Stopabit is an unwanted application that has almost no useful functionality. Users can see its promotions as a useful tool for screen time control, but it in fact aims at exploiting the bandwith. This may lead to connectivity issues and illicit traffic being routed through the system.
Such applications are commonly distributed through software bundling. This supposes installation along with pirated software, game mods and similar software from questionable sources.
Stopabit Virus Overview
Stopabit is a malicious software that manifests as a process within the Windows Task Manager. It falls into the Potentially Unwanted Applications (PUAs) category, working as proxyware. This means that Stopabit can route third-party traffic through the system it is active in. Aside from this, it pretends to be a convenient tool to schedule short breaks in your PC usage, presumably to take care of your eyes.
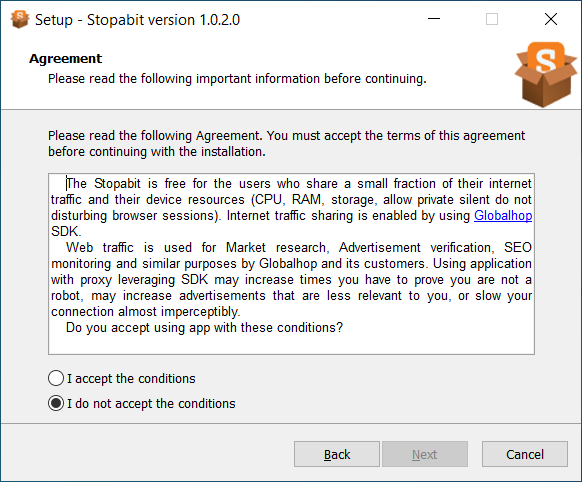
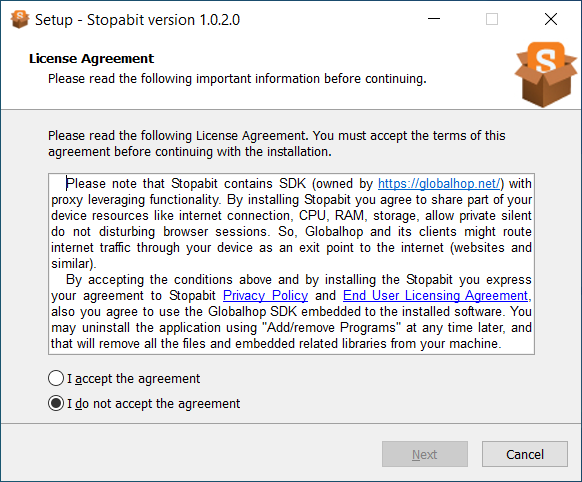
Key danger of proxyware is the unauthorized usage of the system’s bandwidth. During the installation, Stopabit says it will monetize using Globalhop SDK. The latter looks legit only on surface: as numerous analyses from well-known security vendors show, this SDK was repeatedly used to route illegal traffic. As gray proxy services are rather popular in the Darknet, it is pretty easy to understand where this traffic comes from.
Similarly to other proxyware apps, Stopabit mainly gets into user devices through pirated software and similar illegal programs like keygens and activators. Sometimes, it can infiltrate systems through fake versions of mods for popular games.
Stopabit Runtime Analysis
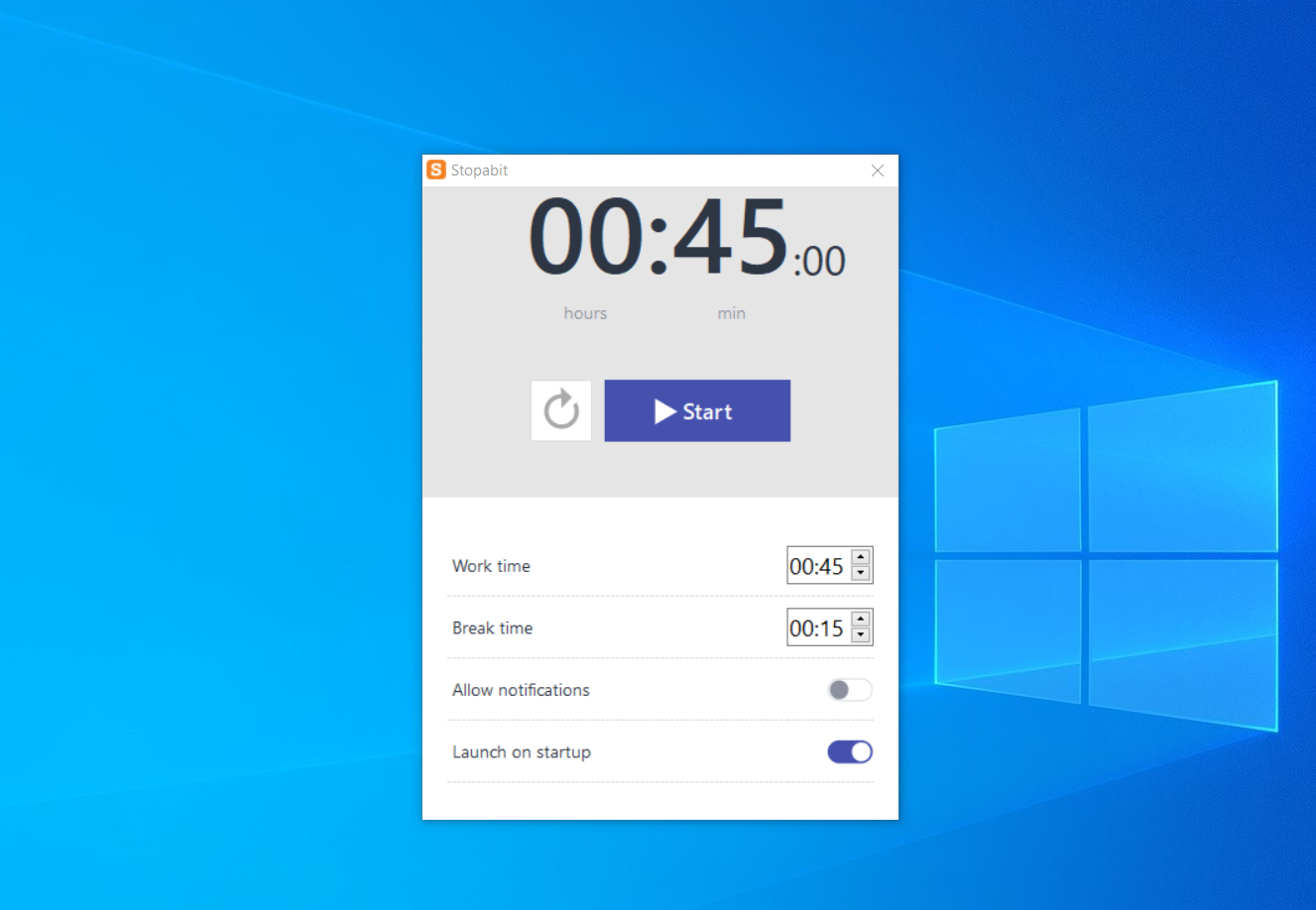
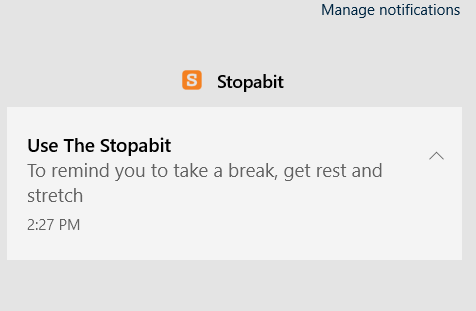
To understand how Stopabit works, let’s go through each step of its actions by analyzing one of its samples. Immediately after the installation, it sends the notification to the tray, offering to start using the tool.
The interface of the program is pretty ascetic, to say the least. There is only one panel with possible actions; the rest of things that are available from the tray are just EULA, some basic settings and program info. Thing is – all these functions are already present in Windows, as a part of the Focus app.
And well, the main course of Stopabit is its proxyware module. It starts together with the program, and appears to have its own persistence settings. Even when you stop the program from the tray, the corresponding process in the Task Manager keeps running. This means proxy connections will keep operating until you remove the program completely.

System Reconnaissance
Stopabit tries to gather detailed information about the system by interacting with the Windows Registry, querying running processes, and reading various system configuration settings. It also tries to get information on the installed software, including software policies and cryptographic machine GUID, the OS version, system information, query environment variables, and get the disk size, system language, geographical location, and time zone information.
HKCU\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ICM\RegisteredProfiles
HKCU\Software\Classes\Local
HKCU\Software\Classes\Local Settings\MuiCache\1F4\52C64B7E\LanguageList
The registry keys include interface and language preferences, application settings, internet connection, session and recovery details, installed applications, internet settings, security certificates, Windows settings, registry values, and security policies.
It also tries to detect virtual machines to hinder analysis by this value
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ICM\RegisteredProfiles
This registry key is related to color management in Windows. The malware understands whether it is in a virtualized environment depending on the response received.
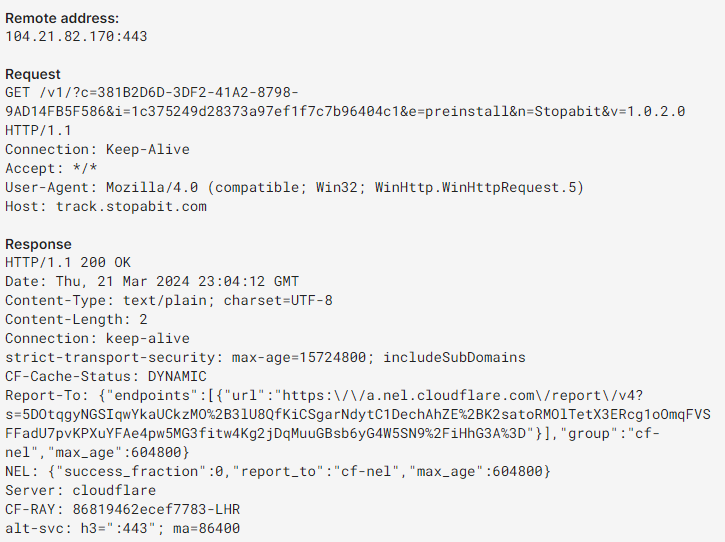
C2 connection
The malware uses secure web protocols (HTTPS) to communicate with its command and control server. This makes detecting malicious traffic an exceptionally hard task, as this blocks the ability to detect it by specific parts. It also transmits data using the following non-standard ports – another anti-detect and anti-sniff feature. All the possible C2 servers are hardcoded into the sample, probably during the compilation.
track.stopabit.com/v1/?c=381B2D6D-3DF2-41A2-8798-9AD14FB5F586&i=ba6361541ad79f7d5bb94c8f8cec972d&e=preinstall&n=Stopabit&v=1.0.2.0
128.140.126.44:32069 (UDP)
a83f:8110:0:0:1400:1400:2800:3800:53 (UDP)
a83f:8110:2800:0:2800:0:1800:0:53 (UDP)
How To Remove Stopabit?
Removing Stopabit almost mandatory involves using anti-malware software. GridinSoft Anti-Malware is a great solution to remove Stopabit and other malware in a few clicks. Manual removal is barely possible, since this application creates numerous backup copies around the disk, that will restore the threat back. This tool will find and delete them all at once.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.