Over the last four years, the share of script-based attacks of malware offenses worldwide has grown so drastically that it raised alerts among security specialists and ordinary users. In this post, we shall regard script-based malware, assess its strengths and weaknesses, explain how the attacks happen, and suggest measures to maintain security in your workgroup.
What is Script Malicious Code?
To understand how someone can run a script-based attack on a computer, we must know what scripts are. They are sets of commands for a system to execute. Users employ them to automatize processes that they would otherwise perform manually. Programmers and advanced users create scripts in scripting languages. Those can be, roughly speaking, general-purpose (such as JavaScript, Python, and PHP), OS-oriented (like PowerShell and AppleScript), and there are also special script languages for particular applications and environments.
The scripts are neither malicious files nor the main content of the files they inhabit. Instead, they are the documents’ allowable components, legal and, in theory, beneficial to the user. Scripts are not compiled. That means they are interpreted and executed by the software environment ad hoc without previous translation into machine code. For AppleScript, for example, such an environment is an Apple operating system. And for cross-system JavaScript (if it is about website construction), any modern web browser can serve as an interpreting environment.
The script-based hacker attacks are cyber crimes that use scripts as a primary tool.
Malware Script Examples
Cross-Site Scripting (XSS) Attacks
XSS (Cross-Site Scripting) attacks can result in data theft, session hijacking, and unauthorized access to confidential information. They also jeopardize user trust, damage the reputation of web applications, and may lead to legal repercussions under data privacy regulations like GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act).
<p>User's comment: <script>alert('Malicious Script')</script></p>
<!-- This user input is not properly sanitized -->
<p>User's comment: <?php echo $_GET['comment']; ?></p>
Consider a website that allows users to submit their own content or post comments. In this scenario, an attacker has posted a comment containing a script tagged as “Malicious Script.” This script was displayed directly without proper sanitation or encoding, leading it to execute in other users’ browsers when viewed. As a result, any user reading the comment would see a pop-up saying Malicious Script, illustrating how attackers can execute scripts in the browsers of unsuspecting users. This highlights a serious vulnerability: the script used in the attack could be modified to execute more complex commands that could potentially steal user data directly from their browser.
XML External Entity (XXE) Vulnerability
XXE, or XML External Entity attack, exploits vulnerabilities in applications that parse XML files. This issue arises when an application’s XML parser improperly configures security settings, allowing it to dereference external entities within the XML file. During parsing, if the application processes these entities, it could unintentionally leak sensitive data, disrupt services, perform unauthorized actions on the server, or access other parts of the system.
import xml.etree.ElementTree as ET
xml_data = """
<!DOCTYPE data [
<!ENTITY xxe SYSTEM "file:///etc/passwd">
]>
<data>&xxe;</data>
"""
root = ET.fromstring(xml_data)
When the Python script runs and processes the XML document with the ElementTree library, it attempts to access the /etc/passwd file.
SQL Injection
SQL injection is a prevalent cybersecurity risk where attackers can alter a web application’s database by inserting harmful SQL code into its input fields. These fields can include any data entry areas on a website, like web forms or URLs. When successful, SQL injection attacks allow attackers to access and manipulate databases, which could lead to the exposure of sensitive information.
user_input = input("Enter your username: ")
sql_query = "SELECT * FROM users WHERE username = '" + user_input + "'"
cursor.execute(sql_query)
In this scenario, user input is directly incorporated into the SQL query string. If an attacker provides harmful input, they might alter the SQL query, potentially obtaining unauthorized access to the database.
What is so worrying about script-based attacks?
First of all, scripts are not files, as we already mentioned. Antivirus programs have a hard time detecting them, or better to say: they are useless against scripts. It is so because modern security software focuses on detecting and removing malicious files. Thus, in the case of script-based attacks, we are dealing with ghostly malware, invisible to antivirus programs.
Another important thing is that scripts are generally hard to detect. They exist in primary memory, soon to be overwritten or erased. It is possible to find the origin of a script if criminals inaccurately leave traces, but why would they do that?
How can an attacker execute malware through a script?
Let’s make it clear: we are not talking about malicious scripts tied to websites (Cross-Site Scripting), which are more or less studied and covered by browser and antivirus security systems. Files fitted with simple yet treacherous scripts constitute a new problem. These are the files whose formats antivirus software lets through by default, not regarded as dangerous: PDF, Word, e-books, HTML applications, and others.
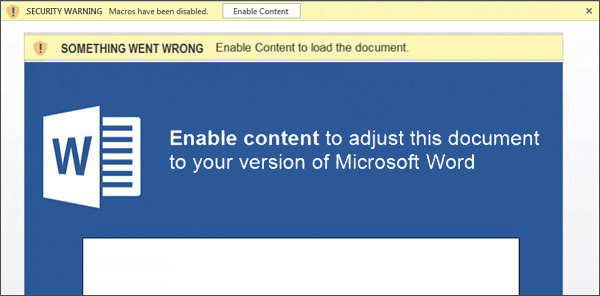
Simple JavaScript code usually employed in files like these can add various practical functions, like making PDF documents signable or featuring a fillable questionnaire. But the script can have a malicious purpose as well. In case of a script-based attack, it most likely will be a set of commands to download any other malware that harms for real. Ransomware, for instance, is the most lucrative type of attack for hackers. The crooks only expect a user to open a file to run the script or, in some cases, to allow macros therefor.
Script-stuffed files can also be downloaded items you are trusty about since they update programs you already have. At least, you believe so. These can be plug-ins, add-ons, and so on. Yes, the UAC will ask whether you want to download this file, but this always happens, and we tend to ignore such warnings. If the criminals manage to cheat you – consider they also cheated your security software. By the way, various untrustworthy PDF-readers and their plug-ins are some of the most dangerous programs in terms of script-based attack menace.
The script-based attacks mostly endanger Windows systems by exploiting vulnerabilities of Command Prompt and PowerShell, the in-built automation tools. However, neither Android, iOS nor even Linux is safe.
How to protect yourself and your workgroup?
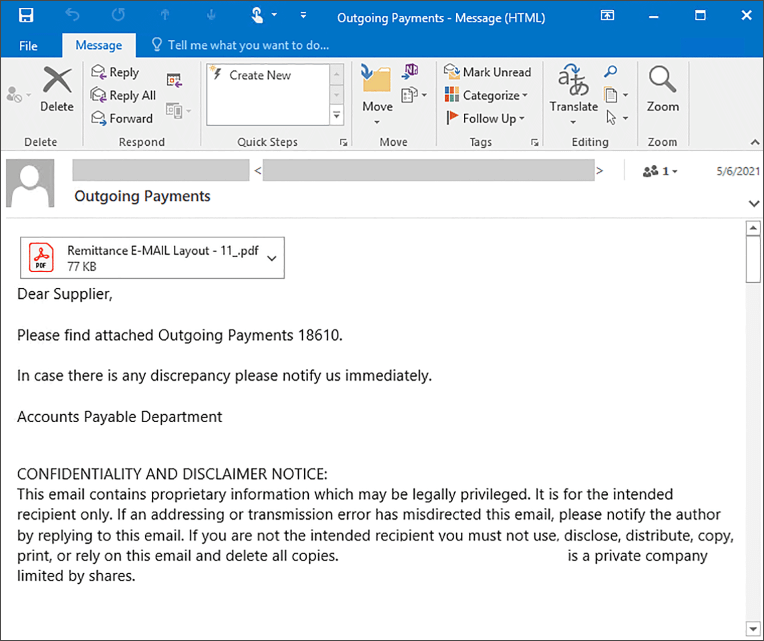
The weakness of script-based malware is that it has to be run by the user. Therefore, the best protection is to be cautious and avoid unknown downloads. Remember that PDF, Word, and other data files can contain a malicious script. These bogus files are most likely to arrive via e-mail or messengers in letters sent seemingly by someone you trust – usually services-providing organizations. Be especially wary of reports from delivery companies like FedEx. Since a postal delivery is pretty believable to be unexpected, hackers often use this disguise for their phishing mail. Before downloading any attachments from suspicious senders, triple-check the source and the message itself. If you are attentive enough, you will find a mistake in the address line, your name, or the text itself.
In workgroups, it makes sense to separate those computers that need to run scripts from those that can do without them. The former should maintain extreme vigilance and advisably deploy zero-trust policy antivirus software, which is for the moment presented by Windows 11 Defender. It has many issues, but it seriously jeopardizes the plans of malefactors who go in for script-based attacks.
Script-fitted files can spread rapidly via the injured network using the same vulnerabilities of Windows elements they use to deliver their malicious payload. General security measures, such as file backup and network separation, are also a must to minimize the destructive effect of any successful cyber-attack.
How to detect script-based malware?

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.