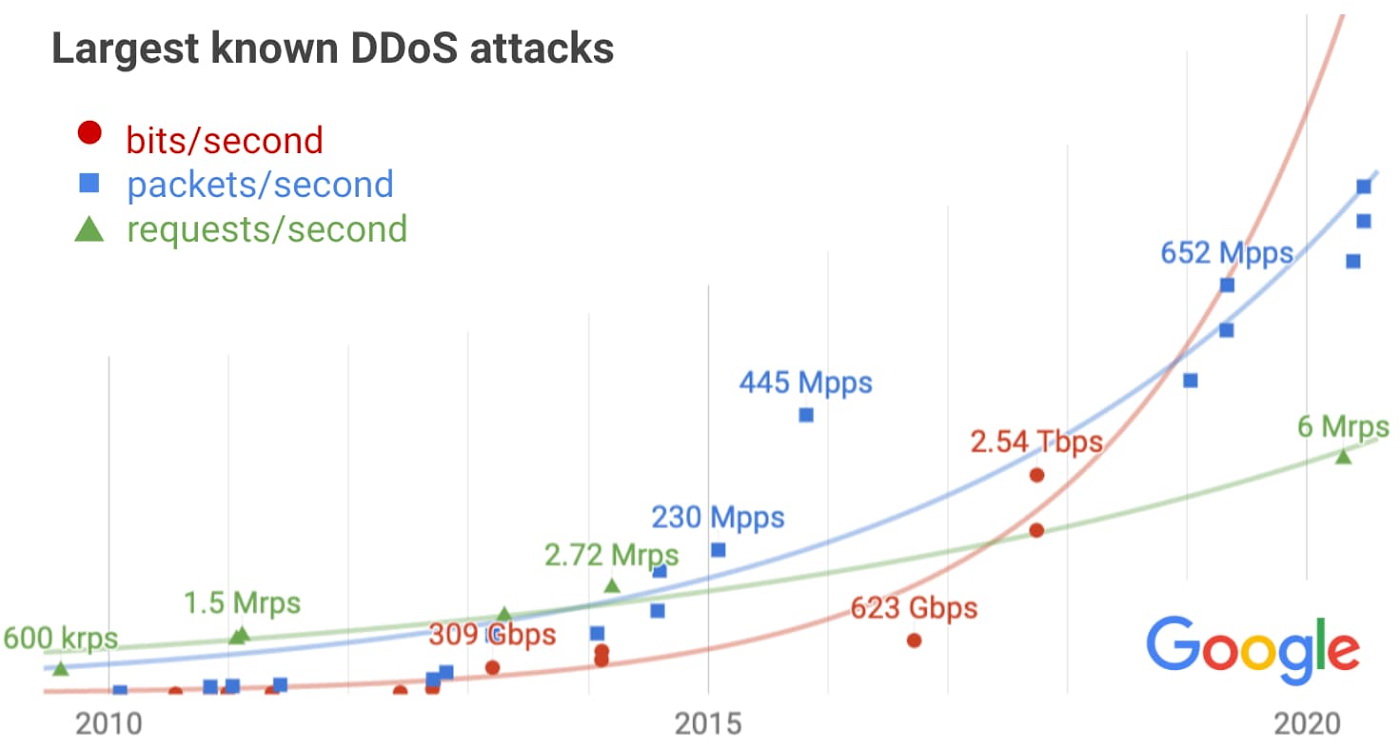
This week, the Google Cloud team talked about a previously unknown DDoS attack that targeted a Google service back in September 2017 and peaked at 2.54 TB/sec, making it the most powerful recorded attack in history.
Soon, analysts from the Google Threat Analysis Group (TAG) published their report on the incident, in which they said that “government hackers” were responsible for the attack.
According to TAG, the attack came from China, from the networks of four specific providers: ASN 4134, 4837, 58453, and 9394.
The researchers write that 2.54 TB/sec was the culmination of a six-month long campaign against Google, during which attackers used various attack methods and tried to undermine the company’s server infrastructure. It was not reported which services the hackers were targeting.
“Attackers used multiple networks to spoof 167,000,000 packets per second into 180,000 open CLDAP, DNS and SMTP servers, which then sent huge responses to us. This demonstrates the scale that well-resourced criminals can achieve: four times the record 623 GB/s attack carried out by the Mirai botnet a year earlier [in 2016]”, — wrote Google engineers.
It is also worth noting that the incident described by Google surpasses even the attack on Amazon that occurred in February of this 2020, the capacity of which was 2.3 TB/sec. That is, the record for DDoS attacks has once again been broken.
Google experts explain that for a number of reasons they kept the incident secret for several years, but now they decided to make the incident public. The fact is that the Google TAG team wanted to draw attention to the increasing incidence of DDoS attacks from government hackers, as well as to the fact that as the Internet develops, the number and power of such attacks will only continue to increase.
However, since the described attack to date remains the record for maximum throughput, this slightly reduces the confidence in the extrapolation of such statistics.
With a DDoS attack, an adversary hopes to disrupt their victim’s service with a flood of useless traffic. While this attack doesn’t expose user data and doesn’t lead to a compromise, it can result in an outage and loss of user trust if not quickly mitigated.
Let me also remind you about the multifunctional Lucifer malware uses many exploits, is engaged in mining and DDoS attacks.