In mid-May 2020, in the Telegram channel of the head of DeviceLock company Ashot Hovhannisyan appeared information on data leak of 33.7 million LiveJournal users. Now, experts have confirmed a data leak of 26 million users.
It was reported that the detected text file contains 33,726,800 lines, among which you can find user IDs, email addresses, links to user profiles, as well as passwords in plain text format (among them 795,402 lines had a blank password).
Subsequent analysis of passwords shoed that 69% of mail/password combinations were unique, that is, they had never been found in other leaks before.
Now ZDNet has published material that sheds light on the details of what happened.
“Apparently, LJ suffered from a break-in back in 2014, and rumors about this have been circulating in the network for many years. For example, they talked about compromise in October 2018, when LiveJournal users massively reported that they received old but unique passwords from LiveJournal as part of a blackmail sextortion campaign”, – write ZDNet reporters.
Although the 2014 hack was not officially confirmed, in recent months the DreamWidth blogging platform, created on the basis of the LiveJournal code base, has also been attacked. In a series of posts and tweets, DreamWidth developers talked about the massive credential stuffing attacks they have noted recently.
Stuffing attacks are situations, when usernames and passwords are stolen from one sites and then used on others. Therefore, attackers have a ready-made database of credentials (purchased on the darknet, collected independently, and so on) and try to use this data to log in to any sites and services under the logins of their victims.
Unfortunately, users often apply the same usernames and passwords for different services without changing them for years, which makes such attacks very effective.
DreamWidth claims that hackers used old combinations of user names and passwords from LiveJournal to crack DreamWidth accounts and posted spam messages on the site.
However, the Rambler company, which owns LiveJournal, still refused to acknowledge the fact of compromise, even after DreamWidth administrators contacted it.
Now, the authoritative leak aggregator Have I Been Pwned (HIBP) has confirmed the fact of leakage of user data from LJ. The administration of the service received a copy of the LiveJournal user database and indexed it on its website.
“The dump contains data of 26 372 781 LiveJournal users: user names, email addresses and passwords in plain text. This is consistent with Ashot Hovhannisyan’s information, which estimates that the dump contains approximately 22.5 million unique mail/password combinations”, – reported in HIBP.
Analysts of the information security company KELA found many references to the stolen database and its copies in different places of the hacker underground, and confirmed the existence of a dump.
So, first KELA and ZDNet discovered several ads that posted data brokers. In these ads, hackers said they wanted to sell or buy the LiveJournal database. That is, criminals were well aware of the data stolen from LJ and actively exchanged it.
Judging by these announcements, after LJ was compromised in 2014, hackers sold the stolen data privately, handing databases from hand to hanв among spammer groups and botnet operators. Since this data was exchanged again and again, information eventually leaked to the public.
The first notification that the LiveJournal database became public arrived in July 2019, which was announced by the now defunct WeLeakInfo service that was selling stolen data.
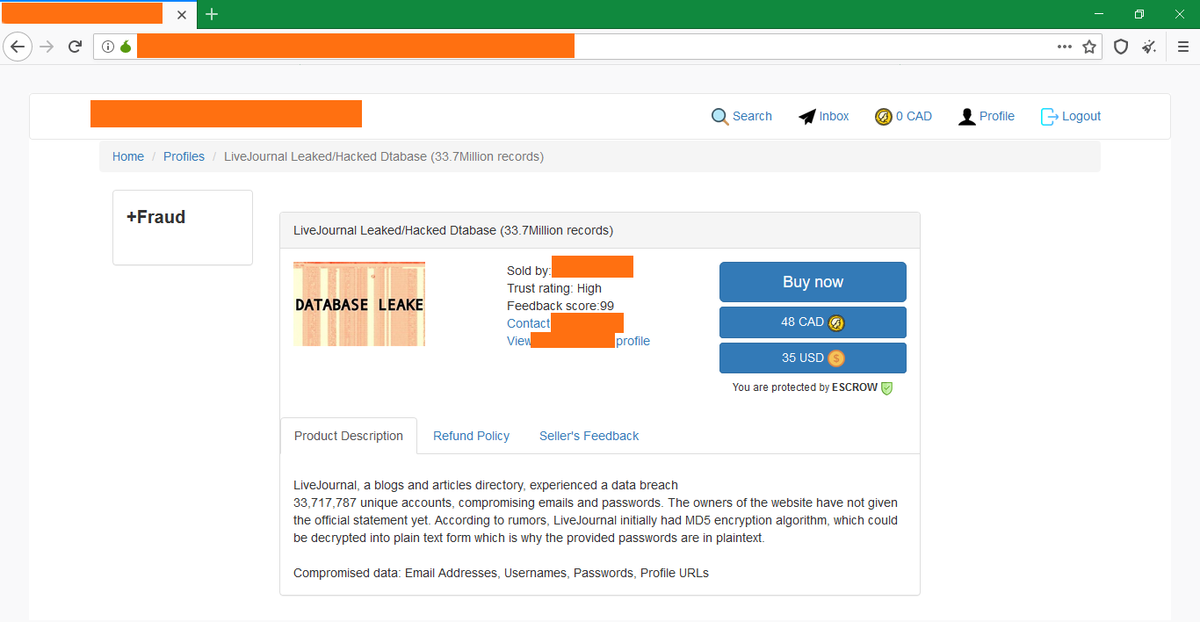
Over time, this dump became available even wider. For example, recently LiveJournal databases were sold on darknet for the price of only $35. The ad, which is shown in the illustration below, refers to 33 million records, but this is the overall dump before removing duplicates.
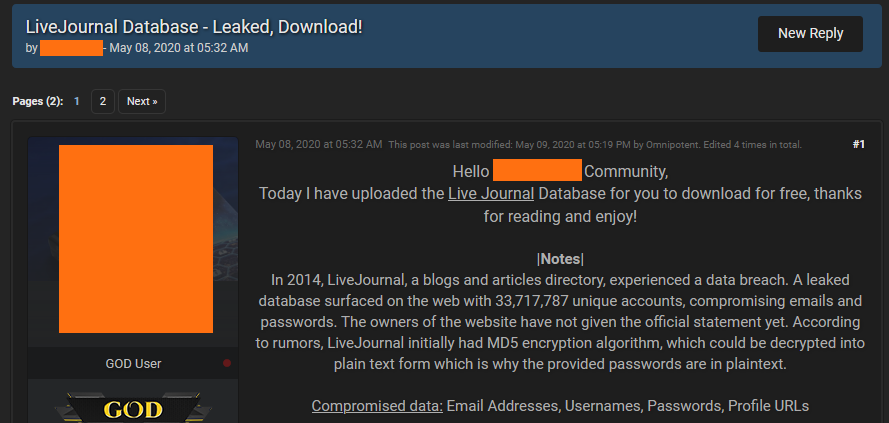
As a result, the LiveJournal database was published on the well-known hacker forum, from where it instantly spread, and now the dump is offered for free on Telegram channels and uploaded to file sharing services.
ZDNet notes that the DreamWidth platform still suffers from attacks with the use of old credentials, stolen from LiveJournal, although the company’s developers release updates and try to protect their users.
Of course, not only DreamWidth users are at risk. People that use LJ logins and passwords on other sites are also at risk of hacking due to credential stuffing attacks. Users that changed their LJ password after 2014 may be safe, however, experts still advise changing the passwords from any other accounts where the same credentials could be reused.
Interestingly, ZDNet managed to get a comment from Rambler representatives yesterday. The fact is that two weeks ago the company announced that the information about the data leak “is not true – this is one of the clickbait news, the task of which is to attract interest of a third party in this matter.”
No representatives of the Rambler Group holding continue to deny that hackers have gained access to their systems, but confirm the existence of a dump and say that the database contains information that hackers have been collecting for many years from various sources: malware-infected systems (data stolen from browsers) and brute force – attack (hackers simply selected passwords to LiveJournal accounts).