JsTimer is a malicious browser extension detected in various browsers, predominantly targeting users through dubious websites. This extension engages in peculiar behavior by blocking access to the Chrome Web Store, which, although seemingly trivial at first, raises significant concerns when paired with other similarly distributed extensions.
Malicious browser extensions are not a novel threat; however, the year 2024 marks a notable resurgence in their use as effective tools in cybercrime arsenals. JsTimer, like the Funny Tool Redirect extension, is notorious for redirecting users during web browsing sessions and potentially harvesting extensive personal information, thereby posing a severe threat to user privacy.
Exploring the JsTimer Extension Virus
JsTimer is designed for Chrome and Chromium-based browsers and is categorized as a harmful plugin. On the surface, its actions might appear benign as it merely redirects users to Google Search’s main page anytime they attempt to access the Chrome Web Store. The mechanism behind this is straightforward yet invasive: JsTimer monitors and intercepts attempts to navigate to chromewebstore.google.com. This behavior mirrors the functionalities of traditional browser hijackers, making it a subtle yet significant threat.
Like many other malicious extensions, JsTimer exploits the “Managed by your organization” feature found in Chromium browsers. Typically, this setting is used by organizations to control browser setup and prevent users from modifying extensions and settings. However, in this scenario, cybercriminals manipulate this feature to thwart manual removal efforts by users.
Varied Effects of the JsTimer Malicious Plugin
The behavior of the JsTimer browser extension varies based on the IP address of the host computer. Under normal conditions, if the system’s IP address is from an area on the “operational” list, JsTimer engages in its primary malicious activities. Conversely, if the system is located in a “banned” region, the extension switches to a less aggressive mode.
Primarily, JsTimer’s main function is to redirect user searches from Google to alternative search engines. In its latest version, it redirects queries to findflarex.com, which then sends users to boyu.com.tr. Findflarex.com acts as an intermediary that not only captures the initial search request but also injects additional search tokens. Boyu.com.tr, a pseudo-search engine, uses these tokens to display an overwhelming number of advertisements. This redirection and ad-loading process are integral to the monetization strategy behind this malicious scheme.

Another facet of this scheme involves blocking access to the Chrome Web Store. Understandably, users frustrated by an extension that commandeers their search queries would naturally head to the Web Store to identify the offending extension, leave a critical review, and report the abuse. However, what this plugin cunningly does is redirect any attempts to visit chromewebstore.google.com back to the main Google search page. While this might seem minor initially, when combined with other malicious behaviors, it exacerbates the issues significantly.
If JsTimer detects that the system’s location is in what it deems the “wrong” region, it will restrict access to the Chrome Web Store. This tactic might go unnoticed by users who infrequently visit the store, yet it serves as a protective measure for the extension and any others that might be involved in the scheme.
Spreading Ways
Most of the time, junk extensions like JsTimer get into a browser through a fraudulent website that the user is getting redirected to. The latter often happens during interactions with questionable sites, typically ones with pirated content. On the page, the user sees an offer to install “the recommended extension” (text may vary depending on the case). Hackers’ hopes are on people clicking through the pages in a rush to get to the desired content. And that is it – after a single session on such a website, a user may end up with a handful of malicious extensions.
Another often situation that leads to the “install the extension” page is when there is an active adware in the system. Aside from injecting ads into all the pages that the user visits, it may also open additional tabs with more ads, or other questionable content. And since malware actors often stick to working with each other, it is not a big surprise to see adware opening a malicious extension installation page.
How to Remove JsTimer Extension?
It is possible to get rid of JsTimer in both manual and automated ways. I will recommend sticking to the automated due to the matters I’ve described above. Source malware, as well as other junk that could have gotten into the system in the same way will remain present even after you remove the extension. And for this purpose, I recommend you to use GridinSoft Anti-Malware.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.

Manual removal method
To get rid of the JsTimer extensions manually, you will need to get rid of the “Managed by your organization” thing. This trick stems from changes in the browser’s registry keys that are responsible for such deep configurations. Removing that registry key will do the job. Open Registry Editor by pressing Win+R and typing “regedit” into the appeared window. There, paste the registry address you see below:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Google\Chrome
You should delete this registry key: click it with the right mouse button and choose the corresponding option. That shall do the job – thereon, nothing will block you from removing the extension through the extension tab. After starting up, Chrome will recover its registry key, but without the malicious change.

You can also see the guides online that offer to change Group Policies. I will not share it here, as it is not possible to accomplish for all users of non-Pro Windows editions. And that is just another reason why removal with anti-malware software is preferable.

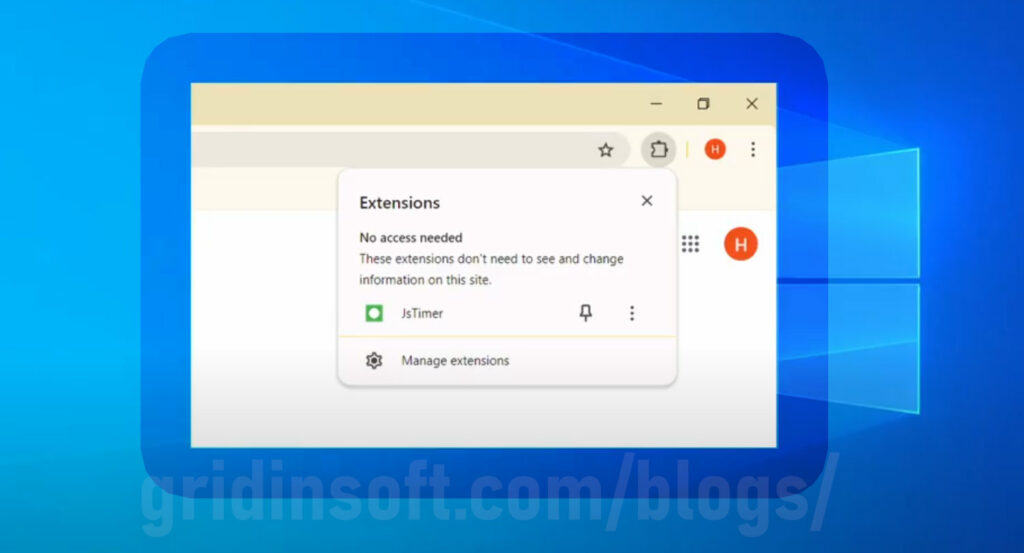

Hi! your article really helped me, though for me the chrome webstore was still visible. I could see two unwanted extentions, JSTimer and another one linked to it. I could see the extentions but I couldnt remove them because “my organization” was blocking it. I was able to remove it easily using the manual method, but I just wanted to let you know that maybe im not the only one that can see the extension through the webstore. Have a nice day!