An information security expert known as mr.d0x has developed a new attack technique that abuses Microsoft Edge WebView2 applications to steal authentication cookies. In theory, this allows bypassing multi-factor authentication when logging into stolen accounts.
Read also: 10 Ways To Recognize and Avoid Phishing Scams.
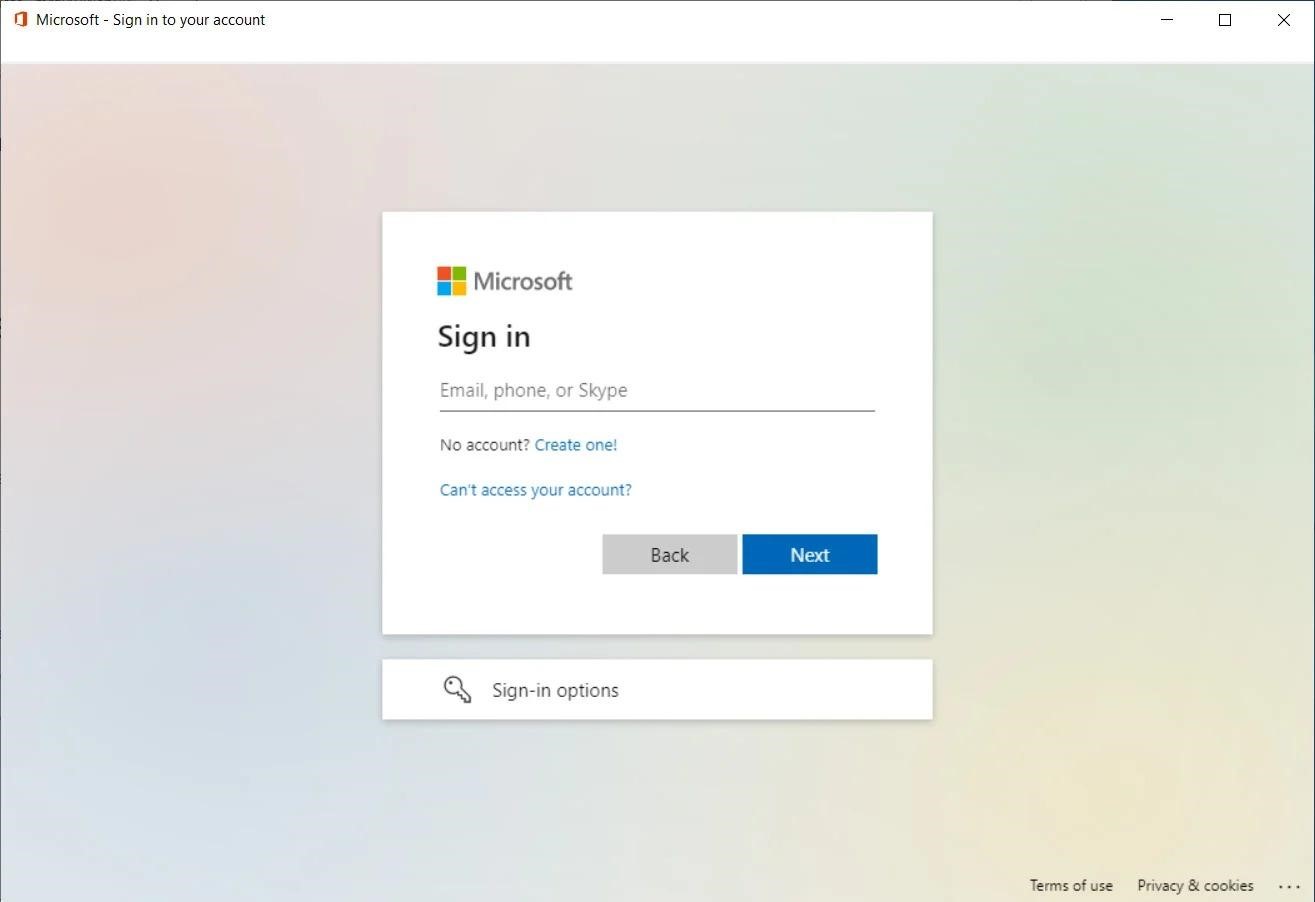
The new attack technique is called WebView2-Cookie-Stealer and consists of a WebView2 executable file that, when launched, opens a login form in the application to a legitimate site.
You might also be interested to know about TOP 12 Most Dangerous Types of Phishing Attacks 2022.
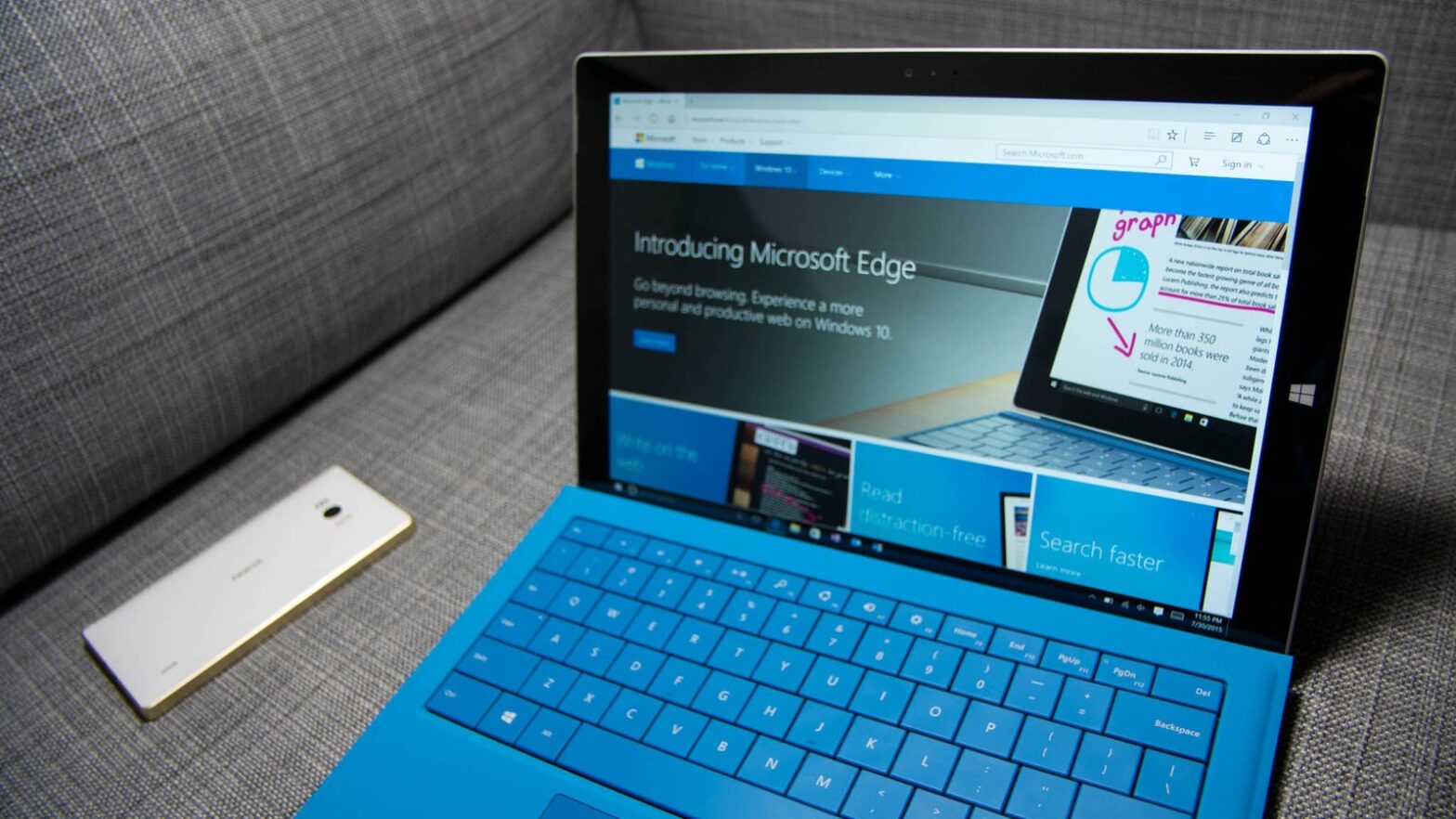
The fact is that Microsoft Edge WebView2 allows to embed a browser (with full support for HTML, CSS and JavaScript) into native applications using Microsoft Edge (Chromium) for rendering. Using this technology, apps can load any site within the app itself and display it as if it’s open in Microsoft Edge.
However, the researcher noticed that WebView2 allows the developer to access cookies directly and inject JavaScript into pages loaded by the application, making it a great tool for intercepting keystrokes and stealing authentication cookies.
For example, in the mr.d0x PoC exploit, the executable file opens a legitimate Microsoft login form using an embedded WebView2 element. This login form looks exactly the same as when using a browser and does not contain anything suspicious (typos, strange domain names, and so on).
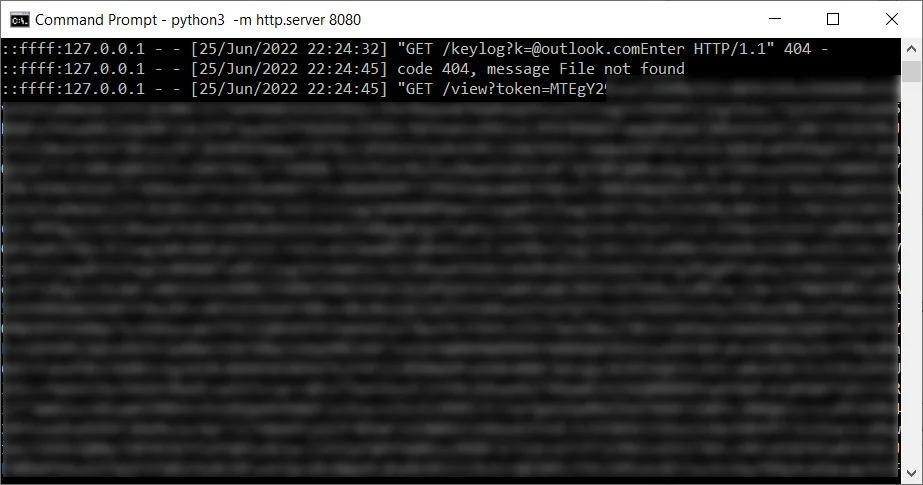
But because the WebView2 application can inject JavaScript into the page, whatever the user enters is automatically sent to the attacker’s server. In this case, any cookies sent by the remote server after the user has logged in, including authentication cookies, can be stolen.
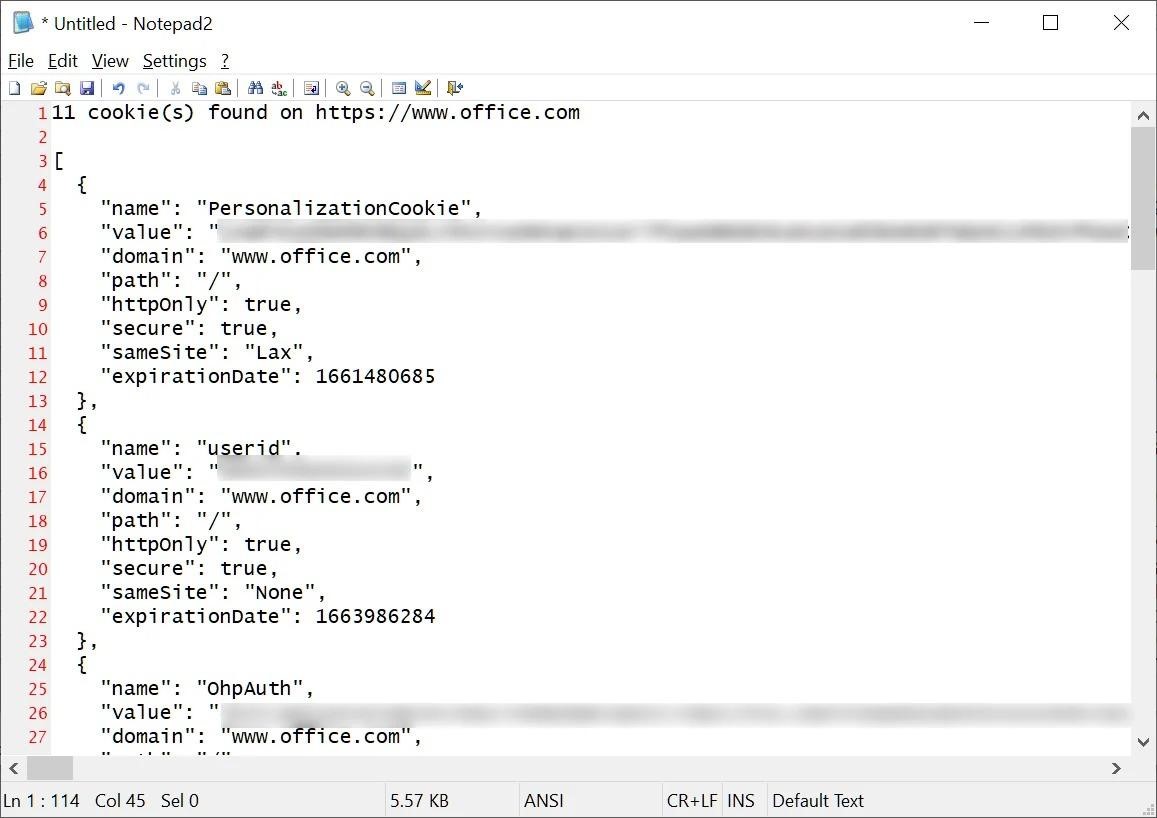
To do this, the researcher explains, the app creates a Chromium User Data folder the first time it is launched, and then uses it for each subsequent installation. The malicious application then uses the built-in WebView2 interface ICoreWebView2CookieManager to export the cookies received from successful authentication and then pass them to a server controlled by the attacker.
Once the attacker decrypts the cookie (base64), he will have full access to the sites’ authentication cookies, as well as the ability to use them to log into someone else’s account.
Mr.d0x also writes that WebView2 applications can also be used to steal cookies from an existing Chrome user profile by copying them.
Ultimately, an attacker could use these cookies simply by going to the login form for the hijacked account and then importing the cookie using any suitable Chrome extension, such as EditThisCookie. After importing the cookie, all that remains is to refresh the page for authentication on the site.
Even worse, such an attack also bypasses multi-factor authentication, since cookies are stolen after the user has logged in and successfully completed the MFA.
In response, Microsoft developers note that such an attack will require the preparation and use of social engineering, because first attackers need to convince the user to download and run a malicious executable file. The company noted that it always recommends that users avoid running and installing applications from unknown or untrusted sources, as well as keeping security software up to date.