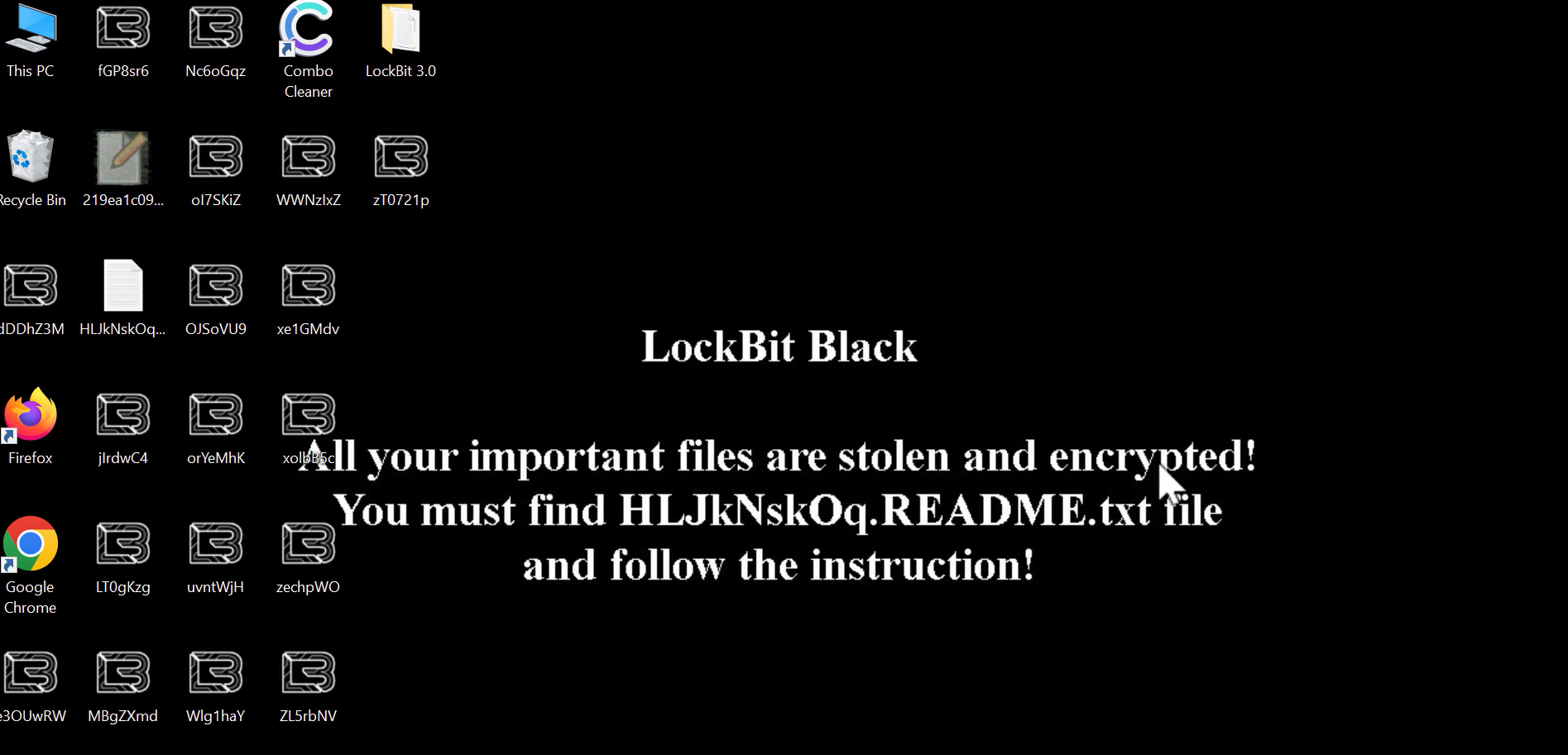
On September 21, 2022, a new Twitter user Ali Qushji published what is supposed to be a LockBit Ransomware builder. According to what the user says, this application is for LockBit 3.0 ransomware – the latest version of malware used by these cybercriminals. The exact user pretends to be an anonymous hacker who breached LockBit infrastructure.
What is LockBit Ransomware?
LockBit Ransomware is one of the most successful ransomware gangs among the ones active in 2022. Appeared in 2020, it quickly became a big fish – thanks to its extremely fast and reliable encryption, and the same fast data extraction tools. In 2022, after the Conti group shutdown, it rapidly gained market share and became an absolute leader. Available statistics show that almost 60% of ransomware attacks on corporations in the summer of 2022 were commenced by the LockBit group.
They’re also known as a very public group, as they are constantly active on various forums, and even give interviews to various blogs. The main narrative the group were pushing was “Lockbit always does what they promise”. They have likely meant that after paying the ransom(s), the victim will receive the decryption key, and its files will be deleted. Obviously, DDoS-attacks this group started using to create the other stimulus to pay should be stopped as well. Such confidence is likely the result of a diligent hiring program – the administration is definitely sure that group members follow the rules.
LockBit 3.0 Builder leak
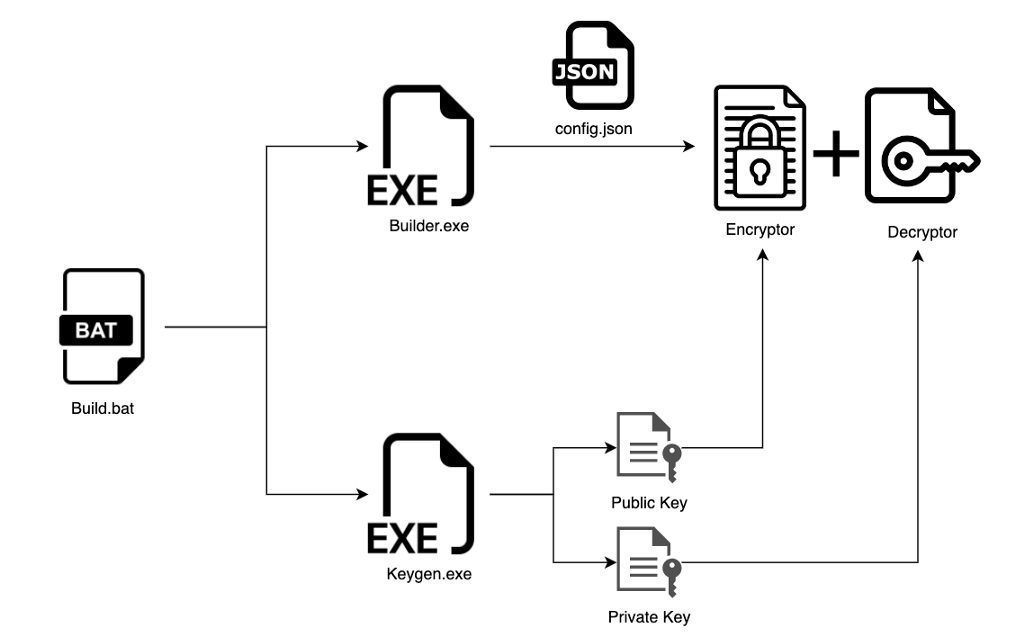
Each ransomware sample deployed by the LockBit group is unique. It is delivered to the target system after establishing the connection that follows the initial access. The special tool generates a new build of malware that makes it impossible to detect it with any kind of signature analysis. It is also used in creating the encryption and decryption keys, which makes this app potentially valuable for creating a unified decryptor.
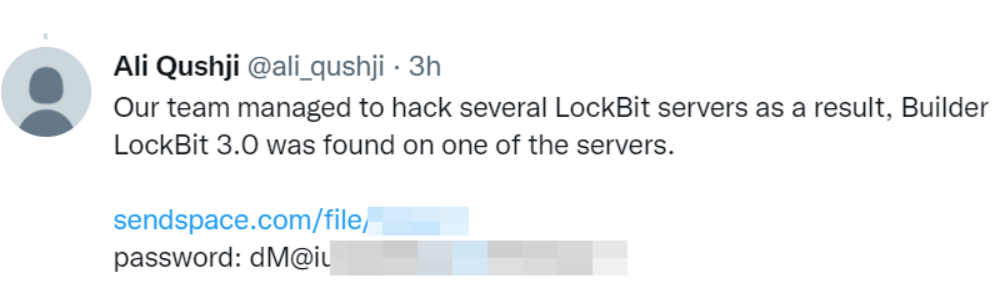
On Wednesday, 21st of September, 2022, a Twitter user nicknamed Ali Qushji posted several tweets where they shared the link to builder download and some details. In particular, there was a claim that this program has been leaked from the LockBit infrastructure after the successful hacking of the latter. There is no evidence that there was any real hacking into LockBit servers, but another tweet (now deleted) from Vx-Underground was confirming the earlier breach (as of September 10, 2022).
A person nicknamed Proton, who appears to be a programmer that works for the group, shared a builder with the admins of the aforementioned Twitter page. That version belonged to the latest version of LockBit 3.0 ransomware and featured several flaws fixes that were present earlier. What creates even more confusion is the fact that both versions – the one shared by Proton and the one from Ali Qushji – are different. Both of them are available on 3xp0rt’s GitHub.
What’s next?
The situation is as unclear as it could be. The chance that LockBit infrastructure was breached is pretty high, and if this turns out to be true – the group will likely have some serious problems. And not only because of security concerns: ones who got inside of the servers have likely leaked all the data needed to create a decryptor. Sure, the group can switch on the other technology – but it will take time, and such an operation will not be very pleasant shortly after switching to LockBit 3.0 ransomware. It is better to wait for the official reaction of a cybercrime gang – and only then make any conclusions.