Worst computer virus – what is it? Seems that anyone who has ever been infected asks this question. And each user will think that his case was more severe than someone’s else. Is that true? And which virus is really the worst?
It is important to mention that computer viruses are not only “viruses”. Nowadays, the term “computer viruses” is used to describe all types of malicious programs. But, in fact, viruses are just the type of malware – same as backdoors, coin miners, spyware or ransomware. You can read more about why that happened in our article.
The worst computer virus – what is it like?
First, let’s figure out what is meant by the term “the worst computer virus”. Different malware deals different kinds of damage, and it is always unwanted. Viruses can damage your networking configurations, system settings, cipher your files or even break your hardware. But the most dangerous ones considerably deal damage to all elements of your system. Some of such malware aims at making money on you, others – just to make your life harder. Let’s see the top-5 list of the worst computer virus – starting from less dangerous.
5th position. Coin miner trojan
This malware uses your hardware to mine cryptocurrencies, exactly, Monero and DarkCoin. What is the risk for your computer? First of all, it creates a significant load on your hardware – almost 70-90% on both CPU and GPU. That can easily lead to overheating, which never causes a positive impact on the lifespan of your hardware. Moreover, the GPU wear ratio is much higher when it is used for cryptomining purposes. The biggest danger is on laptops – their cooling system is not designed to deal with constantly overloaded hardware.
Another side of the problem is that modern coin miner trojans sometimes have a spyware module. It means that your personal data will not be personal anymore – read the next paragraph.
4th place. Spyware.
Spyware is designed to steal all possible personal information from the victims’ PCs. Location, language setups, cookie files, search history, activity hours data – even your PC configuration will be leaked to the crooks. Depending on the type of attack – massive or individual – this information will be sold to third parties or used for further cyber attacks. Spyware is extremely silent – it tries to stay in your system as long as possible to get more personal information about you. Most examples of this malware type are also able to steal your conversations – so don’t be surprised when you’d see some very private information available for everyone.
Spyware stealthiness makes it a tough nut for antivirus programs. Security tools often struggle to detect spyware correctly with a heuristic engine. Even if it detects one, you will probably see the detection of the “generic” type, which sometimes refers to a false detection and is thus ignored.
3. Banking trojans
What can be worse than getting your personal information stolen? Sure, getting your banking information stolen. And we are talking not only about card numbers and CVV code – they are important, but almost useless without the transaction approval. Modern banking trojans aim at your online banking – exactly, on login and password for it. Having them, crooks are free to manage your money.
Sometimes, banking trojans are combined with other malware – embedded into spyware, rogue software or phishing trojans. Since they aim at seriously protected things – online banking login forms – they are made by professionals. And it is a bad idea to ignore their efficiency – otherwise, you will have to ignore zeros on your banking account. Or, possibly, huge credit lines.
2nd place – Wiper virus
This type of malware was always very rare, but its danger can not be underestimated. Wiper malware is one that destroys your disk partitions. That malware is not about making money on you – it is just for revenge or mischief. Having your disk partition broken, you lose access to all your files and also to your operating system. UEFI is just not able to find the boot record of your OS – all data you have on your disks are just a weird mixture of non-structured bytes. Wiper malware is so rare that some of the anti-malware programs do not even have them in their detection databases.
Such a malicious program needs access to your system at the driver level. Hence, it is obvious to wait for the hazard from the program that pretends to be the driver updater, “system optimization tool”, or other deep-configuration stuff. Overall, such tools are considered dangerous because of their questionable functionality. And the chance to get your logical disks ruined complements this danger.
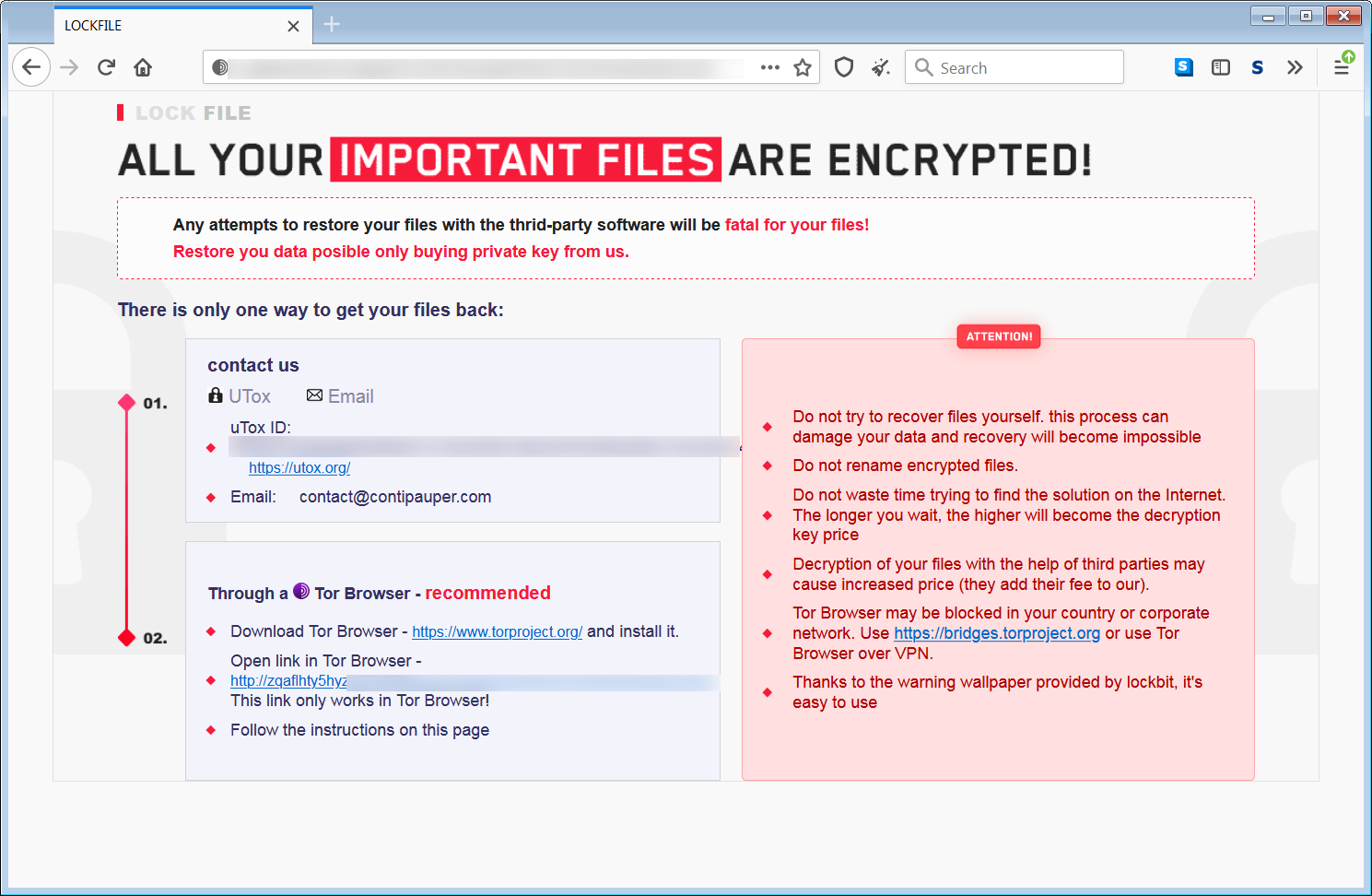
Worst computer virus ever. Ransomware
What is more painful than to get your disk partitions destroyed? Yes, to get your files ciphered. While partitions can be recovered – thanks to the special tools available for LiveCD launch – files attacked by ransomware are impossible to fix. Exactly, there are decryption tools for several ransomware families, but none of them give you a guarantee that you will get your files back. The guaranteed way to decrypt your data is to pay the ransom – $1000 and more.
Ransomware uses military-grade encryption – AES-256, RHA-1024, RHA-2048, or even ECC. Decrypting it with brute force can take more time than our universe exists. The only lucky chance of getting your files back without paying the ransom is to get encrypted with the flaw-by-design ransomware. The only well-known ransomware family that has flaws in its encryption key is HiddenTear – but its most modern variants have these breaches fixed. Another way to get the decryption key is to wait for the ransomware group to shut down. But even this does not give you any guarantees.
Ransomware also deals heavy damage to your system configurations. To prevent the usage of anti-malware software, it blocks access to the websites of the vendors that are listed on the VirusTotal site. Moreover, it also blocks the launching of antivirus software installation files. It means that your HOSTS files, along with Group Policies, suffered significant changes. If you just manage to remove ransomware, ignoring the system recovery, you will probably see your system malfunctioning.