Law enforcement agencies, as well as European and American authorities, have taken up the fight against ransomware in earnest and the other day they arrested a Kaseya hacker.
However, over the past few days, several important events have taken place at once.
Operation Cyclone, which was carried out by Interpol, the law enforcement agencies of Ukraine and the United States, lasted more than 30 months and was aimed at fighting Clop ransomware (aka Cl0p). As part of this operation, six Ukrainian citizens were arrested in June 2021.
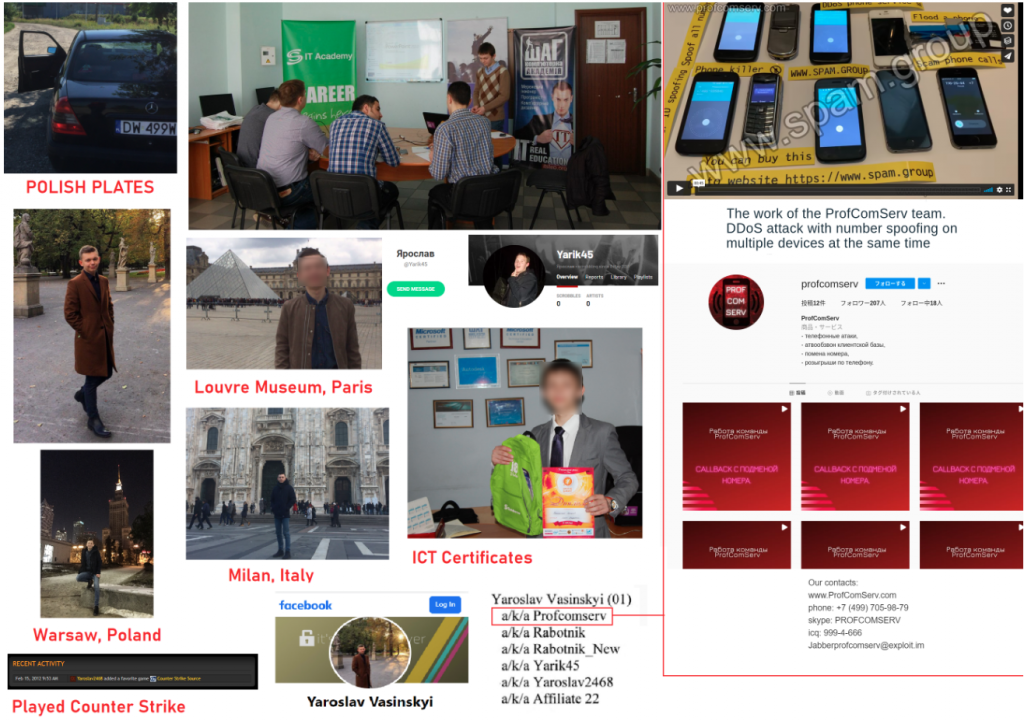
The US Department of Justice has also indicted Yaroslav Vasinsky, a 22-year-old citizen of Ukraine, who is suspected of organizing a ransomware attack on Kaseya’s servers in July this year.
The suspect was detained last month under a US warrant. He was arrested by the Polish authorities at the border between Ukraine and Poland.
Let me remind you that in early July, customers of the MSP solution provider Kaseya suffered from a large-scale attack by the ransomware REvil (Sodinokibi). Then the hackers used 0-day vulnerabilities in the company’s product (VSA) and through them attacked Kaseya’s customers. Currently, patches have already been released for these vulnerabilities.
The main problem was that most of the affected VSA servers were used by MSP providers, that is, companies that manage the infrastructure of other customers. This means that the cybercriminals have deployed the ransomware in thousands of corporate networks. According to official figures, the compromise affected about 60 Kaseya clients, through whose infrastructure hackers were able to encrypt approximately 800-1500 corporate networks.
As the authorities now say, Vasinsky was known on the network under the nickname MrRabotnik (as well as Profcomserv, Rabotnik, Rabotnik_New, Yarik45, Yaraslav2468, and Affiliate 22) and since 2019 has hacked companies around the world (having made at least 2,500 attacks), implementing to their infrastructure REvil malware.
To recover their files, the victims had to pay a ransom to the REvil hack group, and Vasinsky received a significant portion of this “profit”. The Justice Department said the hacker “earned” $2.3 million, demanding more than $760 million from companies in total.
In addition to Vasinsky, the US Department of Justice also indicted the second suspect, who also collaborated with the REvil hack group. In court documents, this person appears as a 28-year-old citizen of Russia Yevgeny Polyanin (aka LK4D4, Damnating, damn2Life, Noolleds, Antunpitre, Affiliate 23). He also reportedly worked with REvil as a partner, hacking companies on behalf of the group.
According to authorities, Polyanin hacked into the network of TSM Consulting, a managed service provider based in Texas, from where he deployed REvil malware on the intranets of at least 20 local government agencies on August 16, 2019.
Although Polyanin is still at large and wanted by the FBI, the Justice Department says that specialists managed to seize $6.1 million worth of cryptocurrency that the suspect had kept in an FTX account.
This week, Europol announced the arrest of seven suspects who worked as partners of the REvil (Sodinokibi) and GandCrab ransomware, and have helped carry out more than 7,000 ransomware attacks since the beginning of 2019. Experts from Bitdefender, KPN and McAfee also took part in the operation.
Let me remind you that, according to information security specialists, REvil and GandCrab are run by the same people who created the malware and offered it to other criminals for rent.
As we previously reported, the US government has also offered a $10,000,000 reward for any information that could lead to the identification or arrest of members of the DarkSide hack group.