Security professionals at Unit221b found vulnerabilities in the Zeppelin ransomware encryption mechanism. Experts managed to use them to create a working decryptor that they have been using since 2020 to help victim companies recover files without paying the attackers a penny. The work was carried out covertly so hackers would not find out about vulnerabilities in their ransomware.
Unit221b succeeded at hacking Zeppelin after seeing ransomware operators targeting charities, nonprofits and even hospices. Malware analysis from Blackberry Cylance helped the company discover vulnerabilities in the ransomware.
What is Zeppelin ransomware?
Zeppelin is a ransomware gang that started its activity around the spring of 2019, under the name of Vega/VegaLocker. Their malware also featured the name Jamper, Storm and Buran, but some analysts consider it a spin-off rather than a renamed copy. Contrary to a great number of other ransomware groups, they first aimed for ex-USSR countries. Since the beginning of 2022, they drastically changed their looks and opted to avoid Russian-speaking countries. Like most other groups, Zeppelin uses the ransomware-as-a-service model, thus its developers do not take part in distribution. Instead, they offer their “product” to hackers at different Darknet marketplaces, receiving an initial payment and per-ransom contribution. The key way of distribution threat actors chose and still use is malvertising and watering hole attacks.

Aiming generally for organizations, Zeppelin never followed the so-called “blacklist” of possible targets. That list is an agreed selection of sectors that should not be attacked – governmental and non-profit organizations, hospitals, humanitarian orgs and educational infrastructure. The group freely attacked any kind of company, asking for a separate ransom for data decryption and non-publishing of the leaked information. This practice, called “double extortion”, can sometimes increase the ransom amount multiple times.
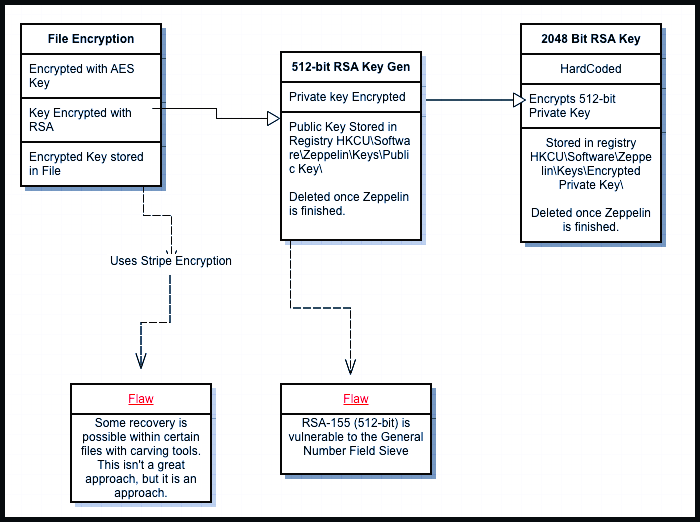
Zeppelin ransomware cipher hacked by Unit221b
The researchers noticed that Zeppelin uses an ephemeral 512-bit RSA key to encrypt the AES key, which actually ciphers the files. The AES key was stored in the footer of each encrypted file. Hence, if someone could crack the RSA-512 key, they would be able to decrypt the files without paying the attackers.
Specialists also found that the public key remained in the attacked system’s registry for about 5 minutes after the encryption was completed. The key could be extracted in three ways. Those are cutting the registry data from the raw file system, registry.exe memory dump, and directly from the NTUSER.Dat file in the “/User/[username]/” directory. The resulting data was obfuscated using RC4. Once the experts figured out this encryption layer, they had to overcome the last obstacle – the encryption layer using RSA-2048.

To overcome this hurdle, Unit221b used a total of 800 CPUs across 20 servers, each handling small portions of the key. Six hours later, the key was cracked, and analysts succeeded to extract the key from the file footer. Unit221b founder Lance James said in his interview that the company decided to make the details public because Zeppelin ransomware victims have dropped significantly in recent months. Lance said the decryption tool should work even with the latest versions of Zeppelin. It will also be available to all victims who leave a request.
What then?
Zeppelin definitely lost its image, but that won’t likely create many problems for them. Last month, their activity plummet to zero. The latest submissions related to the attack of this group appeared at the end of October. They’ve likely got an ancestor – Vice Society ransomware, that successfully attacks companies almost daily. Overall, that’s not the first time the ransomware cipher was hacked. Multiple vulnerabilities within HiddenTear ransomware allowed the analysts to break the cipher easily. Some of the encryption cases were solved via hacking into the ransomware gang’s infrastructure or capturing the threat actors. But those cases still have a share of statistical errors. Ransomware was and remains one of the most dangerous malware types, which attack may cost not only thousands of dollars but also a reputation.