ARP Spoofing (also known as ARP Cache Poisoning) is a type of cyber attack based on sending malicious ARP (Address Resolution Protocol) packets by attackers to the default gateway via the local network (LAN), using it in such a way as to associate its own MAC address with the IP address of the gateway device.… Continue reading ARP Spoofing (ARP Cache Poisoning) Attack
Tag: Spoofing
Phishing vs Spoofing: Definition & Differences
What is a Phishing Attack? Phishing is a cyber-attack method that introduces malware to a computer via email. Intruders send users emails containing links under various pretexts. After clicking these links, the malware enters your computer. Thus, cybercriminals deceive the target to get as much data about the user as possible: his card numbers, bank… Continue reading Phishing vs Spoofing: Definition & Differences
Sniffing and Spoofing: Difference, Meaning
Users are increasingly encountering malicious links that, when clicked, unleash a different kind of computer destruction. In this case, users must be aware of the appearance of such malware, its associated links, and other potential hazards. This article aims to introduce the concepts of sniffing and spoofing, distinguish between them, explore protective measures against these… Continue reading Sniffing and Spoofing: Difference, Meaning
Black Hat SEO: Is Someone Phishing With Your Site Domain?
Search engine optimization (SEO) is a process of optimization and upgrading of websites to improve the ranking of search engine results pages and to attract traffic. Among other things, SEO helps to create a reliable reputation. But there is also a black SEO, also known as black hat SEO. The article below will tell you… Continue reading Black Hat SEO: Is Someone Phishing With Your Site Domain?
Twilio Falls Victim To Phishing Attack
Twilio, a tech giant from San Francisco, became a victim of a phishing scam, resulting in the exposure of consumers’ data. The exact incident took place on August 4 and is likely conducted through the use of SMS phishing. Twilio Data Breach Twilio, the provider of voice and SMS notification services for various purposes, turned… Continue reading Twilio Falls Victim To Phishing Attack
11 Types of Spoofing Attacks
Spoofing is a kind of cybercrime in which attackers impersonate a trusted source, such as a trusted contact, to gain access to confidential information or steal data, whether personal or professional. In addition to threatening your data privacy, Spoofing attacks can damage the brand’s reputation or the person the attackers are impersonating, sometimes making it… Continue reading 11 Types of Spoofing Attacks
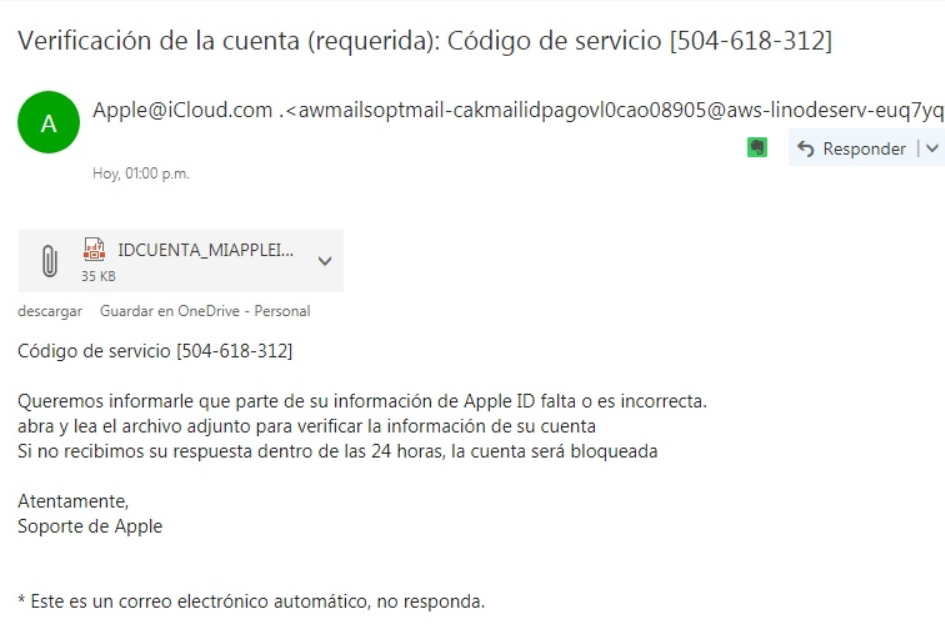
Extension spoofing strikes Spanish-speaking countries
An old-good form of malware disguisment sparked recently in several Spanish-speaking countries across the globe. Users note numerous cases of email attachments with spoofed file extensions, that appear to be coin miner trojans. Massive outbreak of extension spoofing in email spam Email spam is a form of malware spreading that became very popular at the… Continue reading Extension spoofing strikes Spanish-speaking countries
DNS Spoofing: Key Facts, Meaning
What is DNS Spoofing? DNS (Domain name server) spoofing or DNS cache poisoning is a type of cyberattack used by an attacker to direct the victim’s traffic to a malicious website (instead of a legal IP address). Attackers use DNS cache poisoning to redirect Internet traffic and steal sensitive information. For example, a hacker wants… Continue reading DNS Spoofing: Key Facts, Meaning
IP Spoofing Attack: Explanation & Protection
Among other types of attack, IP spoofing stands out for its simple yet graceful design. This is, exactly, what goes for its long life and widespread application throughout decades. Let’s see how this attack works, and where the hackers can use it. What is IP Spoofing? IP spoofing is a type of cyberattack where the… Continue reading IP Spoofing Attack: Explanation & Protection