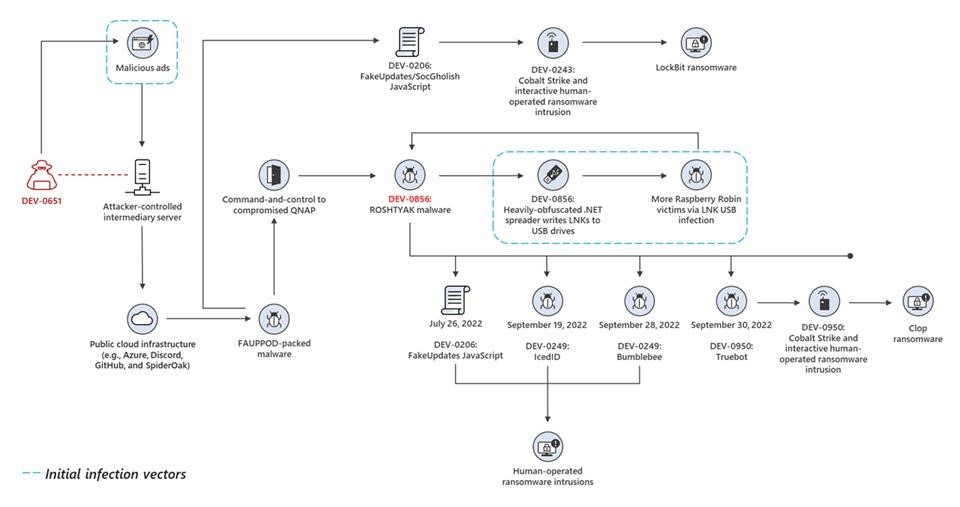
Microsoft researchers reported that the operators of the hack group, which they track under the ID DEV-0950, used the Clop ransomware to encrypt the network of a victim previously infected with the Raspberry Robin worm.
Let me remind you that the first Raspberry Robin malware was found by analysts from Red Canary. In the spring of this year, it became known that the malware has the capabilities of a worm, spreads using USB drives, and has been active since at least September 2021. The cybersecurity company Sekoia even observed that back in November last year, malware used Qnap NAS devices as control servers.
It’s also worth noting that during the summer, Microsoft researchers discovered the presence of Raspberry Robin on the networks of hundreds of organizations from various industries, some of which were in the technology and manufacturing sectors. At that time, the targets of the attackers remained unknown, since at that time they did not yet have access to the networks of the victims.
And also, as we already reported, Microsoft Links Raspberry Robin Worm to Russian Grouping Evil Corp.
Over the past months, the worm has reportedly spread to networks that now belong to nearly 1,000 organizations. In the past 30 days alone, Microsoft analysts have seen Raspberry Robin payloads on 3,000 devices in nearly 1,000 organizations.
Moreover, according to experts, Raspberry Robin operators have now become access brokers, that is, they sell access to networks of hacked companies to other criminals. For example, the malicious activity of the aforementioned DEV-0950 group intersects with the activity of the financially motivated hack groups FIN11 and TA505, which are deploying the Clop ransomware in their target networks.
Raspberry Robin and Clop Attack Scheme
Moreover, due to Raspberry Robin, other threats also penetrated victims’ devices, including payloads of malware such as IcedID, Bumblebee and TrueBot.
Analysts summarize that from a widespread worm that did not show any activity after infection, Raspberry Robin has become one of the largest malware distribution platforms.
So, earlier researchers have already noticed that with the help of Raspberry Robin, the FakeUpdates (aka SocGholish) backdoor, which experts associate with the Evil Corp hacker group, was delivered to victims’ devices. Now there are much more malware that penetrates the systems of victims because of this worm.