Check Point analysts found that Chinese hackers in a chain of accidents infected an unnamed European hospital with malware. Researchers attribute this to the uncontrolled spread of malware that is dissiminated by the Chinese hack group Camaro Dragon (aka Mustang Panda, BASIN, Bronze President, Earth Preta, HoneyMyte, RedDelta and Red Lich) via USB drives.
The topic of Chinese hackers becomes more and more often guest of newsletter headlines. Some episodes surprise with their cheekiness and insolence – when they managed to use Google infrastructure as C2 servers. But healthcare infrastructure attacks are non-grata even for such daredevils. Cyberattack on a German hostpital lead to patient’s death – most likely, that was out of hackers intentions. For that reason, hackers all over the world agreed to avoid attacking hospitals.
Chinese Camaro Dragon Hackers Attacked Hospital
The Check Point report states that the Camaro Dragon typically attacks targets in Asian countries, and features designed to evade SmadAV, a popular antivirus solution in the region, can be found in the group’s malware code. However, the WispRider and HopperTick malware has infiltrated a European hospital and has also been encountered by researchers in Myanmar, South Korea, the UK, India and Russia.
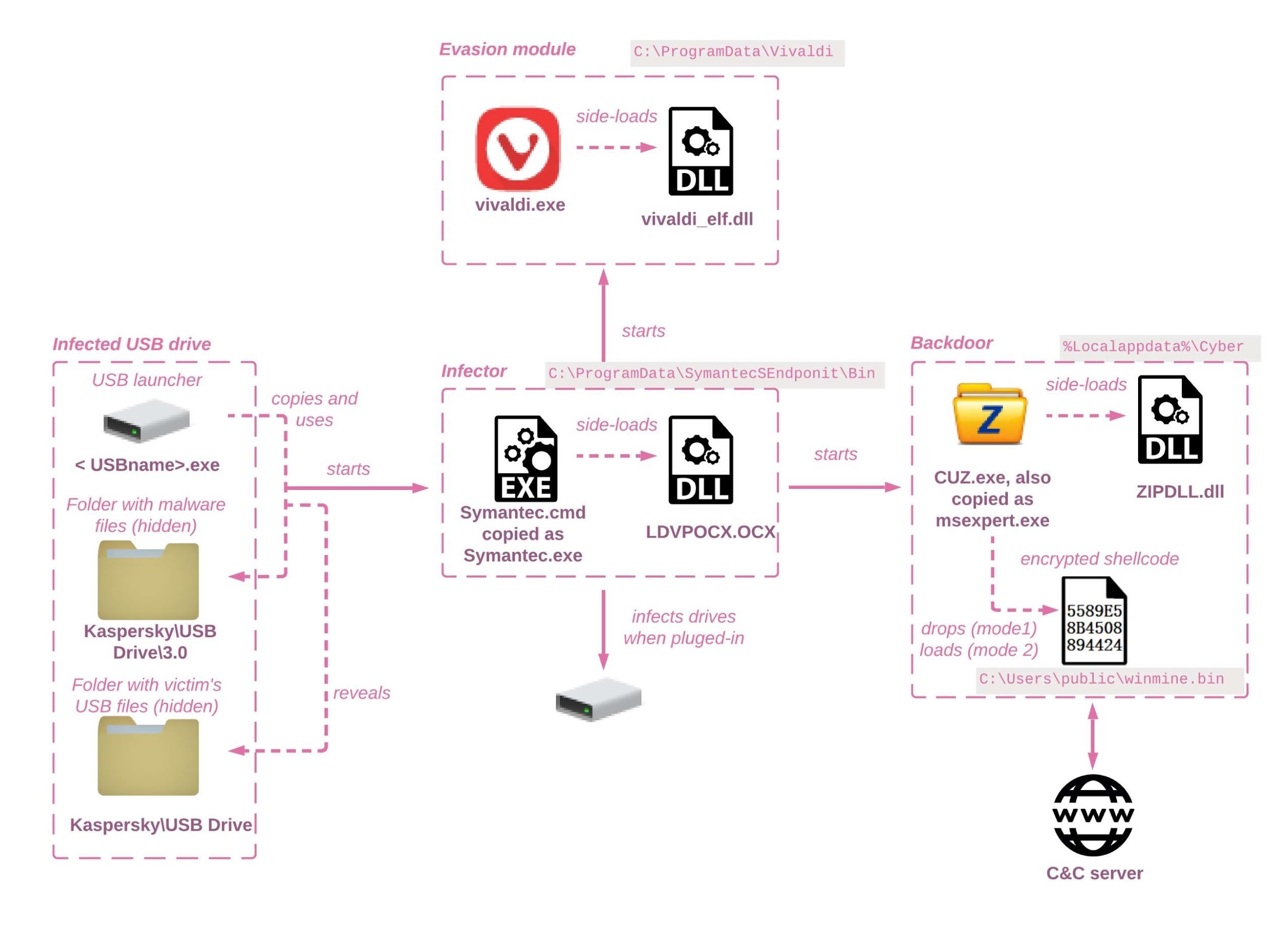
Checkpoint believes that the attack begins with the victim launching a malicious launcher written in Delphi on an infected USB drive. This causes the launch of the main payload, which downloads malware onto other drives when they connect to the infected machine. At the same time, it is emphasized that the malware poses a great danger to corporate systems, since infected machines install malware on any newly connected network drives, and not on drives already connected to the machine at the time of infection.
Researchers are confident that the spread to newly connected network drives is unintentional.
If the malicious code does run, it tries to spread the backdoor and steal data. Due to this, accidental infection of network storages becomes a serious problem, as in many organizations this is where important data is stored.
Another unpleasant feature of this malware is that it “performs DLL-side-loading using security software components, including G-DATA Total Security, and products from two major gaming companies (Electronic Arts and Riot Games).” Checkpoint says it has already warned developers about their unwitting involvement in Camaro Dragon malware companies.