Aggregatorhost.exe is a process in the Task Manager that is also often suspicious to users. Due to its uncertain nature, it can appear to the users as a malicious process, but it is not (at least, not usually). Below, I will tell you what this process is, what it refers to, and whether you may have a reason to distrust it.
What is AggregatorHost.exe?
The Aggregatorhost.exe is a system process that you can occasionally spectate in the Task Manager. I should note right away that this is a legitimate Windows process related to Windows Defender and Windows Update functionality. Originally, this process belonged to the Windows Evaluation Program, and helped to test features before they are released to the public. Aggregatorhost is responsible for collecting and submitting user feedback and telemetry data from participants in the Windows evaluation program.
Since its functions are not always performed, the process may periodically appear and disappear in the Task Manager. In addition, AggregatorHost is responsible for some UI elements. For example, it is responsible for the live tiles in Start, which display real-time information from applications. It also does the job of drawing a thumbnail when hovering over a running application on the taskbar.
Is AggregatorHost.exe Safe?
This process is entirely safe by itself, as it is a legitimate Windows process. However, attackers can use the name of this process to disguise their malware. To understand whether a process is legitimate or not, you need to check certain information about it.
First, a legitimate executable is always located in the C:Windows\System32 directory and is signed by Microsoft. To verify this, locate the process in Task Manager (AggregatorHost.exe), right-click on it, and select Open file location. This factor alone is enough in the majority of diagnostic cases, but you can go further and check other properties.
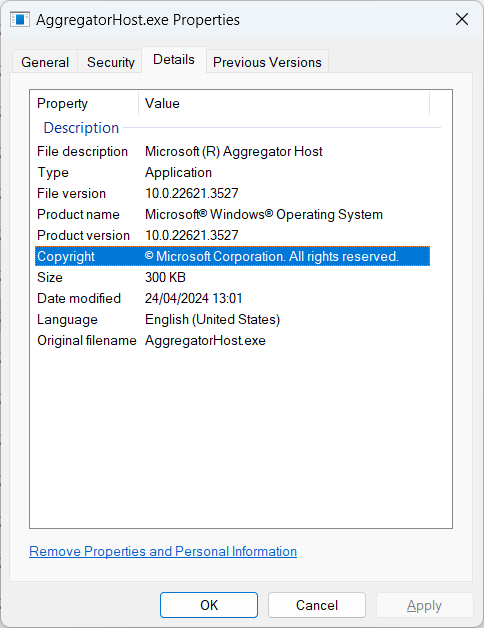
Next, you can check the digital signature of the file. To do this, right-click on the process again, click the Properties → Details tab, and make sure that the signature belongs to Microsoft Corp.
Though, in some versions of Windows, the above information may not be displayed. To check this, open PowerShell and paste the following command:
Get-AuthenticodeSignature -FilePath C:\Windows\System32\AggregatorHost.exe | Format-List
Make sure your results match these values:
Issuer: CN=Microsoft Windows Production PCA 2011, O=Microsoft Corporation, L=Redmond, S=Washington,
C=US
Status: Valid
If everything corresponds to the values above, then Microsoft issued the signing certificate and the file is all right. The Status value acts as another confirmation, as some of the malicious programs, namely backdoors, happen to use expired certificates from legit issuers to avoid detection.
Another aspect to consider is the resource utilization of the file. In its normal state, the process should consume minimal resources. If you notice a file consuming a significant amount of system power, it could indicate a problem, or malicious activity. In particular, high CPU and GPU consumption may be a sign of malicious crypto miner activity.

Can I delete Aggregatorhost.exe?
I would not recommend removing the Aggregatorhost.exe file, as it is a legitimate Windows process. However, you should investigate further if you are having any issues with this file. But first and foremost, make user your OS has all the latest patches installed – this may solve quite a few issues with the system.
Next, run a system file check. To do this, open Command Prompt as an administrator, type sfc /scannow, and press Enter. The System File Checker tool will check and restore system files if necessary.
How To Scan the System?
I recommend using GridinSoft Anti-Malware to scan your system for malware. In some cases, malware can masquerade as legitimate processes, taking its name or even its place.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.