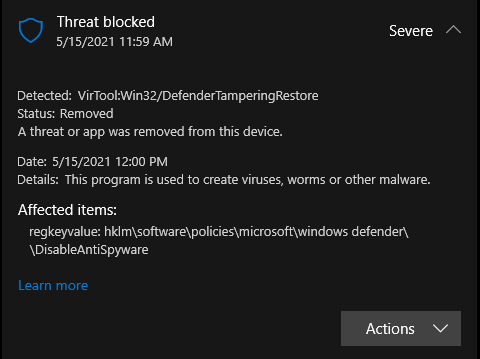
VirTool:Win32/DefenderTamperingRestore is the name of the Microsoft Defender detection of a malicious element present in the system. Usually, it marks a thing that can weaken the system’s security and make the device vulnerable to malware injection. Let’s find out how dangerous this is, and how to deal with it.
Threats like VirTool are often the sign of an ongoing malware attack. Threats may carry embedded code that targets security tools and uses a stand-alone script. The fact that malicious software tries to disable antivirus tools usually means that its activities are hard to conceal, i.e. it is something harsh and severe. Ransomware, desktop blockers, vandal viruses, coin miners – all of them can make use of a defenseless system.
What is VirTool:Win32/DefenderTamperingRestore?
VirTool:Win32/DefenderTamperingRestore detection points at a malignant element that can prevent Microsoft Defender from working properly. This can include various scripts, ones that modify registry keys that control the functioning of Defender. It is also triggered when trying to run scripts or download programs designed to subvert system defenses. As I said, VirTool is hidden from the user and runs in the background. This makes malware detection and removal more difficult.
Also, pirated software can contain part of code that modifies system settings to bypass license restrictions but does not carry malicious functionality. Pirated software may also include scripts that disable Microsoft Defender to prevent malicious components from being detected and removed.
Is VirTool:Win32/DefenderTamperingRestore false positive?
Although VirTool:Win32/DefenderTamperingRestore usually indicates the presence of malicious activity, in some cases it may be the result of a false positive detection. This can happen if legitimate software or administrative scripts change security settings during standard operation or system maintenance.

VirTool:Win32/DefenderTamperingRestore sometimes also appears in scenarios involving the use of Microsoft Safety Scanner (MSERT), which can identify and report changed settings as part of its scan, correcting them back to safer configurations.
DefenderTamperingRestore Analysis
As I said above, it specializes in modifying registry keys to disable Microsoft Defender, or restrict its capabilities. This is mainly done through PowerShell or Command Prompt commands that modify system policies and specific Defender settings.
One particular thing that quite a few VirTool:Win32/DefenderTamperingRestore samples do is modify the registry entries responsible for real-time and heuristic protection. Malware particularly goes for the “DisableRealtimeMonitoring” key to disable real-time protection or modify “DisableBehaviorMonitoring” to stop tracking suspicious activity.
Walking Through Affected Registry Keys
Among the main targets of VirTool is to disable Defender completely. Malware creates the “DisableAntiSpyware” parameter, setting its value to 1, which stops Defender from running.
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender
To disable proactive protection, VirTool creates another key – “DisableRealtimeMonitoring” – and sets it to 1. This stops the security tools from continuous scanning of all the accessed folders and launched files.
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection
A less often trick that thing pulls targets the automatic sample submission system. By setting the 1 value to the DontReportInfectionInformation entry in the following registry hive, it disables sending samples to Microsoft.
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Spynet
Some of the things that Microsoft detects with this name reach a sky-high level of tricks with Windows commands. A confusing set of meaningless letters and symbols you can see below is rather useful. It sets certain folders – particularly ones that malware uses – to the whitelist of Microsoft Defender. Several ransomware samples use the same or similar commands during gaining persistence.
C:\Windows\SysWOW64\sc.exe
sc sdset WinDefender D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPLOCRSDRCWDWO;;;BA)(D;;WPDT;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)
In rare cases, VirTool acted as a loader, downloading and executing additional malicious modules. It modified the “Shell” and “Userinit” registry keys to execute malicious scripts at system startup. However, a much more common occasion is this malicious element being embedded into a more complex script. The latter typically orchestrates the initial malware injection, where disabling Microsoft Defender is a rather obvious preliminary step.
How to Remove VirTool:Win32/DefenderTamperingRestore?
The appearance of VirTool:Win32/DefenderTamperingRestore is usually a bad omen. It is likely a sign of malware activity that goes below the radar. For that case, I recommend following these steps:
1. Restart your computer into Safe Mode with Networking
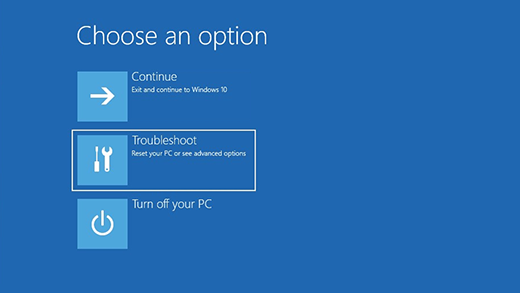
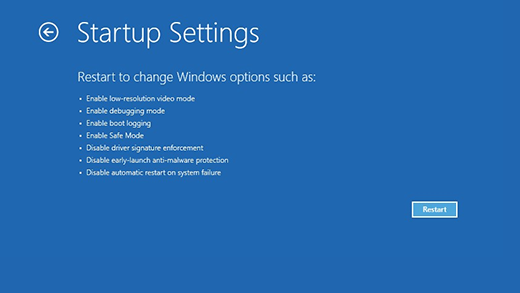
Open the Start menu, then click the “Reboot” button while holding the Shift key. The Troubleshooting menu will appear, select here “Troubleshoot” → “Startup Settings” and click “Restart”. This sends you to the window with Safe Mode options.
There, click on the 5 button to launch the Safe Mode with Networking. This mode stops all non-essential processes from launching, leaving you with bare Windows and network connectivity features enabled. Doing so restricts malware from running, making the removal much easier to accomplish.
2. Run reliable antivirus software
Download a reliable antivirus software that can remove VirTool remnants permanently from your PC. GridinSoft Anti-Malware is an excellent option for this. Run a Full Scan and remove any detected threats.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.