Sentinel One has discovered that the North Korean hacker group Lazarus is targeting macOS users selectively. Attackers are using fake Crypto[.]com jobs to hack developers and digital artists in the cryptocurrency community. It is assumed that in the long term, attackers aim to steal the digital assets and cryptocurrencies of their victims.
By the way, we said that the North Korean Group Lazarus Attacks Energy Companies.
Let me also remind you that Crypto.com is one of the world’s leading cryptocurrency exchange platforms. The company gained mainstream attention in 2021 when it acquired the Los Angeles Staples Center and renamed it the Crypto.com Arena, followed by a series of television commercials.
Sentinel One analysts write that the campaign, which targets people working in the cryptocurrency industry, has been carried out by hackers since 2020. Recently, it was noticed that the attackers exploit the brand of another well-known cryptocurrency exchange, Coinbase, in their attacks, and now they have switched to Crypto.com and are attacking macOS users.
Typically, Lazarus will reach out to their targets via LinkedIn, sending them direct messages informing them of an interesting and high-paying job that Crypto.com is allegedly offering them.
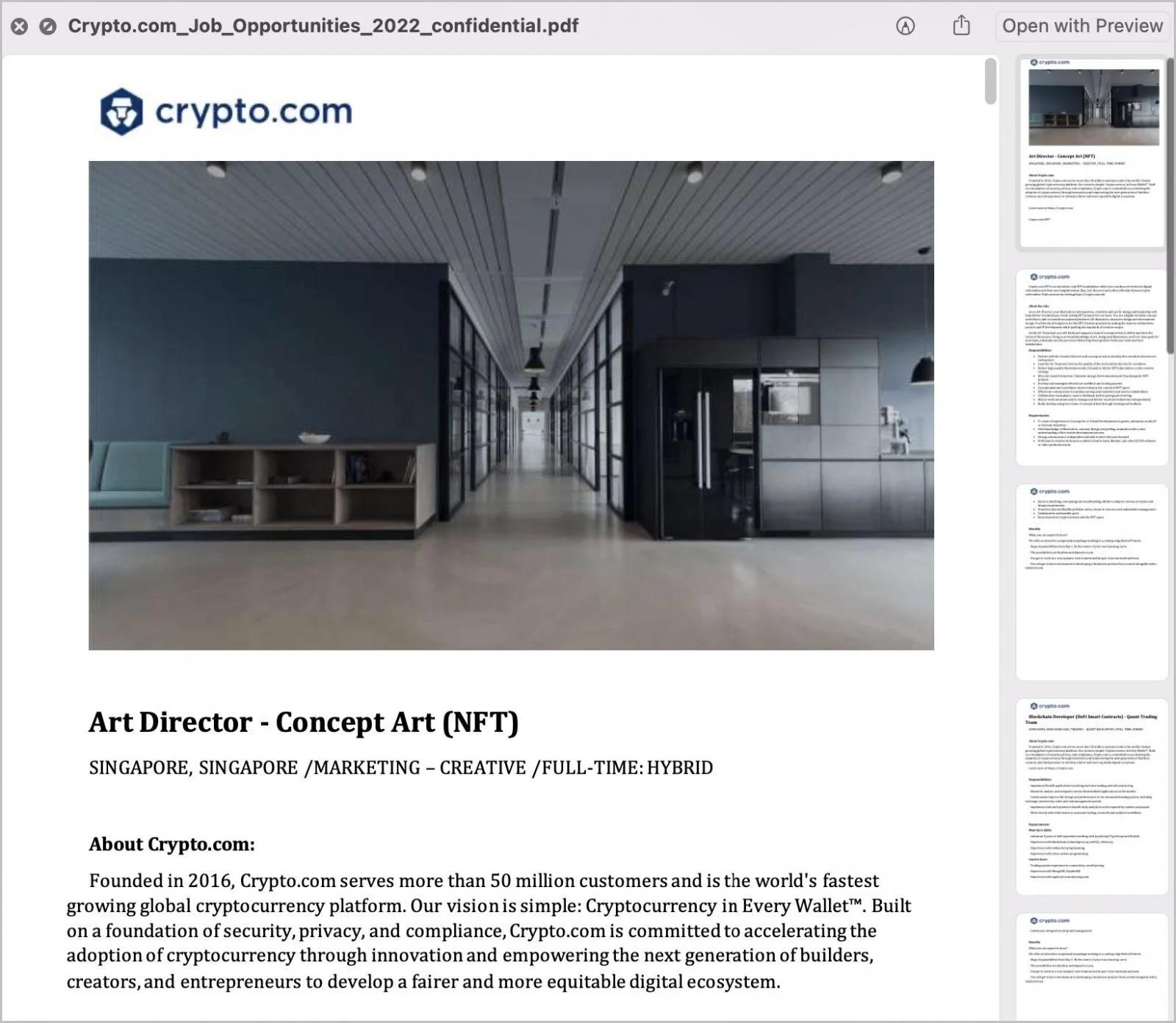
As with previous campaigns targeting macOS, the hackers send victims a binary file disguised as a PDF that contains a 26-page PDF file named Crypto.com_Job_Opportunities_2022_confidential.pdf and information about jobs on Crypto.com.
In the background, this Mach-O binary creates a folder (WifiPreference) in the Library directory and deploys the second and third stage files. The second stage is the WifiAnalyticsServ.app file, which is fixed in the system (wifanalyticsagent) and eventually connects to the control server at market.contradecapital[.]com, from where it receives the final WiFiCloudWidget payload.
Because the attackers’ binaries are signed, they can bypass Apple’s gatekeeper checks and run as trusted software.
Unfortunately, the researchers were unable to study the group’s final payload, as the hackers’ C&C server was already down at the time of the investigation. However, they note that there are some indications that this operation is short-lived, which is quite typical of Lazarus phishing campaigns.