, it uses pretty straightforward delivery methods when it tries to break into the sole users’ PCs. Still, it will be much better to have all measures taken regardless of the possibility of the attack.
- Don’t use software cracks and dubious tools. These two are probably the most popular malware spreading ways, and the longest lasting ones. Malicious applications can have different disguises, but most often they hide under the guise of the apps that ask you to disable the antivirus to be installed.
- Avoid the offers on forums. You can sometimes find extremely generous offers on different forums – like a free key for the certain application. When you are not sure about the personality of this user, it is better to avoid such offers. It is especially recommended when you visit that forum for the first time, searching for the solution of the problem.
- Use anti-malware software. A proper anti-malware program will stop even the newest ransomware variant with the heuristic engine. It will also prevent you from getting into traps of this kind. GridinSoft Anti-Malware is a great security program that can protect you from several directions.
- Apply using advanced backup tools. Most of the ransomware variants can disable the general backup utilities, like System Restore, Onedrive or Volume Shadow Copy. However, it is useless against the copies of important files on the removable drive, or when you store the backup on the cloud storage.